URL:Blacklist is a security detection used by Avast and AVG antivirus programs to flag potentially dangerous websites. This warning typically appears after clicking a link, advertisement, or sometimes immediately upon opening your browser. While this protective feature helps shield users from various online threats, it can also trigger false positives on legitimate websites. This comprehensive guide explains everything you need to know about URL:Blacklist detection, how to interpret these warnings, and what steps to take when they appear.
What is URL:Blacklist Detection?
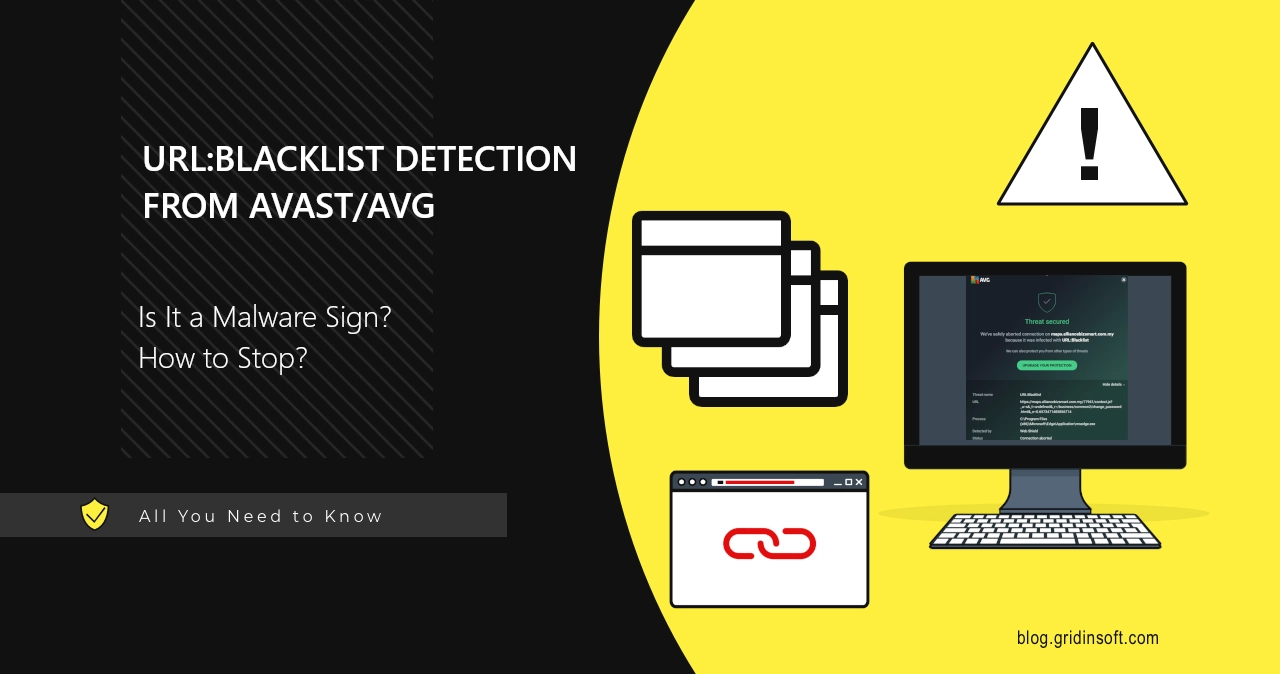
URL:Blacklist is a detection generated by the network security engine integrated into Avast and AVG antivirus solutions. This protection feature is enabled by default and actively monitors all outgoing connections from your device, blocking those deemed potentially harmful. When you attempt to visit a website that the security engine identifies as suspicious or dangerous, you’ll receive a URL:Blacklist warning alerting you to the potential risk.
One significant limitation of this detection is its lack of specificity. Unlike some security alerts that provide detailed information about the exact nature of the threat, URL:Blacklist warnings typically offer minimal context about why a particular site was flagged. This ambiguity can leave users confused about the severity of the risk and whether it’s safe to proceed.
It’s important to understand that URL:Blacklist doesn’t always indicate malware activity, though this can certainly be one reason for the alert. These warnings can be triggered by various types of suspicious or potentially harmful websites, ranging from online scams and phishing attempts to legitimate sites that have been compromised to distribute malware.
When you encounter a URL:Blacklist warning and need more specific information about the potential threat, we recommend using a free online website checker to perform a more detailed analysis of the flagged URL.
Types of Websites That Trigger URL:Blacklist Warnings
Various types of websites can trigger URL:Blacklist warnings. Understanding these categories can help you better interpret what these alerts might be trying to protect you from:
| Blacklist Type | Description | Example |
|---|---|---|
| Phishing site | Probably, the most widely known type of online scam is phishing. Such websites usually mimic a login page of a well-known site, such as Microsoft, Amazon, eBay, or online banking web pages. They contain a script that allows hackers to extract the input (i.e. login credentials) | kuex bet |
| Fake online shopping site | Another widely known case is the shopping website that takes an order but never delivers one. It may offer astonishing discounts, selling items worth several hundred dollars for just a nickel. A user trying to get the desired thing almost for free will happily pay, but only to discover that the order is never about to be delivered | Soolinen |
| Cryptocurrency scam | Rising popularity of cryptocurrencies made a lot of inexperienced people try getting into this topic. Scammers take advantage of this, offering the sites they established yesterday to trade crypto, participate in airdrops, or create a hot wallet. Further, they steal any info and money that gets into these sites. One particular specimen of cryptocurrency scams is so-called crypto drainers, which empty the hot wallet once the user connects one to the scam site | exnori |
| Fake raffle prizes | A rather old kind of scam site that encourages people to share their personal information by offering sweet rewards. The latest iPhone, new Samsung smartphone, or $1000 gift card just for sharing personal information sounds great. However, all this will never get to the “winner”, as it did not even exist. The only thing such scams aim for is users’ personal information | 1xbetwinprizes |
| Fake job offerings | This type of scam is particularly new but works with the same intent as the previous one. Frauds lure people with a job offer, typically going for ones who seek a remote job. After contacting the victim, they say the victim should send them the entirety of their documents, including SSN and ITIN. On top of that, there is a need to pay a small (~$100) fee to cover the paper job expenses. Then, scammers simply cut the conversation | clickjob work |
Below, you can see examples of dangerous websites that have triggered URL:Blacklist warnings, analyzed with online scanning tools. These examples demonstrate different types of threats and show how even seemingly legitimate sites can pose significant risks.
| URL | Threat Type | Full Report |
|---|---|---|
| D1b2hzwettncwz.cloudfront.net | Malware distribution | Scan Result |
| A2zapk.com | Phishing | Scan Result |
| Bloomsbody.com | Fake Online Shop | Scan Result |
Examining these examples reveals certain patterns. Sometimes, the URL itself offers clues about a website’s legitimacy, as dangerous pages often use unfamiliar domains with seemingly random characters. However, this isn’t always a reliable indicator, as many scam websites—particularly those designed for shopping fraud—often use clear, believable domain names designed to appear legitimate at first glance.
Understanding False Positive Detections
While URL:Blacklist detection helps protect users from genuine threats, the system is not perfect. There are numerous reported cases where URL:Blacklist incorrectly flags legitimate and safe websites[1], [2]. These false positives can occur for various reasons, usually related to the detection mechanisms employed by the antivirus software.
Based on user reports from various forums, certain types of legitimate websites seem particularly prone to triggering false URL:Blacklist warnings:
- File-sharing services: Platforms that allow users to share files, even legitimate ones, may be flagged due to their potential for distributing malicious content.
- Cryptocurrency mining pools: Crypto mining pools are often flagged because some malware uses similar connections for cryptocurrency mining without user consent.
- Newly created websites: Recently launched websites may lack sufficient reputation history to be considered trustworthy by security databases.
- Less popular but legitimate websites: Sites with lower traffic volumes may not have established sufficient trust signals for security algorithms.
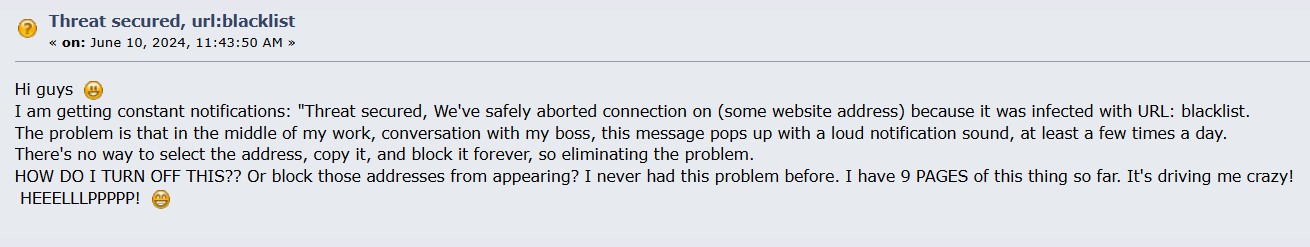
While the caution exercised by Avast and AVG is understandable, these false positives can be frustrating, especially when they block access to websites you know to be safe and need to use regularly.
How to Handle URL:Blacklist False Positives
If you encounter a URL:Blacklist warning for a website you know to be safe, you have several options:
Option 1: Add the Website to Exceptions (Recommended)
For users who want to maintain the protection of Avast/AVG’s web shield while allowing access to specific trusted sites, adding the website to your exceptions list is the recommended approach:
- Open Avast or AVG antivirus software
- Navigate to Settings → General
- Find the Exceptions tab
- Click the Add Exception button
- Paste the URL of the website you want to allow
- Click Add Exception to confirm
This method allows you to maintain protection against genuinely dangerous sites while preventing false positives for specific trusted websites.
Option 2: Disable Web Shield Protection
If you find the URL:Blacklist feature too restrictive or encounter frequent false positives, you can disable the Web Shield component entirely. Note that this will reduce your protection against malicious websites:
- Open Avast or AVG antivirus
- Go to Settings → Protection → Core Shield
- Select the Web Shield tab in the top navigation
- Uncheck all options to disable web protection
- Restart your computer to apply the changes
Before disabling this protection, consider whether the convenience outweighs the potential security risks. If you choose to disable Web Shield, it’s advisable to exercise additional caution when browsing and consider using alternative web protection tools.
When URL:Blacklist Warnings Indicate Malware Infection
While many URL:Blacklist warnings occur when you deliberately try to visit a website, a particularly concerning scenario is when these alerts appear frequently and seemingly at random, regardless of what websites you’re trying to access. If you notice URL:Blacklist warnings appearing constantly during your normal browsing activities, this could indicate a malware infection on your system.
Several types of malware can trigger these persistent URL:Blacklist warnings by attempting to connect to malicious servers in the background:
- Adware: Less severe but annoying malware that displays unwanted advertisements and may redirect your browser to promotional websites.
- Browser Hijackers: Malware that modifies browser settings to redirect searches and visits to specific websites without user consent.
- Backdoors: More dangerous malware that provides attackers with remote access to your system, often attempting to communicate with command and control servers.
- Loaders: Malicious programs designed to download and install additional malware from remote servers.
The last two categories pose significant security risks and should not be ignored. If you suspect a malware infection is causing URL:Blacklist warnings, performing a thorough system scan with specialized anti-malware software is strongly recommended. For effective detection and removal of these threats, GridinSoft Anti-Malware is an excellent choice, as it’s designed to identify and eliminate threats that other antivirus solutions might miss.
How to Remove Malware Causing URL:Blacklist Warnings
If you’re experiencing persistent URL:Blacklist warnings that suggest a malware infection, follow these steps to scan and clean your system:

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Frequently Asked Questions
Is it safe to ignore URL:Blacklist warnings?
Generally, it’s not advisable to ignore URL:Blacklist warnings, as they often indicate genuine security threats. These warnings are designed to protect you from websites that could steal personal information, distribute malware, or scam you financially. However, if you’re absolutely certain that the flagged website is legitimate (for example, it’s a well-established site you’ve used safely for years), you can add it to your antivirus exceptions list rather than bypassing the warning each time. If you’re experiencing frequent warnings without actively trying to visit new websites, this could indicate a malware infection that requires immediate attention.
Why does AVG/Avast flag websites that other antivirus programs don’t?
Avast and AVG (which are now owned by the same company) may flag websites that other antivirus programs don’t because they use different detection algorithms and threat intelligence databases. Their Web Shield feature employs a more aggressive approach to web protection compared to some competitors. This can result in better protection against emerging threats, but it also increases the likelihood of false positives. Additionally, Avast/AVG updates their URL blacklist database frequently, sometimes detecting suspicious websites before other security solutions. If you believe a website has been incorrectly flagged, you can report the false positive to Avast/AVG for review, or add the site to your exceptions list if you’re confident it’s safe.
How often is the URL:Blacklist database updated?
The URL:Blacklist database used by Avast and AVG is updated continuously throughout the day. The companies maintain a cloud-based threat intelligence network that collects and analyzes data from millions of users worldwide, allowing them to identify and add new malicious URLs to their database in near real-time. This frequent updating is necessary to keep pace with the rapidly evolving landscape of online threats, as new malicious websites are created daily while previously compromised sites may be cleaned and removed from the blacklist. The database receives both automated updates based on threat detection algorithms and manual verification by security analysts who investigate potential threats.
Can URL:Blacklist warnings appear on mobile devices?
Yes, URL:Blacklist warnings can appear on mobile devices that have Avast or AVG security applications installed. The mobile versions of these security solutions include similar web protection features to their desktop counterparts, monitoring web traffic and blocking access to potentially harmful websites. On Android devices, the protection works across different browsers through the security app’s web shield component. On iOS, due to platform restrictions, the protection typically works through a secure browser provided by the security application. If you encounter these warnings frequently on your mobile device without actively browsing to new websites, it could indicate adware or other malicious apps that are attempting to connect to suspicious servers in the background.
Does URL:Blacklist only check the domain or the entire URL?
URL:Blacklist checks both domain-level and full URL path information when evaluating potential threats. While many blacklisting systems primarily focus on domain names, modern web security solutions like Avast and AVG’s URL:Blacklist implement more sophisticated scanning that considers the complete URL, including specific pages and parameters. This approach provides more comprehensive protection, as it can identify specific malicious pages within otherwise legitimate domains that have been compromised. For example, a legitimate website might have a specific page that has been infected with malware or set up for phishing, while the main domain remains safe. The granular scanning also helps reduce false positives by potentially allowing access to safe sections of partially compromised websites.