One Year of Russian-Ukrainian War in Cybersecurity
February 24, 2022, will be a turning point in history. It was…
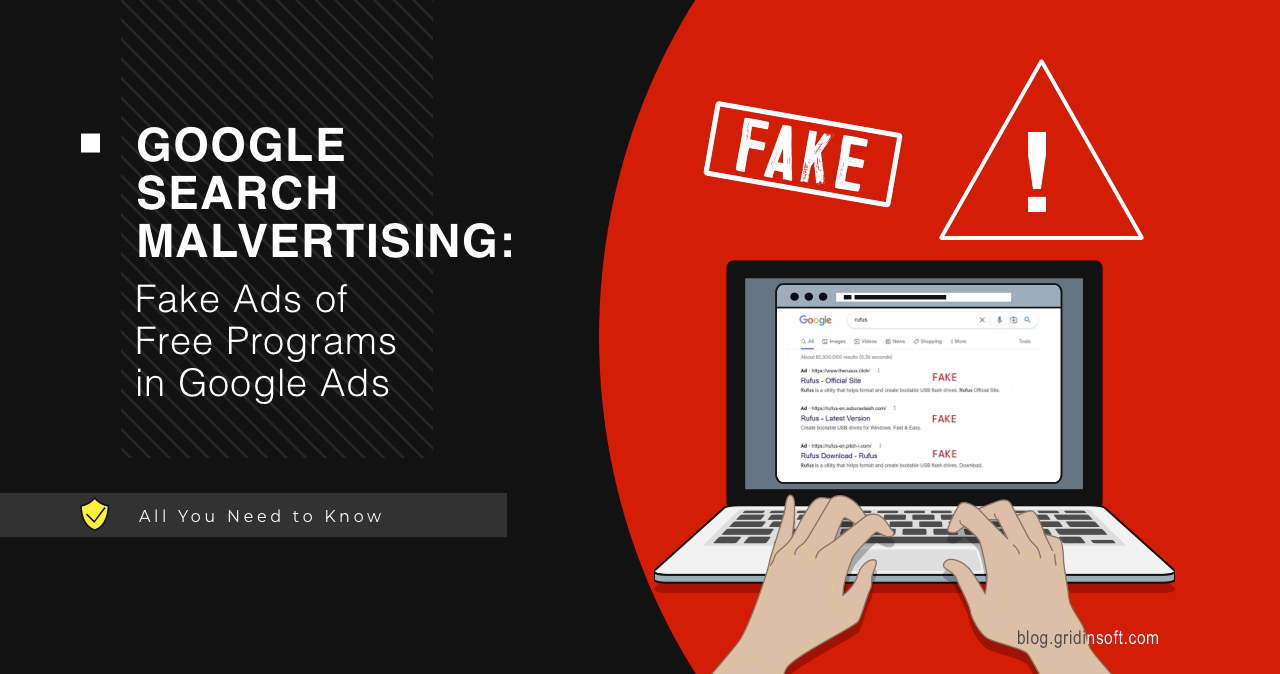
Google Search Malvertising: Fake Ads of Free Programs in Google Ads
Google Search malvertising is an unpleasant phenomenon of malicious advertisements in search…
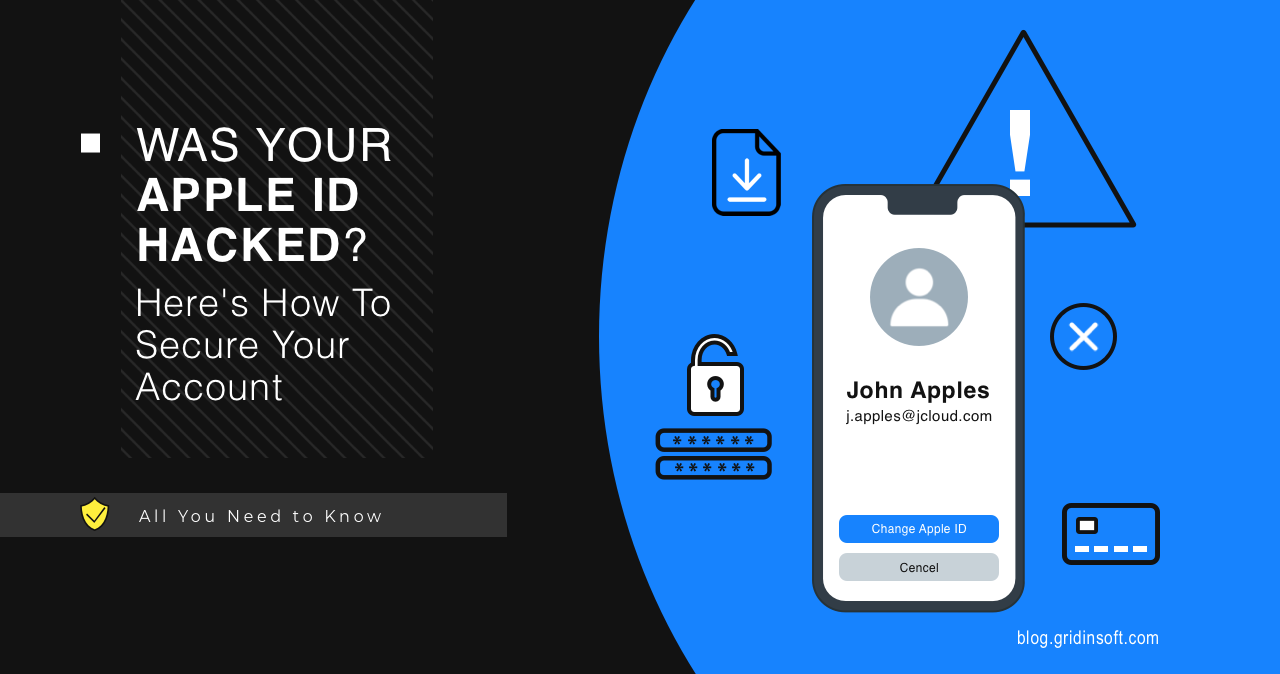
Was Your Apple ID Hacked? Here’s How To Secure Your Account
Apple's services and products are only accessible through their walled garden. Users…
Browser Cookies Definition And Most Significant Types
Cookies are an essential part of how the Internet works. They help…
Texting Spam: How to Stop Spam Text Messages
What does spam mean in texting? Receiving random text messages from unknown…
Difference Between IPSec and SSL
In the last couple of years, remote work has become integral to…
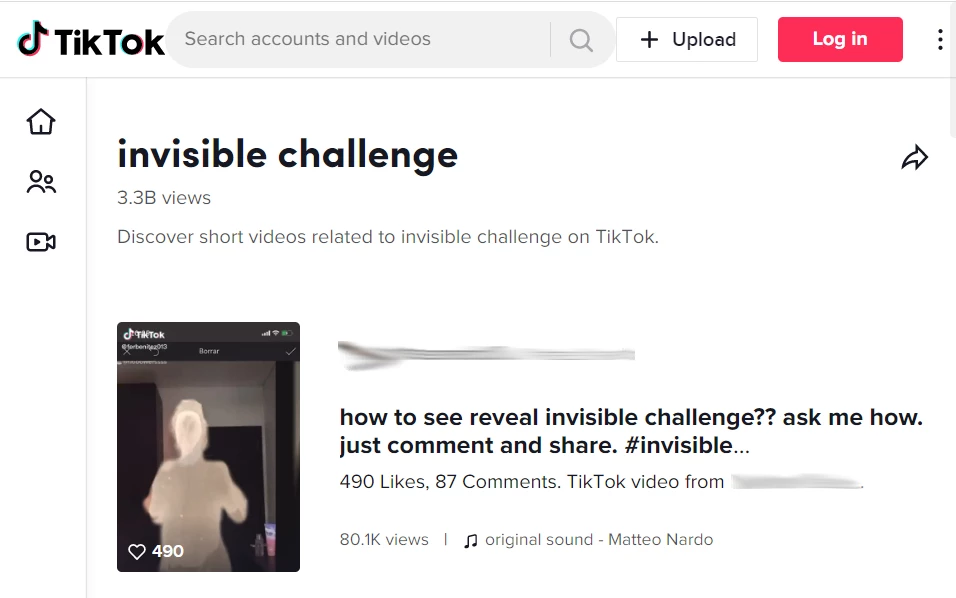
TikTok Invisible Challenge Is Used to Spread Malware
TikTok Invisible Challenge became yet another host for threat actors. Crooks found…
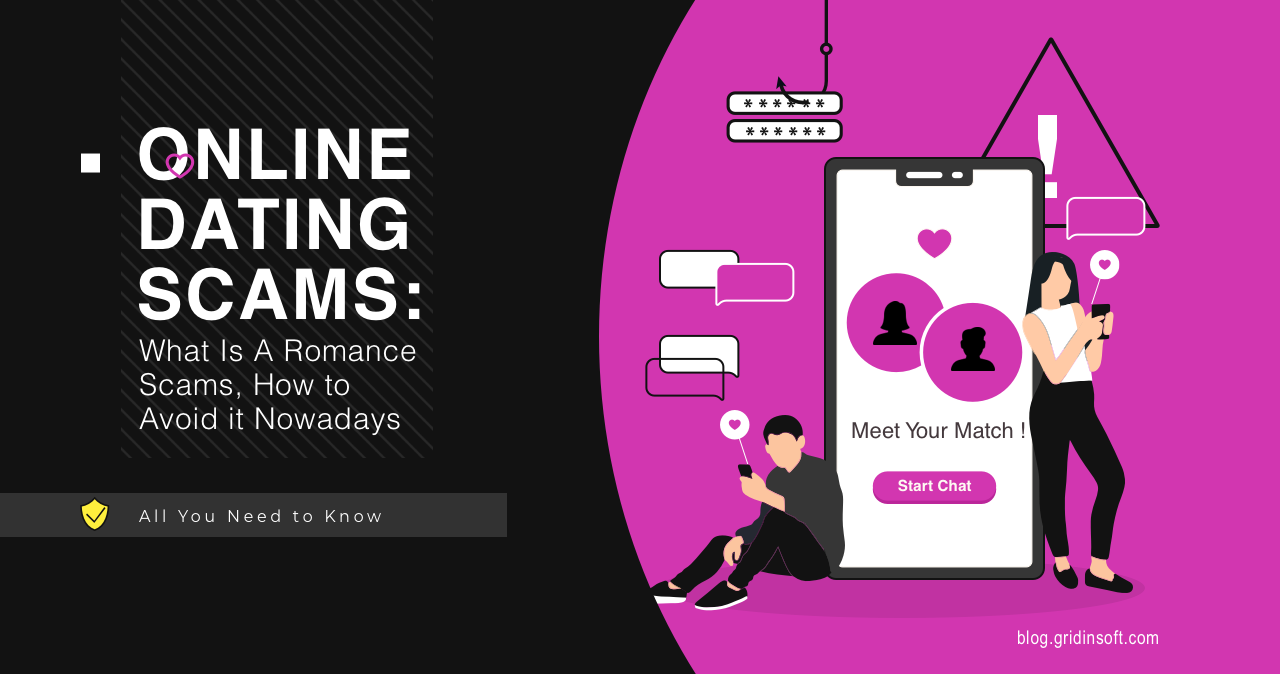
Online Dating Scams: How to Avoid Romance Scam
Online dating scammers get you to believe that their fake romances are…
What Is an Evil Twin Attack? How Does It Work?
How often do we connect to free Wi-Fi networks in public places?…
What is eWallet? How to Protect Your eWallet
During a time of crisis, Americans turned to digital wallets called eWallets…
Beware Snapchat Hacker Attacks: How to Stop Them
There's a demand for users to secure their privacy and security when…
Transport Layer Security (TLS): Difference Between TLS and HTTPS?
Transport Layer Security is a widely used security protocol designed to ensure…