SMApps is a malicious program that aims at spreading illegal promotions. It mainly attacks browsers by changing settings and redirecting search queries from Google to suspicious sites. Possible distribution methods are standard: malicious adverts and dodgy sites with hacked software.
This malware uses different detection evasion, anti-analysis, and persistence tactics. Although primarily positioned as adware, it can deliver other adware-like applications and log keystrokes.
SMApps Overview
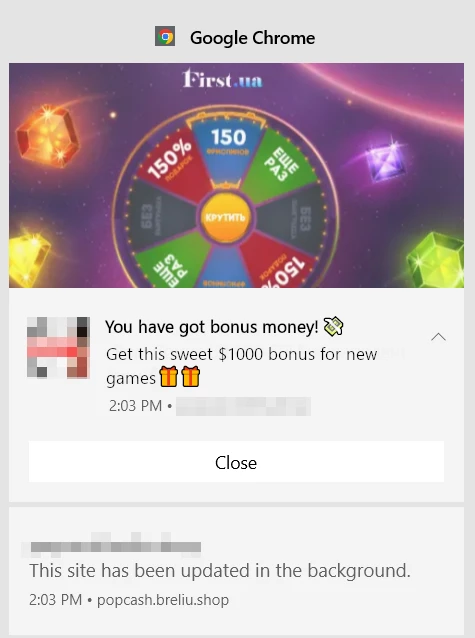
SMApps is malware that falls under the designation of adware and browser hijackers. This malware mainly targets altering web browser settings, mainly ones around search engines and homepages. After typing a search query on Google.com, a redirect to Bangsearch[.]pro occurs instead of the expected search results.
Aside from Bangsearch, SMApps can promote literally any other engine, depending on who pays. Even when it throws the user to Yahoo or Bing, the results appear to be altered and may contain harmful content. In addition, fake search systems often collect sensitive user data, to a much bigger extent than more usual search providers.
At first glance, it may appear to be just annoying, as the majority of adware viruses. However, this is different. Detailed analysis has shown that SMApps can steal sensitive information from the victim’s device and redirect search queries. It can capture keystrokes, collect process information, and install additional payload (usually other adware). This thing’s removal is tricky regardless of the infection path because the malware uses various tricks to avoid this. I’ve made my analysis of this threat, finding all the tricks it does in the infected system – you can see it below.
Key spreading places for SMApps virus are websites that distribute hacked software, and malicious ads. Shady pages with add-ons or mods to popular games do their contribute to this malware spreading. Moreover, this thing can spread by itself, replicating the files to USB drives, effectively acting like a worm, so be careful with what you plug into your USB port.
Technical Analysis
It was not hard to retrieve the sample of SMApps – malware analysis platforms are filled with its samples. This one was some kind of a hack for Roblox, which checks up with what I’ve found about spreading ways. Let’s peek into its internals and in-system activities.
Initial Access
The Initial Access stage involves SMApps using various methods to gain a foothold in the target system. In the next stage, attackers may use Windows Management Instrumentation to query sensitive video device information or check if an antivirus program is installed. This acts as both system fingerprinting and analysis/VM evasion step:
IWbemServices::ExecQuery - ROOT\cimv2 : SELECT * FROM Win32_VideoController
IWbemServices::ExecQuery - ROOT\SecurityCenter2 : SELECT * FROM AntiVirusProduct
This is often done to detect virtual machines. It also queries the firmware table information and checks if the current process is being debugged. Additionally, it queries disk information to detect virtual machines. To hinder dynamic analysis, the program may contain medium and long sleep (>= 30 seconds and >= 3 minutes respectively) and use evasive loops.
Persistence & Privilege Escalation
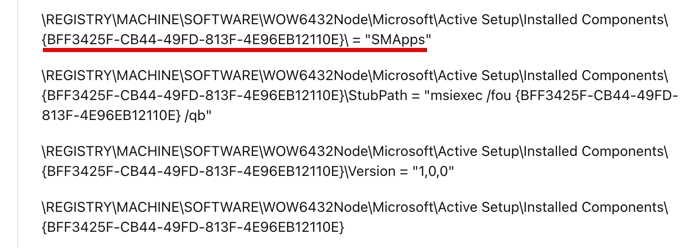
SMApps gains persistence via creating or modifying Windows services, registry run keys, and startup folders.
It calls for Windows Installer to arrange its further execution, hiding the window through the command line arguments.
"C:\Windows\system32\msiexec.exe" /I "C:\Users\
To gain more persistence and additional privileges, this program calls for Windows Error Reporting service. This trick is rather popular these days, as it abuses the ability to relaunch the process with top privileges without calling for a UAC window.
C:\Windows\SysWOW64\WerFault.exe -pss -s 492 -p 7280 -ip 7280
C:\Windows\SysWOW64\WerFault.exe -pss -s 552 -p 3300 -ip 3300
Command Server Connection, Additional Installations
As for communications with C2, SMApps use FTP protocol and a list of pre-determined addresses to connect to. In my case, the 162.250.124.82:21 address was a primary server. However, the connection cannot boast of any rich logs – malware just sends the info about the infected system. However, more interesting stuff surfaced after giving the thing to run in the background.
As I said above, SMApps can act as a dropper. It dropped two files after installation:
IdealWeightOperator.exe
IdealWeightService.exe
These two malicious programs are pretty much the same as SMApps itself in terms of functionality. They change browser settings on top of what the original thing does, promoting questionable sites and spawning unwanted ads. Even though these threats are not really severe, the fact that it is capable of doing so is concerning.
How To Remove SMApps?
To remove SMApps, you need an effective antivirus solution. I recommend GridinSoft Anti-Malware as it will help remove this malware without much effort. Users report problems with removing this malware with the manual approach, therehence a specialized tool is required. GridinSoft program will also allow you to reset your browser in two clicks. This is especially effective when the browser has been interfered with by adware.





