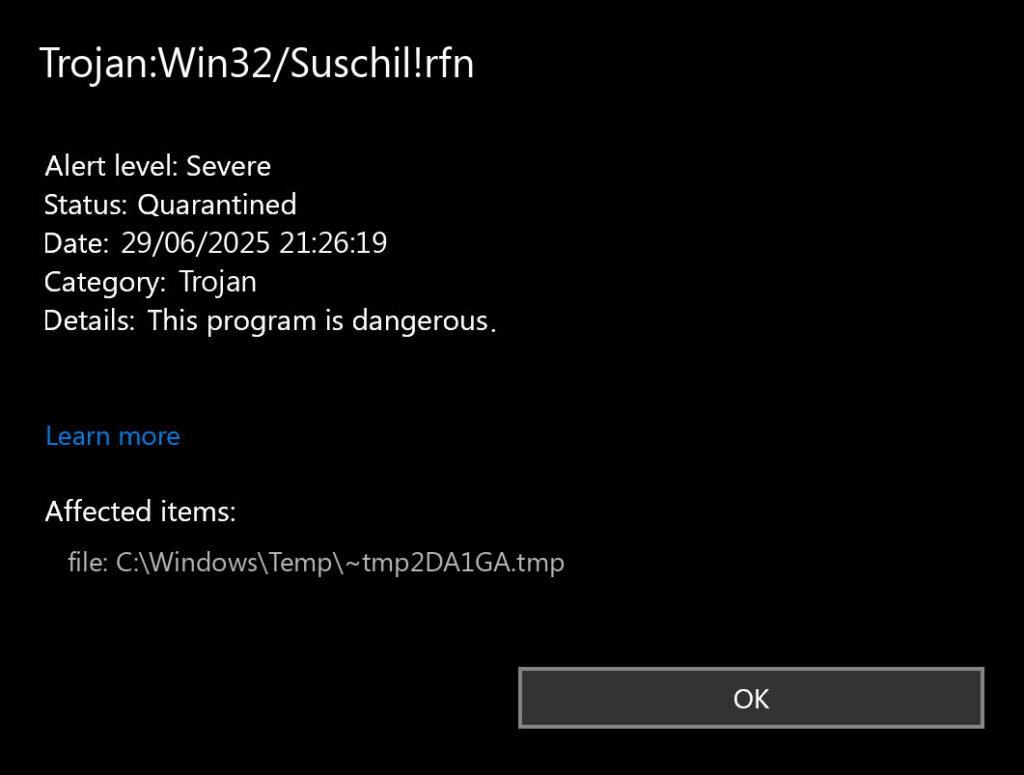
If you’re seeing Trojan:Win32/Suschil!rfn detected by your antivirus, don’t panic. Your computer might be running slower than usual. You might notice strange processes consuming system resources. Your browser might be acting up with unexpected redirects or pop-ups.
This guide will help you remove this threat completely. Follow these step-by-step instructions to eliminate the threat. We’ll start with manual methods you can try right now.
| Detection Name | Trojan:Win32/Suschil!rfn |
| Threat Type | Trojan Horse / Information Stealer |
| Threat Family | Suschil Trojan Family |
| Primary Function | Data theft, system compromise, backdoor access, credential harvesting |
| Target Platforms | Windows 7, Windows 8, Windows 10, Windows 11 |
| Common Sources | Cracked software, email attachments, malicious downloads, drive-by downloads |
| File Locations | %TEMP%, %APPDATA%, %LOCALAPPDATA%, %SYSTEM32% |
| Registry Keys | HKCU\Software\Microsoft\Windows\CurrentVersion\Run, HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Network Behavior | Connects to command and control servers, downloads additional payloads |
| Data Targets | Passwords, browser data, cryptocurrency wallets, banking information |
| Persistence Methods | Registry entries, scheduled tasks, startup folder modifications |
| Removal Difficulty | Moderate to High – Requires comprehensive cleanup |
| Risk Level | High – Can steal personal data and provide unauthorized system access |
| Impact Level | Severe – Identity theft, financial loss, system compromise |
What Is Trojan:Win32/Suschil!rfn?
Trojan:Win32/Suschil!rfn is a dangerous malware that targets Windows systems. It’s designed to steal your personal information. The malware can access your files, passwords, and browsing data.
This trojan often disguises itself as legitimate software. It might appear as a normal Windows process or application file. Once installed, it runs silently in the background.
The malware can open backdoors for hackers. This means criminals can access your computer remotely. They can install additional malware or steal sensitive data.
Similar to other trojan malware threats, Suschil!rfn uses social engineering tactics. It tricks users into downloading infected files. Common infection methods include cracked games, pirated software, and suspicious email attachments.
Signs Your Computer Is Infected
You might notice these symptoms if Trojan:Win32/Suschil!rfn has infected your system:
- Slow system performance – Your computer takes longer to start up and respond
- High CPU usage – Task Manager shows processes consuming excessive resources
- Unusual network activity – Unexpected data transfers or network connections
- Browser issues – Redirects to suspicious websites or unwanted pop-ups
- Antivirus alerts – Repeated detections of the same threat
- System crashes – Frequent blue screens or unexpected shutdowns
- Missing files – Important documents or programs disappear
These symptoms are common across many information stealing malware infections. If you notice multiple symptoms, immediate action is required.
Manual Removal Steps
Manual removal requires careful attention to detail. Follow each step exactly as described. Make sure to complete all steps to ensure complete removal.
Step 1: Disconnect from the Internet
Your first priority is cutting off the malware’s communication. Disconnect your computer from the internet immediately. This prevents the trojan from sending stolen data to hackers.
Unplug your ethernet cable or disable your Wi-Fi connection. This also stops the malware from downloading additional threats.
- Click the network icon in your system tray
- Select “Disconnect” for your current connection
- Alternatively, unplug your ethernet cable
Step 2: Boot into Safe Mode
Safe Mode loads Windows with minimal drivers and services. This makes it easier to identify and remove malicious processes.
- Press Windows key + R to open the Run dialog
- Type “msconfig” and press Enter
- Go to the Boot tab
- Check “Safe boot” and select “Minimal”
- Click OK and restart your computer
Your computer will boot into Safe Mode. The desktop will look different than usual. This is normal.
Step 3: Identify Malicious Processes
Open Task Manager to check for suspicious processes. Look for processes that you don’t recognize or that consume high CPU resources.
- Press Ctrl + Shift + Esc to open Task Manager
- Click the “Processes” tab
- Look for processes with suspicious names or high resource usage
- Right-click suspicious processes and select “End task”
- Note the process names and file locations
Be careful not to end legitimate Windows processes. If you’re unsure about a process, research it online before ending it.
Step 4: Delete Malicious Files
Now you need to locate and delete the actual malware files. Trojan:Win32/Suschil!rfn typically hides in these locations:
- Press Windows key + E to open File Explorer
- Enable “Show hidden files” in the View tab
- Navigate to these common malware locations:
Common file locations:
- C:\Users\[username]\AppData\Local\Temp
- C:\Users\[username]\AppData\Roaming
- C:\Windows\Temp
- C:\Windows\System32
- C:\Program Files
- C:\Program Files (x86)
Look for files with random names or suspicious extensions. Delete any files you identified in Step 3. Empty the Recycle Bin when finished.
Step 5: Clean Registry Entries
Trojans often modify Windows Registry to maintain persistence. You need to remove these entries manually.
- Press Windows key + R to open Run dialog
- Type “regedit” and press Enter
- Navigate to these registry locations:
Registry locations to check:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Look for entries with suspicious names or file paths. Right-click and delete any entries related to the malware.
Warning: Be extremely careful when editing the registry. Deleting wrong entries can damage your system. Only remove entries you’re certain are malicious.
Step 6: Check Scheduled Tasks
Malware often creates scheduled tasks to restart automatically. You need to find and remove these tasks.
- Press Windows key + R to open Run dialog
- Type “taskschd.msc” and press Enter
- Expand “Task Scheduler Library” in the left panel
- Look for tasks with suspicious names or unknown publishers
- Right-click suspicious tasks and select “Delete”
Pay attention to tasks that run at startup or have unusual triggers. These are likely malware-related.
Step 7: Clear Browser Data
Trojans often target browsers to steal login credentials and personal data. Clear all browser data to remove any traces.
- Open each browser you use (Chrome, Firefox, Edge)
- Access browser settings
- Find “Clear browsing data” or “Privacy” settings
- Select all data types and clear everything
- Restart your browser
This process is similar to dealing with heuristic virus infections that target browser data.
Step 8: Reset System Settings
Return your system to normal boot mode and verify the infection is gone.
- Press Windows key + R to open Run dialog
- Type “msconfig” and press Enter
- Go to the Boot tab
- Uncheck “Safe boot”
- Click OK and restart your computer
After restart, reconnect to the internet and run a full system scan with your antivirus software.
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of trojan threats. Professional anti-malware software can find hidden components and registry changes that you might miss.
GridinSoft Anti-Malware specializes in detecting sophisticated threats like Trojan:Win32/Suschil!rfn. The software uses advanced heuristic analysis to identify malware behavior patterns.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Browser Cleanup
Remove Malicious Browser Extensions
Trojans often install malicious browser extensions to monitor your online activities. These extensions can steal passwords and personal information.
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect browser-based compromise, reset your browser completely. This removes all extensions, settings, and stored data.
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
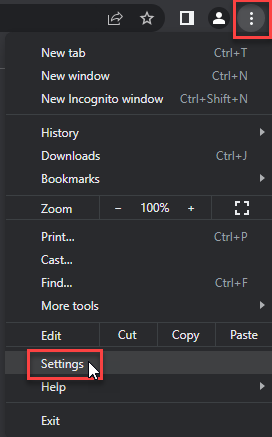
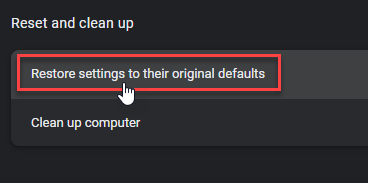
- Choose Reset and Clean up and Restore settings to their original defaults.
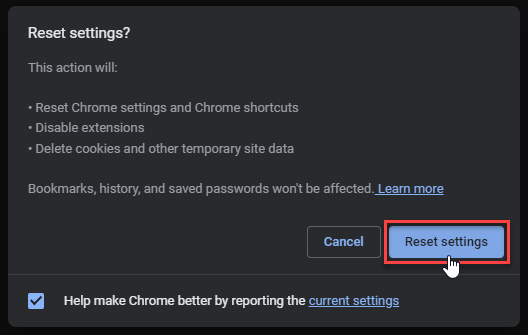
- Tap Reset settings.
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
- Choose More Troubleshooting Information.
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
How to Prevent Future Infections
Prevention is always better than removal. Follow these security practices to protect your system from future trojan infections.
Avoid Suspicious Downloads
Never download software from untrusted sources. Stick to official websites and verified download platforms. Be especially careful with cracked games and pirated software, as these are common infection vectors.
Keep Your System Updated
Install Windows updates regularly. Security patches fix vulnerabilities that malware exploits. Enable automatic updates for critical security fixes.
Use Reliable Antivirus Software
Install reputable antivirus software with real-time protection. Keep virus definitions updated. Run regular system scans to catch threats early.
Be Cautious with Email Attachments
Never open attachments from unknown senders. Scan all attachments with antivirus software before opening. Be suspicious of unexpected attachments, even from known contacts.
Enable Windows Defender
Windows Defender provides basic protection against malware. Don’t disable Windows Defender unless you have a compelling reason and alternative protection.
Create System Backups
Regular backups protect your data if malware strikes. Use Windows Backup or third-party backup solutions. Store backups on external drives or cloud storage.
Frequently Asked Questions
What is Trojan:Win32/Suschil!rfn and why is it dangerous?
Trojan:Win32/Suschil!rfn is a malicious program that steals personal information and provides unauthorized access to your computer. It’s dangerous because it can steal passwords, financial data, and personal files. The trojan also creates backdoors for additional malware infections.
How did Trojan:Win32/Suschil!rfn get on my computer?
This trojan typically spreads through infected downloads, email attachments, or bundled software. Common sources include cracked software, pirated games, and suspicious email attachments. It might also come from visiting compromised websites or clicking malicious ads.
Can I remove Trojan:Win32/Suschil!rfn manually?
Yes, you can remove it manually by following the steps in this guide. However, manual removal requires technical knowledge and careful attention to detail. Missing any components can leave your system vulnerable. For complete removal, consider using professional anti-malware software.
Is it safe to delete processes related to Suschil!rfn?
Yes, it’s safe to delete malicious processes once you’ve identified them correctly. However, be careful not to end legitimate Windows processes. If you’re unsure about a process, research it online or use Task Manager’s “Properties” option to check file details.
How can I prevent Trojan:Win32/Suschil!rfn infections?
Avoid downloading software from untrusted sources, keep your system updated, use reliable antivirus software, and be cautious with email attachments. Regular system backups also help protect your data if infections occur.
What if manual removal doesn’t work?
If manual removal fails, the trojan might have deep system integration or rootkit capabilities. In such cases, professional anti-malware tools like GridinSoft Anti-Malware provide more comprehensive removal. These tools can detect hidden components that manual methods might miss.
Should I reinstall Windows after removing the trojan?
Complete Windows reinstallation isn’t usually necessary if you’ve successfully removed all malware components. However, if you’re concerned about system integrity or if the infection was severe, a clean Windows installation provides the highest level of security assurance.
Can this trojan come back after removal?
The trojan can return if you don’t eliminate all components or if the infection source remains active. This is why it’s important to follow all removal steps completely. Installing reliable antivirus software and practicing safe computing habits prevents reinfection.
Related Trojan Threats
Trojan:Win32/Suschil!rfn belongs to a family of similar threats. Understanding related malware helps you recognize and prevent future infections.
Trojan:Win32/Kepavll!rfn is another variant that targets Windows systems. It uses similar infection methods and poses comparable threats to your personal data.
Trojan:Win32/Wacatac represents a different type of trojan that focuses on cryptocurrency theft. These threats often work together to maximize damage.
Trojan:Win32/Leonem is known for its persistence mechanisms. It’s particularly difficult to remove manually due to its deep system integration.
Other related threats include Trojan:Win32/Yomal!rfn and Trojan:Win32/Vundo. These trojans share similar characteristics and require similar removal approaches.
System Recovery Tips
After removing the trojan, your system might need additional recovery steps. These tips help restore normal functionality.
Check System Performance
Monitor your system performance after removal. The trojan might have damaged system files or changed critical settings. Use Windows System File Checker to repair corrupted files:
- Open Command Prompt as administrator
- Type “sfc /scannow” and press Enter
- Wait for the scan to complete
- Restart your computer if prompted
Update All Software
Make sure all your software is up to date. Outdated programs can provide entry points for malware. Focus on these critical updates:
- Windows operating system updates
- Web browser updates
- Antivirus software updates
- Adobe Flash and Java updates
- Microsoft Office updates
Change All Passwords
The trojan might have stolen your passwords. Change all important passwords, including:
- Online banking and financial accounts
- Email account passwords
- Social media passwords
- Shopping and e-commerce sites
- Work-related accounts
Use strong, unique passwords for each account. Consider using a password manager to generate and store secure passwords.
Conclusion
Trojan:Win32/Suschil!rfn is a serious threat that requires immediate attention. This guide provides comprehensive manual removal steps and prevention strategies.
Remember that prevention is always better than removal. Practice safe computing habits, keep your system updated, and use reliable security software.
If manual removal seems too complex, don’t hesitate to use professional anti-malware tools. GridinSoft Anti-Malware provides automated detection and removal of threats like Suschil!rfn.
Stay vigilant and keep your system protected. Regular maintenance and security awareness are your best defenses against malware infections.





