Virus:Win32/Floxif.H is a detection of a malicious program, though not a virus as you may suppose by its name. Malware like Floxif aims at delivering and install additional malicious payloads onto compromised systems.
This malware uses different tactics to evade detection, such as compression and file replacement, also employing anti-analysis tricks. It is spread through software hacking tools and malicious adverts.
Virus:Win32/Floxif.H Overview
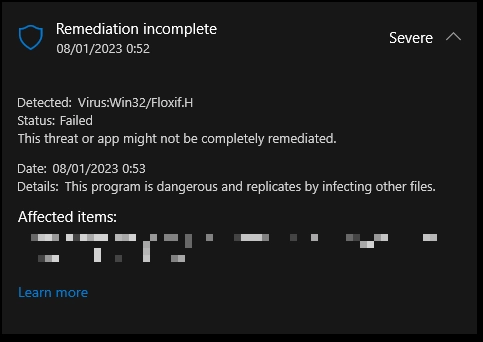
Virus:Win32/Floxif.H is a detection by Microsoft Defender that points to malware active in the system. In this case, we are talking about a dropper—malware designed to install another malware (such as stealers and ransomware) onto a computer. While the dropper may seem harmless at first glance, the payload it can bring is not.
One common infection vector is pirated software, files, and programs from P2P networks, third-party downloaders, shady pages, etc. This method is ideal for spreading malware because it often involves disabling security software during installation. However, in addition to the security risk, pirated software is illegal. In other cases, users infect computers via malicious advertisements and fake software updates. Due to the weak moderation of search ads, this method is quite popular among scammers.
Among the most troubling aspects of Virus:Win32/Floxif.H is its adeptness at evading detection mechanisms. It systematically eliminates original files and replaces them with encrypted and compressed versions. This trick effectively obscures its presence, making it challenging for traditional antivirus software to identify and neutralize.
Technical Analysis
Let’s examine how Virus:Win32/Floxif.H behaves using a single instance. Once inside, the malware leverages commands and scripting interpreters, such as accepting command line arguments. Additionally, it might utilize shared modules to link functions at runtime on Windows. Upon execution, the thing performs a couple of checks, primarily to determine the system location.
HKEY_CURRENT_USER\Software\Microsoft\RAS Phonebook\AreaCodes
Persistence
The malware establishes persistence mechanisms to ensure it remains active across system reboots. This involves creating undocumented autostart registry keys or other methods to maintain their presence in the system. Attackers can use these AppInit_DLLs keys to load their DLL files into every process on the system.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\LoadAppInit_DLLs
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\RequireSignedAppInit_DLLs
Virus:Win32/Floxif.H Privilege Escalation
Floxif increases the permissions of its own process through the command to the SubInACL utility. The command below specifically contains the ”=f” ending, which is an argument for the “full control” permissions.
(open) C:\subinacl.exe/subdirectories %SAMPLEPATH%" /grant=s-1-1-0=f" [(null)]
After that, the malware requests permissions that allow it to have a comprehensive control over the system. The last privilege from the list is the most worrying, as it effectively allows the threat to manipulate the drivers. Such manipulation is commonly used to introduce highly-persistent malware.
SE_DEBUG_PRIVILEGE – gets the ability to debug any process in the system
SE_INC_BASE_PRIORITY_PRIVILEGE – allows for changing the process’ execution priority
SE_LOAD_DRIVER_PRIVILEGE – the ability to control (load and unload) the drivers
Virus:Win32/Floxif.H Payload Delivery
Following gaining the privileges, Floxif drops the payload into the target system. It connects to a remote server (one from the list built into each sample), pulls the payload and saves it to one of the legitimate folders. Usually, it opts for a folder in the C:\Program Files\ or C:\Program Files (x86):
C:\Program Files (x86)\Google\Update\1.3.33.17\goopdate.dll.tmp
C:\Program Files\Common Files\System\symsrv.dll
C:\Program Files\Common Files\System\symsrv.dll.000
C:\ProgramData\Microsoft\Network\Connections\Pbk\rasphone.pbk
The said files are further launched and granted with higher privileges. Original malware does the same trick to the threats it loads as it did for itself.
C:\Windows\System32\wuapihost.exe -Embedding
(open) C:\subinacl.exe/subdirectories C:\Documents and Settings\All Users\Application Data\Microsoft\Network\Connections\Pbk\rasphone.pbk" /grant=s-1-1-0=f" [(null)]
Defense Evasion
The malware employs tactics to avoid detection and analysis. This includes sample packing, encryption and obfuscation, which are rather typical for modern malware. What is less typical is the continuous cleanups Floxif does after the first stage of its activity.
cmd.exe /c del /F /Q "C:\Documents and Settings\Administrator\Local Settings\Temp\EB93A6\996E.exe.dat"
cmd.exe /c del /F /Q "C:\Program Files (x86)\Google\Update\1.3.33.17\goopdate.dll.dat"
cmd.exe /c rd /S /Q "C:\Documents and Settings\Administrator\Local Settings\Temp\EB93A6\996E.exe.dat"
cmd.exe /c rd /S /Q "C:\Program Files (x86)\Google\Update\1.3.33.17\goopdate.dll.dat"
The commands from above serve for deleting the files the malware has dropped earlier in the execution process. Without them, it will be much harder for anti-malware software to trace the infection.
How To Remove Virus:Win32/Floxif.H?
To remove the Virus:Win32/Floxif.H malware from your system, I highly recommend using GridinSoft Anti-Malware.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.