Trojan:Win32/LsassDump.A is a detection that targets the LSASS process. Similar to other heuristic detections, it focuses on behavior rather than the file itself.
Trojan:Win32/LsassDump.A Overview
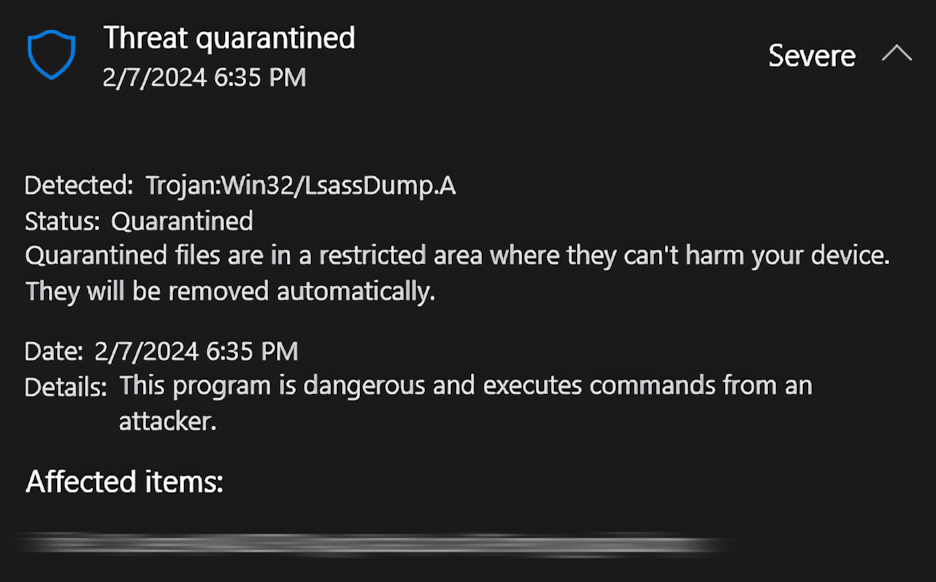
Trojan:Win32/LsassDump.A is a heuristic detection by Microsoft Defender, triggered by unauthorized access to the Windows LSASS process. As a heuristic detection, it flags attempts to access the process, particularly its memory dump, regardless of whether it’s initiated by malware or a user. In both scenarios, the Defender will deem this behavior suspicious and respond accordingly.
LSASS (Local Security Authority Subsystem Service) is a legitimate Windows process that manages security policies, and user authentication and handles security tokens and credentials. In essence, the memory dump of this process stores user credentials, including passwords, in both encrypted and sometimes unencrypted forms. Unsurprisingly, attackers are keen on compromising this process.
This gives us a clue on what malware can cause the Trojan:Win32/LsassDump.A detection. Backdoors often use information like one stored in the LSASS memory to gain persistence, particularly for creating a so-called shadow user. Though, there are spyware samples that do the same trick, most often ones that aim at long-term presence in the infected system.
Technical Analysis
Now let’s take a practical look at how malware behaves on a system. Being a heuristic detection, it’s based on observed behavior rather than a specific threat. Thus, we’ll focus on the malware’s impact on the system rather than discussing a specific threat. Memory dumps can be obtained through various methods, including Task Manager, DLL Host, or DbgHelp.dll. Yet LSASS is more attractive, as its memory contains the most actual information.
In this case, upon execution, the malware immediately performs checks to detect virtualized environments, sandboxes, or debuggers. The malware leverages the Windows Error Reporting component along with other legitimate processes, such as:
%windir%\System32\svchost.exe -k WerSvcGroup
%windir%\system32\WerFault.exe
wmiadap.exe /F /T /R
Further, it reviews a selection of registry values that can contain traces of virtualization or, at the very least, enabled logging. These checks point at this malware aiming at long-term persistence once again, hinting that we’re likely dealing with a backdoor.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\InstallationType
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\PowerShell\ModuleLogging\EnableModuleLogging
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OLE\Diagnosis
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsRuntime\ActivatableClassId\Windows.Foundation.Diagnostics.AsyncCausalityTracer
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Policies\Microsoft\Cryptography\Configuration
Once the malware verifies that the system isn’t virtualized or under debugging, it advances to the next phase – neutralizing security software. The resulting process tree is below, and it
C:\Windows\system32\services.exe
C:\Windows\system32\SecurityHealthService.exe
C:\Windows\system32\svchost.exe -k DcomLaunch -p
The malware then queries the following system values, in order to collect information about the client. Together with data it has got in previous steps
C:\Program Files\Windows Defender\MpClient.dll
C:\Program Files\Windows Defender\MpOAV.dll
C:\Program Files\Windows Defender\MsMpLics.dll
C:\Program Files\WindowsProtection\Updater.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer
Payload
During execution, the malware downloads certain files from https://developerr-bots[.]xyz. Those are likely configuration files, needed for this backdoor to get further instructions. Still, these can be malware payload files, too – it is entirely case-dependent.
https://developerr-bots.xyz/125688/Updater.exe?hash=AgADZw
https://developerr-bots.xyz/125688/Updater.exe?hash=AgADZwLQ
These “Updater.exe” files are further placed in several different directories across the system volume. Such a tactic makes it much harder for users to perform manual removal, and also decreases potential damage when a certain antivirus program finds only one malicious file.
C:\Users\user\AppData\Local\Temp\DownloadScript\updater.exe
%SAMPLEPATH%\7e7e69685128bee624a05f06de2bbe0849cf7ca8629103136872a1b0ada46236.exe
C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Manaa57fc8cc#\999d72a4e033bba86d05407570c67cba\System.Management.Automation.ni.dll
The malware once again leverages WerFault.exe to silently terminate the lsass.exe process and generate a memory dump. That is exactly the action that causes the LsassDump.A detection.
After completing its operations, the malware reconnects to the C2 server and exfiltrated the collected data. As a backdoor, it transmits only basic system information and awaits further commands from the attacker. It is likely that the malware uses the same https://developerr-bots.xyz as the C2 server.
How To Remove Trojan:Win32/LsassDump.A?
Removing Trojan:Win32/LsassDump.A, can typically be handled by the built-in Windows security tools. However, to avoid such incidents, I recommend using an advanced anti-malware solution like GridinSoft Anti-Malware. Just follow this guide to eliminate malware from your system and ensure robust, proactive protection going forward.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.