A group of hackers, presumably state-sponsored, is actively developing and beginning to use a sophisticated Decoy Dog toolkit. It has likely been used for over a year in cyber intelligence operations. It utilizes the Domain Name System (DNS) to manage and control a narrowly focused and minimal number of active clients.
What is Decoy Dog Malware?
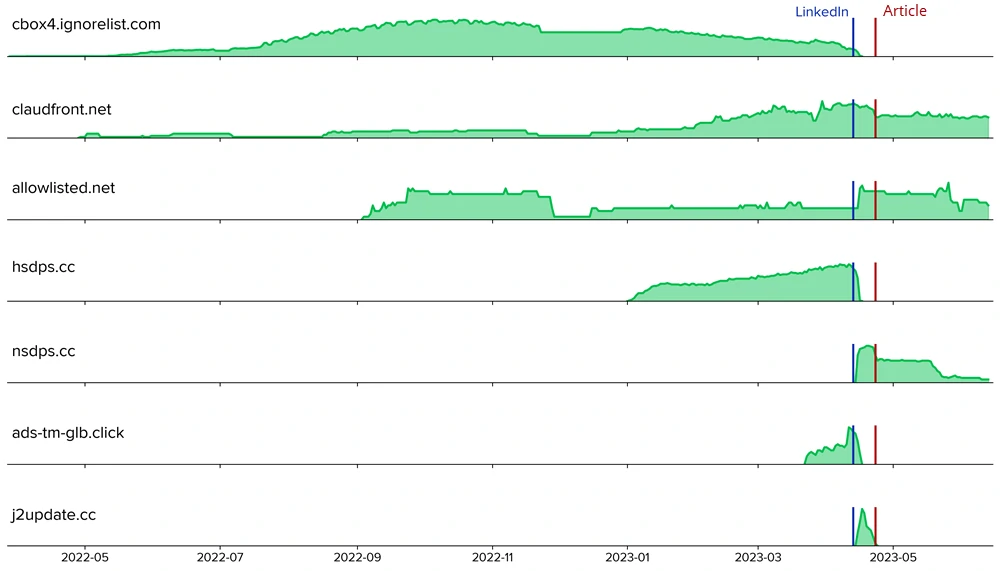
In April, Researchers discovered Decoy Dog, a remote access trojan (RAT) toolkit that uses DNS domains that act as command and control (C2) servers for the malware. It caused abnormal DNS signatures in enterprise networks across various regions, and some communications are being sent to a controller in Russia. Then researchers discovered DNS query patterns in enterprise networks that were not linked to consumer devices. They confirmed that the queries came from network appliances in only a few customer networks. Despite researchers announcement and technical analysis of this malware similarity to the Pupy open-source RAT, the toolkit’s operators continued their activity. At that time, had the following domains, which experts recommended organizations to block:
- claudfront[.]net
- allowlisted[.]net
- atlas-upd[.]com
- ads-tm-glb[.]click
- cbox4[.]ignorelist[.]com
- hsdps[.]cc
However, new research reveals that Decoy Dog significantly improves from Pupy, utilizing new domains, unique commands, and configurations that are not publicly available. Pupy is an open-source post-penetration remote access toolkit that emerged in 2015. Its primary purpose was serving a role of RAT in penetration testing simulations. The configs I mentioned as unavailable were hidden until 2019, and are related to the way malware resolves the C2 DNS. But even having the code, it was needed to perform a thorough name server setup for each malware run – which is a complicated task worthy of network engineers.
Decoy Dog Is a Better Pupy RAT
Researchers have been investigating the differences between Decoy Dog and Pupy since April. They set up their own C2 server for Pupy to analyze its DNS communication protocol. Thus, they could create DNS signatures to detect new controllers of this malware. Pupy and Decoy Dog both use nonces to identify sessions with clients and establish the ordering of messages. However, the subject uses the same query structure as Pupy. So, researchers decoded nonce values and correlated queries to the same compromised device.
Moreover, researchers could track each controller’s activity, including the sessions’ length and number of active clients. Unfortunately, encryption prevented researchers from seeing the specific data communicated, but they identified the types of messages sent and profiled the overall communication behavior of both clients. Decoy Dog responds to replays, while Pupy does not and has a richer set of commands and responses. The malware also exhibits more variance in message payload length than Pupy.
From this, researchers confirmed that Decoy Dog is a major refactor of Pupy with advanced capabilities that have changed over time. It includes a domain generation algorithm and the ability for clients to execute arbitrary Java code. These features indicate sophistication and intentionality beyond many threat actors. Security vendor detectors still identify Decoy Dog as Pupy, possibly Since reverse engineers assumed the binary samples were identical.
Today’s activity
Decoy Dog’s creators quickly adjusted their system in response to its initial disclosure. Malware has expanded its reach, with at least three different actors now using it. Thus, they ensured uninterrupted operations and still access to previously compromised devices. Though based on the open-source RAT Pupy, researchers have identified Decoy Dog as a new and previously unknown form of malware with advanced features that allow it to persist on compromised machines. Today research shows how Decoy Dog significantly improved over Pupy. The former utilizes unique commands and configurations that are not publicly available. TAs use it in ongoing nation-state cyber-attacks through DNS to establish Command and Control.
While much about Decoy Dog remains unclear, specialists determined that the malware can only be detected through DNS threat detection algorithms. At least three threat actors have been identified using this malware based on the open-source remote access trojan called Pupy. However, significant changes to the code suggest the involvement of a sophisticated black hat. The security firm stated that the subject can respond to complex DNS requests that do not follow the typical communication structure. In addition, they specified that Pupy, which is associated with Decoy Dog, is a cover-up for the actual abilities of the program.
Threat Actors Use Decoy Dog for Precise Hacking
Based on the analysis of passive DNS traffic, analysts have difficulty determining the exact number of Data Dog targets and affected devices. However, the lowest and highest number of active concurrent connections detected by investigators on any one controller were 4 and 50, respectively. In addition, the number of compromised devices is less than a few hundred. This indicates a minimal target list, typical of a reconnaissance operation. In any case, experts suggest that well-secured and sophisticated attackers are using the malware.
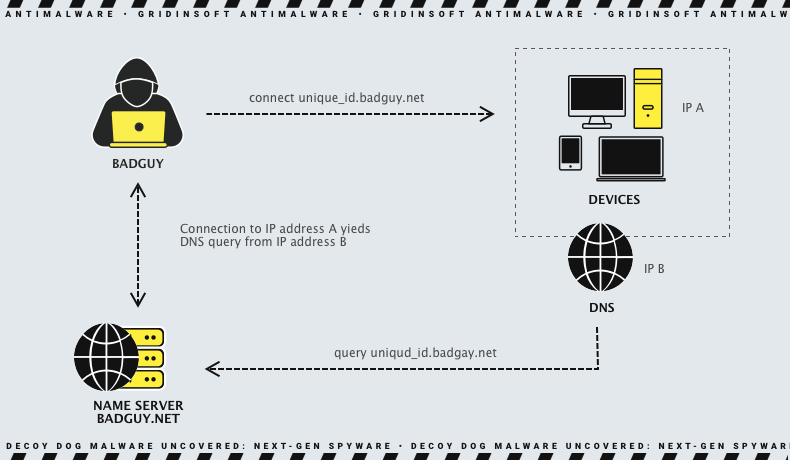
The attackers are likely targeting specific organizations with high information value. As mentioned above, there is a possibility that the victims are located in Russia. However, experts do not rule out that the attackers directed the victims’ traffic through this region as bait or to limit requests to relevant ones. Since it is quite difficult to change this system in modern networks, Decoy Dog behaves similarly to Pupy and uses the default recursive resolver to connect to DNS.
Safety recommendations
Security measures against Decoy Dog are generally similar to basic cyber security recommendations. However, there are key points to consider first. Here are some safety recommendations against this malware:
- Keep your software up to date. Auto-update should be enabled by default because it includes security patches that can help to protect your devices from malware.
- Use a firewall and antivirus software. A firewall can help to block unauthorized traffic from reaching your devices, and antivirus software can help to detect and remove malware.
- Be careful on the web. Look at what websites you visit and what links you click on. Decoy Dog can be spread through malicious websites and links.
- Use strong passwords and change them regularly. While this is a general recommendation, it is essential because strong passwords can protect your accounts from unauthorized access.
- Be aware of the signs of malware infection. Some symptoms include the computer running slowly, pop-ups and new programs appearing that you didn’t initiate, your browser settings changing, and files disappearing.
If you think your computer may be infected with Decoy Dog, contact your IT security team immediately. They will be able to help you to remove the malware and protect your organization from further attacks.
Web safety tips
Here are some additional tips to help you stay safe while web surfing:
- Use VPN when connecting to public Wi-Fi. This will help to protect your traffic from being intercepted by malicious actors.
- Be careful about what information you share online. Don’t share your personal information, such as your Social Security or credit card number, with websites or individuals you don’t trust.
- Please educate yourself about malware and how to protect yourself from it. Forewarned is forearmed. There is a lot of helpful, valuable information in the public domain today to help you keep up to date with the latest developments in cybersecurity.
By following these tips, you can help to protect yourself from Decoy Dog and other malware.




