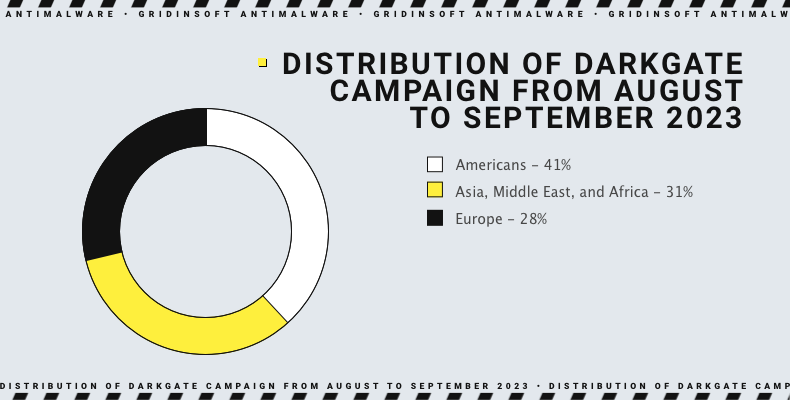
Over the past few years, DarkGate has been relatively inactive. However, several campaign deployments have been detected this year across the Americas, Asia, the Middle East, and Africa. They started to aim at Microsoft apps, such as Skype and Teams, for spreading to target systems.
What is DarkGate Loader?
DarkGate Loader is a type of malware that is capable of downloading and running other types of malware, including ransomware, trojans, and cryptocurrency miners. Additionally, it can be used to extract sensitive data from the victim’s computer, such as passwords, credit card numbers, and personal information.
This malware is typically distributed via phishing emails or malicious attachments. Once it is installed on the victim’s computer, it can communicate with a remote command and control (C2) server to receive instructions and download additional malware.
DarkGate Loader has been gaining popularity among cybercriminals since its creator advertised it as a Malware-as-a-Service offering on popular forums in June 2023. Previously, DarkGate Loader was distributed using traditional email-based malspam campaigns, similar to those used by Emotet. However, an operator started using Microsoft Teams to deliver the malware in August via HR-themed social engineering chat messages. This new tactic has led to an increase in the number of DarkGate Loader infections.
DarkGate Spreads Via Microsoft Teams And Skype Spam
A company has been facing a targeted phishing attack since late September. The attackers have been using Microsoft Teams functionality to deliver the DarkGate Loader malware. Fortunately, all the employees were regularly trained to identify phishing attempts, and they promptly intervened. As a result, no employees, customers, or company resources were harmed during this incident. The malicious message was blocked before it could reach any of the employees.
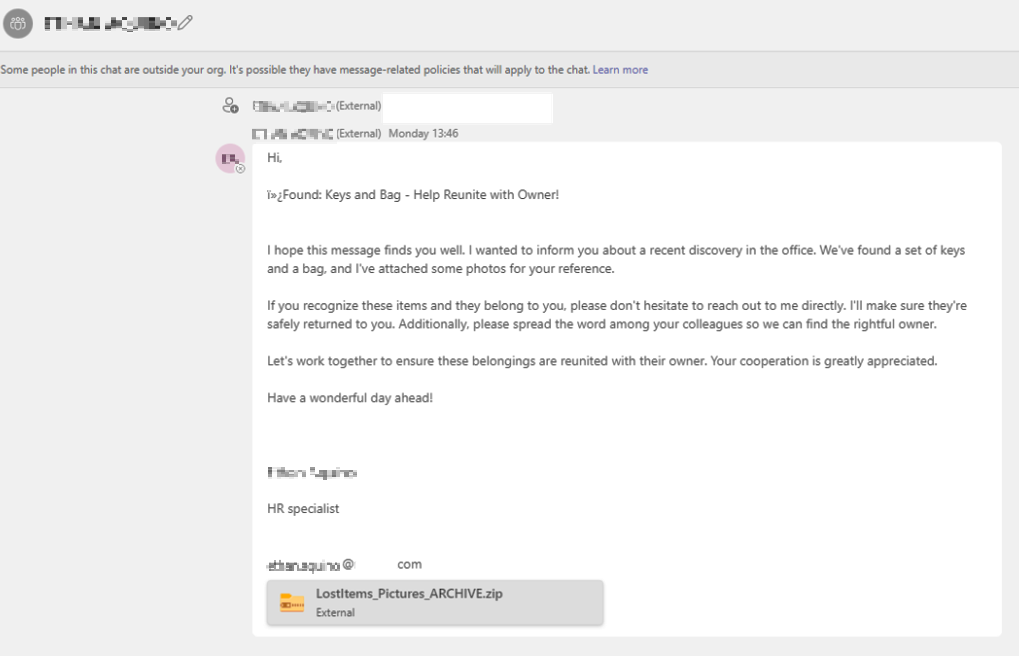
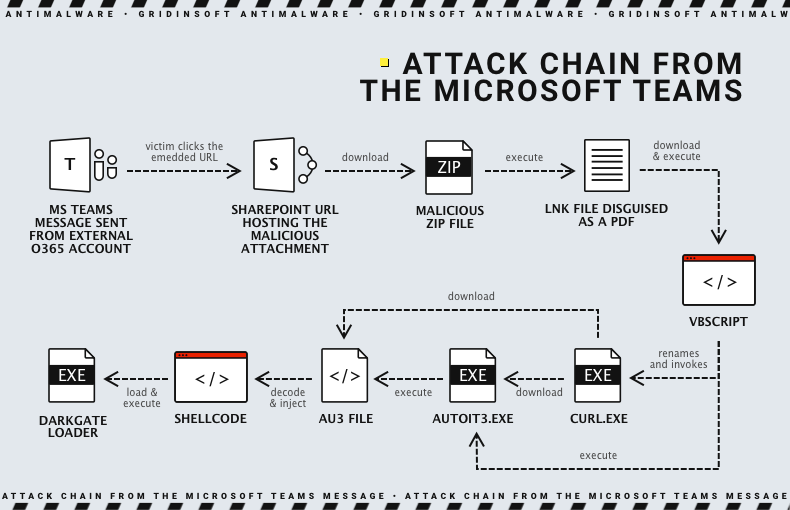
After analyzing a recent case, we discovered that the DarkGate Loader malware was delivered in the payload of a ZIP archive. The image below illustrates the entire attack process, from the moment the Microsoft Teams message is sent to the execution of the DarkGate Loader:
In the next sample, the threat actor exploited a trusted relationship between two organizations to trick the recipient into running the attached VBA script. By gaining access to the victim’s Skype account, the attacker could take control of an existing messaging thread and create file names related to the chat history’s context.
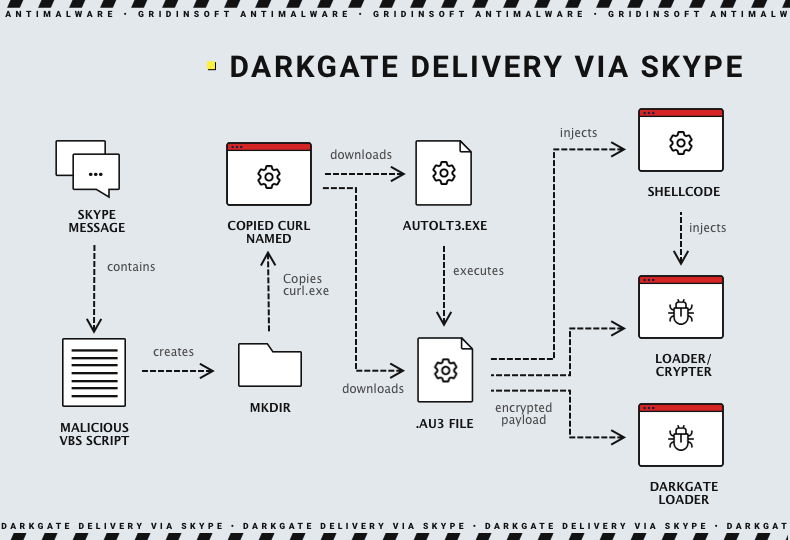
The victims were sent a message from a compromised Skype account. The message contained a deceptive VBS script with a file name that followed the format: “www.skype[.]vbs. In this sample, the recipient believed that the sender was someone from a trusted external supplier.
Installation Consequences
Experts noticed that the threat was functioning as a downloader of further payloads. Once the DarkGate malware was installed, it deposited files in both the <С:/Intel/> and <%appdata%/Adobe/> directories, which aided in its attempt to disguise itself.
The dropped files were identified as variations of either DarkGate or Remcos, most likely to enhance the attackers’ hold on the infected system. Below are some of the sample file names we came across for these additional payloads:
- Folkevognsrugbrd.exe
- logbackup_0.exe
- sdvbs.exe
- Vaabenstyringssystem.exe
- Sdvaners.exe
- Dropper.exe
How to protect against DarkDate Loader?
DarkGate Loader is a dangerous malware that can be used to steal sensitive data from your computer and install other malware, such as ransomware and trojans. Whether you are an individual or an organization, it is important to be aware of the risks posed by DarkGate Loader and to take steps to protect yourself.
To protect you and your organization against DarkGate Loader, you can take the following steps:
- Using a reliable password manager to create and store strong, individual passwords for all your accounts is crucial. Strong passwords are complex to guess and can protect your accounts from brute force attacks.
- Implement a web content filtering solution to block malicious websites. A web content filter prevents access to known malware and phishing sites.
- Deploy a next-generation firewall (NGFW) to protect your network from malicious traffic. An NGFW can help to detect and block malware, phishing emails, and other types of cyberattacks.
- Only download software and files from reputable sources. Avoid downloading files from suspicious websites or using unofficial app stores.
- Use EDR/XDR to provide real-time monitoring, threat detection, and incident response capabilities across your network and endpoints. These tools can identify unusual or suspicious activities that could indicate loader malware.