The Security Blog From Gridinsoft
BLUFFS Bluetooth Vulnerability Threatens Billions of Devices
Eurecom has uncovered a series of exploits named “BLUFFS”, posing a significant threat to the security of Bluetooth sessions. These…
Okta Hack Exposes Data of All Support Customers
Back in mid-October 2023 Okta, one of the world’s largest identity providers, suffered a data breach. Security vulnerabilities in its…
Henry Schein was hacked twice by BlackCat ransomware
Henry Schein Global, a healthcare solutions provider, faced a persistent cybersecurity nightmare. The BlackCat/ALPHV ransomware gang is launching a second…
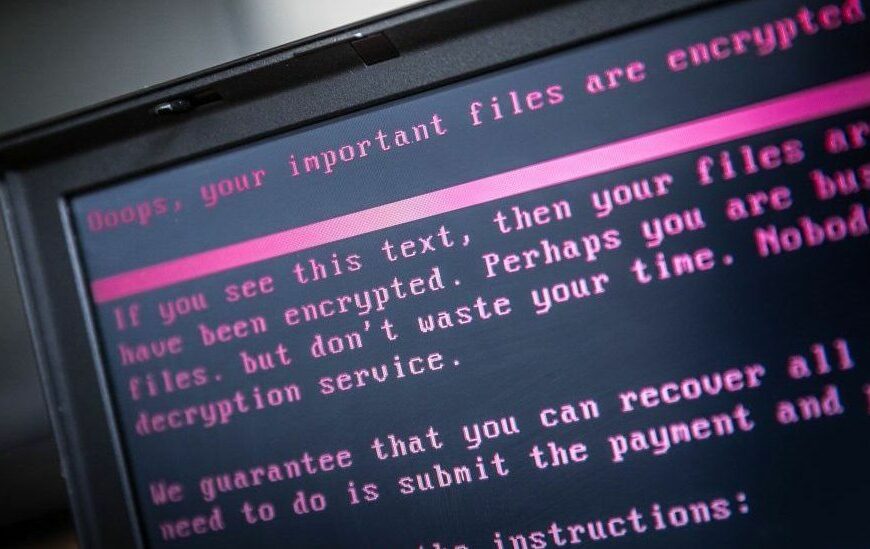
Ethyrial: Echoes of Yore Ransomware Attack Wiped Player Accounts
“Ethyrial: Echoes of Yore” fell victim to a ransomware attack last Friday. The attack hit 17,000 player accounts, wiping them…
Dharma Ransomware Criminals Captured in Ukraine, Europol Reports
On November 28, 2023, Europol claimed successful detainment of ransomware operators, particularly related to Dharma and Hive ransomware. The operation…
SYMBIOTE Backdoor and Rootkit Dropper Revealed
Symbiote Backdoor: a Stealthy and Highly Evasive Linux Malware Researchers…
Internet Explorer shutdown. The Epithaf
On June 15, Microsoft will finally end support for Internet…
Team Xecuter’s life. How hackers leave after the arrest?
Gary Bowser, the Nintendo hacker, appears to be a very…
Companies Manage to Bargain With Ransomware Racketeers
Revelations of the Ransom-Negotiator In May, the racketeer-bargaining specialist (the…
The US Department of Justice Reports a Russian Botnet Dismantled
RSOCKS Russian Botnet Is No More as a Result of…
Microsoft Fixed Follina Vulnerability and 55 Other Bugs
As part of the June Patch Tuesday, Microsoft finally fixed…
Around 2000 People Arrested by Interpol for Internet Scams
Operation “First Light” The war on cybercrime goes on. As…
BlackCat ransomware gang publishes leaked data on the clear web site
BlackCat/ALPHV group recently announced on its victim shaming and extortion…
War in Ukraine triggered a Stream of amateurish ransomware
Russia has provoked hackers around the world to focus their…
The US Will Introduce A Cyber Army Into Its Military Units
By 2030 the US plans to double the size of…
Iranian Spear-Phishing Operation Targets US And Israeli High Executives
In a wake of rising tensions between Israel and Iran,…
Google Is Trying to Get Rid of the Engineer Who Suggested that AI Gained Consciousness
Blake Lemoine, a senior software engineer at Google’s Responsible AI…