Proxyjacking: The Latest Cybercriminal Invention In Action
Today, in the constantly changing world of cyber threats, attackers always look…
Akira Ransomware Decryptor Is Available To The Public
Cybersecurity experts have released a decryptor for the Akira ransomware. It will…
Super Mario Malware: Hackers Spread Stealers in the Fake Game
The Super Mario video game franchise has gained immense acclaim due to…
How Can Companies Be Secure Against Cyberattacks?
Organizations face an alarming reality in the digital world: data breaches and…
Credentials Theft is On The Rise
Email spam has become the prevalent form of phishing and malware spreading…
How to Protect Your Digital Footprint
The modern business world has been greatly advanced by the internet. Its…
BreachForums Is Back Online, Led by ShinyHunters
BreachForums, an infamous Darknet forum that was shut down in late March…
Fortinet Fixes RCE Flaws in FortiOS and FortiProxy
Fortinet, a well-known vendor of corporate-grade security solutions, issued an urgent patch…
Third Party Data Breach: Definition and How to Prevent It
In today's digital landscape, data breaches have become an alarming reality for…
Android Malware Mimics VPN, Netflix and Over 60k of Other Apps
Android is an open operating system. This is an advantage and a…
Beware of Vacation-Related Scams: 4 Most Prevalent Types
Email scam actors constantly try to pick a better disguise for their…
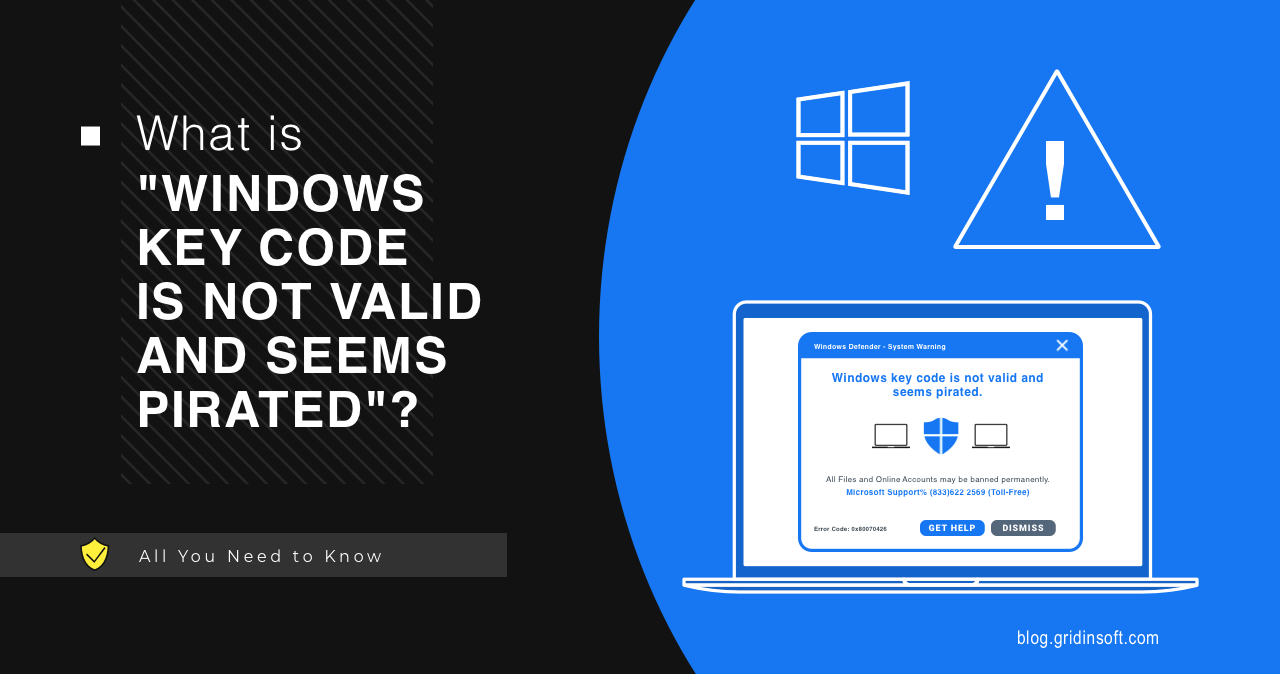
What is “Windows Key Code Is Not Valid And Seems Pirated”?
Windows Key Code Is Not Valid And Seems Pirated appears to be…