A new variant of the Mirai malware botnet has been detected, infecting low-cost Android TV set-top boxes. They are extensively used for media streaming by millions of people. The present Trojan is a fresh edition of the ‘Pandora’ backdoor initially identified in 2015, per the analytics.
The campaign targets low-cost Android TV boxes such as Tanix TX6, MX10 Pro 6K, and H96 MAX X3. These devices have quad-core processors that can launch powerful DDoS attacks, even in small swarm sizes.
Mirai Botnet Aims Android-based TV Boxes
Mirai Botnet can infect devices via malicious firmware updates signed with publicly available test keys or malicious apps. Which undoubtedly distributed on domains that target users interested in pirated content. In the first case, firmware updates are either installed by resellers of the devices or users are tricked into downloading them from websites. Then, they promise unrestricted media streaming or better application compatibility.
The ‘boot.img‘ file contains the kernel and ramdisk components loaded during Android boot-up. It makes it an excellent persistence mechanism for the malicious service.
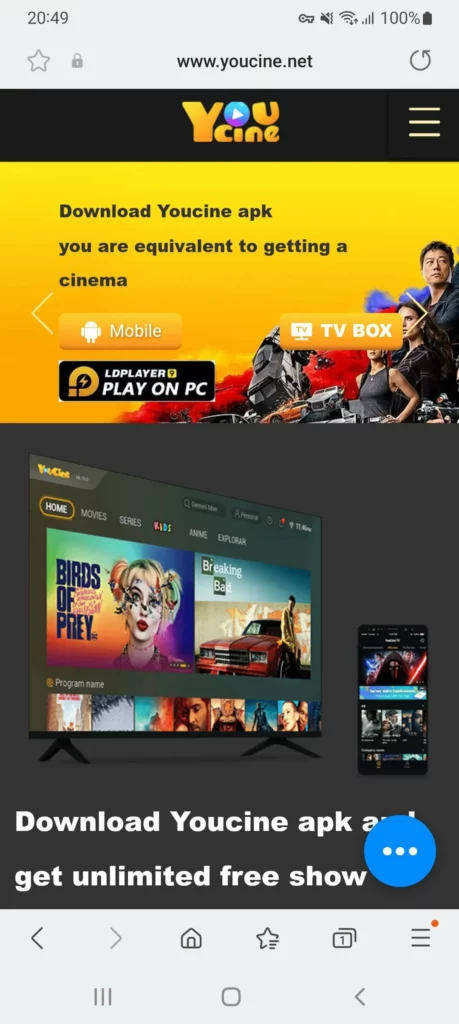
The second distribution channel involves the use of pirated content apps. They also offer access to collections of copyrighted TV shows and movies for free or at a low cost. Security experts have identified Android apps that spread the new Mirai malware variant to infected devices. Here is an example:
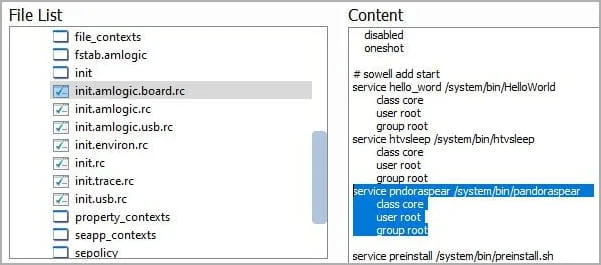
In this case, the malicious apps surreptitiously start the ‘GoMediaService‘ during the initial launch and set it to auto-start when the device boots up.
When the ‘gomediad.so‘ service is called, it unpacks multiple files, including a command-line interpreter that runs with elevated privileges (‘Tool.AppProcessShell.1‘) and an installer for the Pandora backdoor (‘.tmp.sh‘).
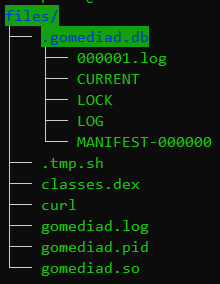
After being activated, the backdoor establishes communication with the C2 server, and replaces the HOSTS file. After that, it updates itself and then enters standby mode, waiting for instructions from its operators. The malware can launch DDoS attacks using the TCP and UDP protocols, such as generating SYN, ICMP, and DNS flood requests. It can also open a reverse shell, mount system partitions for modification, and perform other functionalities.
IoC Mirai Botnet
- Malware.U.Mirai.tr: 96b087abf05bb6c2c1dd6a1c9da460d57564cc66473ca011f85971752a112ce1
- Malware.U.Mirai.bot: 624f4966636968f487627b6c0f047e25b870c69040d3fb7c5fb4b79771931830
- Malware.U.Mirai.bot: 613f03b52910acb8e25491ca0bfe7d27065221c180e25d16e7457e4647a73291
- Malware.U.Mirai.bot: 22f269a866c96f1eec488b0b3aebe9f8024ae455255a4062e6a5e031dfd16533
What devices are at risk?
Budget-friendly Android TV boxes often have an uncertain journey from manufacturer to consumer. It leaves the end-user unaware of their origins, potential firmware modifications, and the various hands they’ve been through.
Even cautious consumers who retain the original ROM and are selective about app installations face a lingering risk of preloaded malware on their devices. It is advisable to opt for streaming devices from trusted brands like Google Chromecast, Apple TV, NVIDIA Shield, Amazon Fire TV, and Roku Stick.
Safety recommendations
For Android TV users, installing apps only from the official app store is advisable. It is also essential to pay attention to the permissions requested by the app. If your app requests access to your phonebook and geo-location, it is best to avoid using it as it could be malware. Additionally, it is crucial not to download or install any hacked apps, as their contents are often infected with malware of some kind.