If you’re seeing Trojan:Win32/Malgent!MSR detected by your antivirus, don’t panic. Your computer might be running slower than usual. You might notice strange processes eating up your system resources. Your antivirus keeps showing this detection and you’re not sure what to do.
This guide will help you remove this threat completely. Follow these step-by-step instructions to eliminate the threat. We’ll start with methods you can try right now, then move to more advanced techniques if needed.
| Detection Name | Trojan:Win32/Malgent!MSR |
| Threat Type | Backdoor Trojan |
| Primary Function | Provides remote access to criminals, delivers additional malware |
| Common Sources | Cracked software, fake system tools, pirated programs |
| Risk Level | High – Can steal data and install more malware |
What is Trojan:Win32/Malgent!MSR?
Trojan:Win32/Malgent!MSR is a backdoor that gives criminals remote access to your computer. The name “Malgent” stands for “Malicious Agent” because it works with other malicious programs. This threat usually comes bundled with fake software activators or cracked programs.
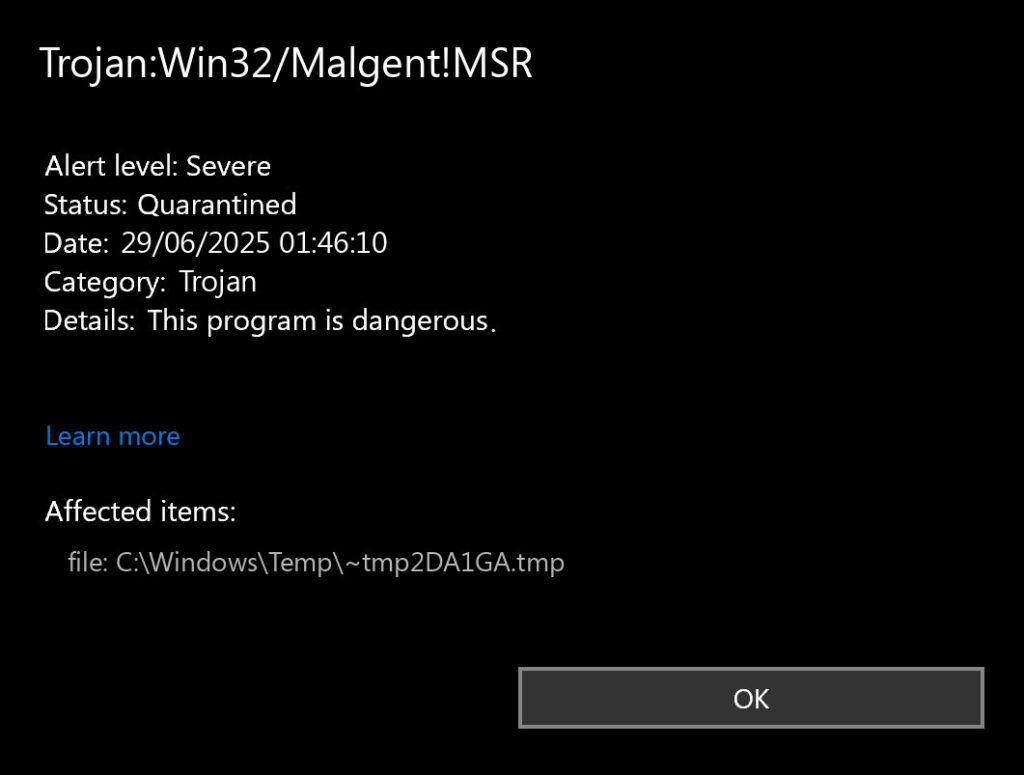
Once installed, this malware connects to remote servers controlled by criminals. It can download more malware to your system. It can also steal your personal information, similar to other information stealing malware we’ve analyzed.
How to Tell if You’re Infected
Look for these warning signs on your computer:
- Slow computer performance – Your system takes longer to start and respond
- High CPU usage – Task Manager shows processes using lots of resources
- Unknown processes running – Strange programs appear in Task Manager
- Antivirus alerts – Repeated detections of Trojan:Win32/Malgent!MSR or heuristic virus warnings
- Network activity – Your internet connection seems busy even when you’re not using it
- New files appearing – Files you didn’t create show up in system folders
Manual Removal Steps
You can remove Trojan:Win32/Malgent!MSR manually by following these steps carefully. Take your time with each step. Make sure you complete each one before moving to the next.
Step 1: Restart in Safe Mode
Safe Mode prevents the malware from running while you clean your system. Here’s how to start in Safe Mode:
- Press Windows + R keys together
- Type msconfig and press Enter
- Click the Boot tab
- Check the Safe boot option
- Select Minimal and click OK
- Restart your computer
Step 2: Check Running Processes
Look for suspicious processes that might be related to the malware:
- Press Ctrl + Shift + Esc to open Task Manager
- Click the Processes tab
- Look for these suspicious processes:
- Random named .exe files with high CPU usage
- Processes running from temp folders
- Unknown processes with network activity
- Right-click suspicious processes and select End Task
- Note the file location before ending the process
Step 3: Delete Malicious Files
Remove files that the malware might have created. Check these common locations:
- Open File Explorer and navigate to these folders:
C:\Users\[YourUsername]\AppData\Local\Temp\ C:\Users\[YourUsername]\AppData\Roaming\ C:\ProgramData\Microsoft\Windows\WER\Temp\ C:\Windows\Temp\
- Look for recently created files with random names
- Delete any suspicious .exe files you don’t recognize
- Pay attention to files created around the time you noticed the infection
Step 4: Clean Startup Programs
Remove the malware from your startup programs so it doesn’t run when Windows starts:
- Press Windows + R and type msconfig
- Click the Startup tab
- Look for unknown programs or programs with suspicious names
- Uncheck any suspicious entries
- Click Apply and OK
Also check the startup folder:
- Press Windows + R and type shell:startup
- Delete any suspicious files in this folder
Step 5: Clean Registry Entries
Remove malicious registry entries. Be careful with this step:
- Press Windows + R and type regedit
- Navigate to these registry keys:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run HKEY_CURRENT_USER\Software\Classes\Local Settings
- Look for entries with suspicious names or paths to temp folders
- Right-click suspicious entries and select Delete
- Be careful not to delete legitimate Windows entries
Step 6: Check Scheduled Tasks
Malware often creates scheduled tasks to restart itself:
- Press Windows + R and type taskschd.msc
- Click Task Scheduler Library
- Look for tasks with random names or suspicious triggers
- Right-click suspicious tasks and select Delete
- Check if any tasks point to files in temp folders
Step 7: Clear Temporary Files
Clean up temporary files where malware might hide:
- Press Windows + R and type %temp%
- Select all files (Ctrl + A) and delete them
- Empty your Recycle Bin
- Run Disk Cleanup to remove additional temporary files
Step 8: Restart Normally
After completing all steps, restart your computer normally:
- Press Windows + R and type msconfig
- Click the Boot tab
- Uncheck Safe boot
- Click OK and restart
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of backdoor trojans like Malgent. Professional anti-malware software can find hidden components and registry changes that you might miss.
The automatic approach is especially useful if you’re not comfortable editing the registry or if the manual steps didn’t completely remove the threat.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Browser Cleanup
If you suspect the malware affected your browser, clean it thoroughly:
Remove Malicious Browser Extensions
Check all your browsers for suspicious extensions:
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect browser-based components of the malware, reset your browser completely:
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
- Choose Reset and Clean up and Restore settings to their original defaults.
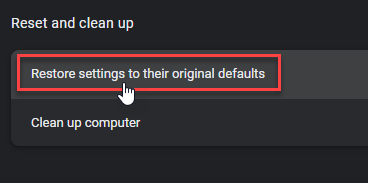
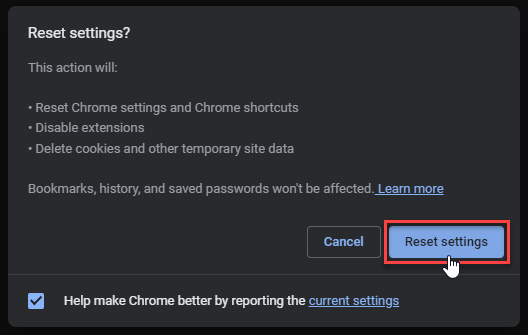
- Tap Reset settings.
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
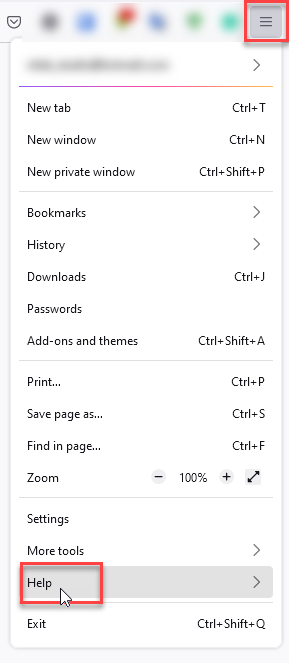
- Choose More Troubleshooting Information.
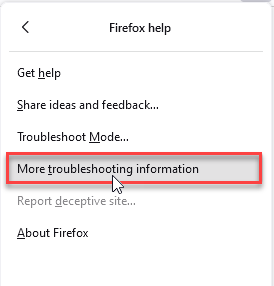
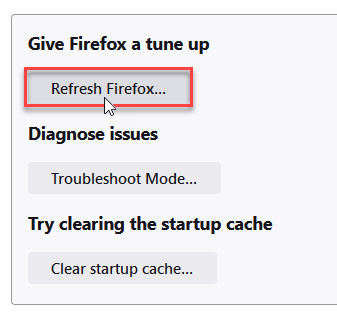
- Choose Refresh Firefox… then Refresh Firefox.
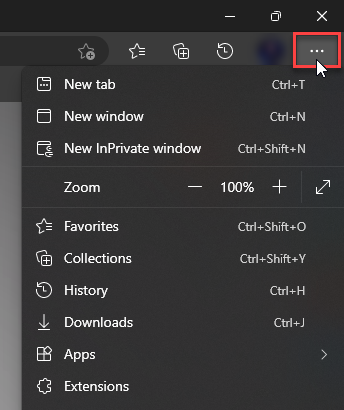
Microsoft Edge
- Tap the three verticals.
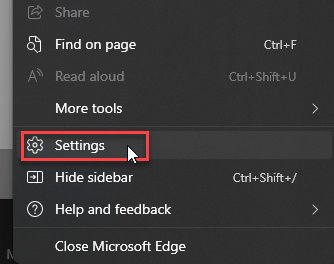
- Choose Settings.
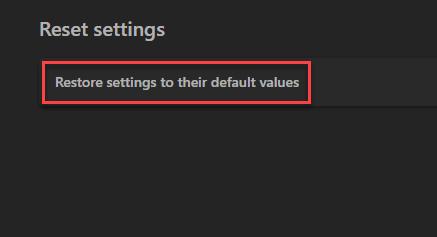
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
How to Prevent Future Infections
Trojan:Win32/Malgent!MSR typically spreads through these methods. Avoid them to stay safe:
Avoid Suspicious Software
- Don’t download cracked software – This is the most common source of Malgent infections. Learn about the dangers of cracked games and software
- Avoid fake system tools – Programs claiming to “speed up” or “clean” your computer often contain malware
- Don’t use unauthorized activators – Windows and Office activators frequently contain backdoors
- Be careful with “free” versions – Legitimate paid software offered for free is usually infected
Practice Safe Computing
- Keep Windows updated – Install security updates promptly
- Use reputable antivirus software – Keep it updated and running. Be careful not to disable Windows Defender unless necessary
- Download from official sources – Use official websites and app stores
- Scan downloads – Check files before running them
- Create regular backups – Keep important files backed up safely
Monitor Your System
Watch for signs of infection:
- Check Task Manager regularly for unknown processes
- Monitor your network usage for unusual activity
- Pay attention to system performance changes
- Keep an eye on your startup programs
Frequently Asked Questions
What is Trojan:Win32/Malgent!MSR and why is it dangerous?
Trojan:Win32/Malgent!MSR is a backdoor trojan that gives criminals remote access to your computer. It’s dangerous because it can steal your personal information, install more malware, and use your computer for criminal activities without your knowledge. Understanding trojan malware facts can help you recognize these threats better.
How did Trojan:Win32/Malgent!MSR get on my computer?
This malware usually comes bundled with cracked software, fake system tools, or pirated programs. It can also spread through infected email attachments or malicious websites. The most common source is downloading “free” versions of paid software.
Can I remove Trojan:Win32/Malgent!MSR manually?
Yes, you can remove it manually by following the steps in this guide. However, manual removal requires careful attention to detail and can be time-consuming. If you’re not comfortable with technical procedures, automatic removal tools are safer and more reliable.
Is it safe to delete processes related to Malgent?
Yes, it’s safe to delete malicious processes related to Malgent. The trojan creates these processes to maintain its presence on your system. However, be careful not to delete legitimate Windows processes. When in doubt, research the process name before deleting it.
What if my antivirus shows false positive detections?
Sometimes legitimate programs like Tor Browser are incorrectly flagged as Trojan:Win32/Malgent!MSR. If you downloaded software from official sources and you’re sure it’s legitimate, you can add it to your antivirus exclusions. However, if you downloaded from suspicious sources, treat the detection as real.
How can I prevent Trojan:Win32/Malgent!MSR infections?
Avoid downloading cracked software, fake system tools, and unauthorized program activators. Download software only from official sources. Keep your operating system and antivirus updated. Be cautious with email attachments and suspicious websites.
What if manual removal doesn’t work?
If manual removal doesn’t completely eliminate the threat, use professional anti-malware software like GridinSoft Anti-Malware. Some variants of this trojan can be particularly persistent and may require specialized removal tools to completely clean your system. You might also encounter similar issues with other persistent trojans that need automatic removal.
Can Trojan:Win32/Malgent!MSR steal my passwords?
Yes, this backdoor trojan can steal passwords and other sensitive information. It can capture keystrokes, take screenshots, and access stored credentials in your browsers. If you suspect you’re infected, change your important passwords after cleaning your system.
Does Trojan:Win32/Malgent!MSR affect all versions of Windows?
This malware can affect various Windows versions, including Windows 10 and Windows 11. The removal steps in this guide work for most Windows versions, though some interface details might vary slightly between versions.
How do I know if the removal was successful?
After removal, monitor your system for a few days. Check if your computer performance improves, if unknown processes disappear from Task Manager, and if your antivirus stops showing detections. Run a full system scan to confirm the threat is gone.
Conclusion
Removing Trojan:Win32/Malgent!MSR from your computer is possible with the right approach. The manual method works well if you follow each step carefully. However, automatic removal tools provide better protection against hidden components and future threats.
Remember that prevention is always better than removal. Avoid downloading software from untrusted sources. Keep your system updated and use reliable antivirus protection. These simple steps will help you avoid most malware infections.
If you found this guide helpful, you might also want to read about similar trojan variants, PUA detections, and connection security issues.