The Security Blog From Gridinsoft
New Google Chrome 0-day Vulnerability Exploited, Update Now
In the most recent release notes, Google reports about a new 0-day vulnerability that is already exploited in the wild.…
Novice FBot Stealer Targets Cloud Services
Researchers report about a new malware strain dubbed FBot. This Python-based malicious program appears to be a unique tool in…
AzorUlt Stealer Is Back In Action, Uses Email Phishing
Cybersecurity experts have stumbled upon the eight-year-old Azorult malware. This malware steals information and collects sensitive data, and has been…
Remcos RAT Targets South Korean Users Through Webhards
An infamous Remcos RAT reportedly started targeting South Korean users through the files shared on Webhards platform. By baiting users…
GitLab Zero-Click Account Hijack Vulnerability Revealed
On January 11, 2024, GitLab released an update with the official warning regarding the critical security violation fix. The vulnerability…
Open-Source Cryptor Cryptonite Became a Wiper due to a Bug
Fortinet researchers studied the recently appeared open-source cryptor Cryptonite, distributed…
Fosshost, an Open-Source Project Hosting, Is Closing Down as Its Leader Disappeared
Volunteers of the open-source project hosting Fosshost, whose services are…
Application Bugs Allowed to Open and Start Cars Hyundai, Genesis and Others
Experts from Yuga Labs discovered vulnerabilities in mobile applications for…
FBI Says Cuba Ransomware ‘Made’ $60 Million by Attacking More Than 100 Organizations
The FBI and the U.S. Infrastructure and Cyber Security Agency…
Cyber Spies Use USB Devices to Infect Targets
Mandiant specialists talk about an unusual malware campaign affecting targets…
Dell, HP, and Lenovo Devices Use Older Versions of OpenSSL
Many Dell, HP and Lenovo devices use old and insecure…
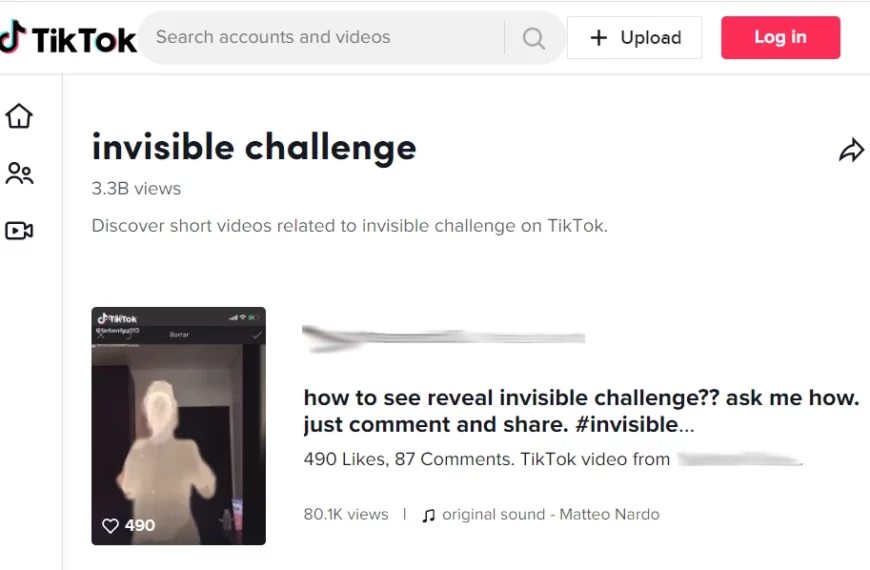
TikTok Invisible Challenge Is Used to Spread Malware
TikTok Invisible Challenge became yet another host for threat actors.…
Ragnar Locker Ransomware Accidentally Attacked Belgian Police
The operators of the ransomware Ragnar Locker published on their…
WhatsApp Hacked, Almost 500 Million Users Exposed
On November 28, 2022, information regarding a new WhatsApp breach…
“Password” Topped the List of the Most Common Passwords in 2022
The NordPass password manager team has prepared annual statistics by…
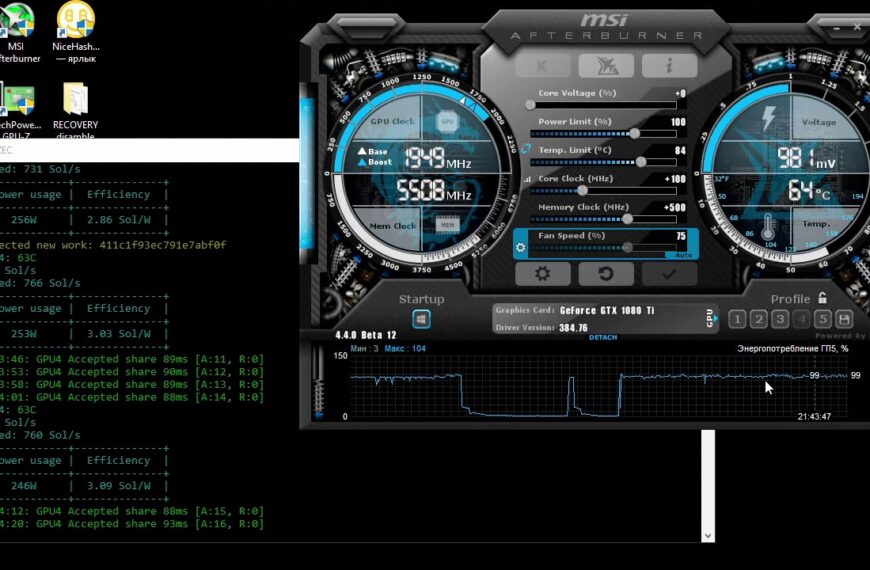
Fake MSI Afterburner Infects Users’ Machines with Miners and Stealers
According to cybersecurity specialists from Cyble, attackers distribute miners and…
Chrome Extension ViperSoftX Steals Passwords and Cryptocurrency
A Windows malware designed to steal cryptocurrency and clipboard contents…