In 1998, Microsoft introduced the Windows Terminal Server as an add-on to the Windows NT Server 4.0 operating system. This optional feature provided remote desktop access over the network using TCP/IP. Each subsequent release of Windows has included this capability, becoming the default remote session access standard for Windows desktop and server operating systems with the release of Windows XP (in October 2001). Remote Desktop Protocol became a logical successor of that technology. Although being a convenient technology for remote control, it has a great number of different vulnerabilities. Let’s see how to deal with it and use RDP in a secure way.
What is RDP?
RDP (Remote Desktop Protocol) is a particular protocol that provides full desktop access, including sound, clipboard, printers, and file transfer with high-resolution graphics (which can be reduced depending on bandwidth) to the remote user. Over 20 years, RDP has seen several versions with new features added to make it a reliable remote access protocol. During this time, Remote Desktop Protocol has also had security problems.
However, with the advent of the “new age,” which entails more remote working, increased reliance on cloud computing, and increasingly distributed environments. RDP became stretched for usage scenarios far beyond what was initially intended. Numerous threat and hacking research reports over the past 18 months have shown that misuse of RDP contributes to the successful dissemination of ransomware and other cyberattacks. Today we’ll explore RDP and how it works, RDP security risks, and RDP security recommendations.
How Does Remote Desktop Protocol work?
RDP uses a single TCP/IP port to establish a connection (3389 by default). It is derived from the T.128 application sharing protocol. Typically, all traffic is point-to-point, encrypted, and contains all data for efficient remote transmission and handling of the entire user experience with various failure mechanisms. Tolerance, authentication, and even support for multiple monitors.
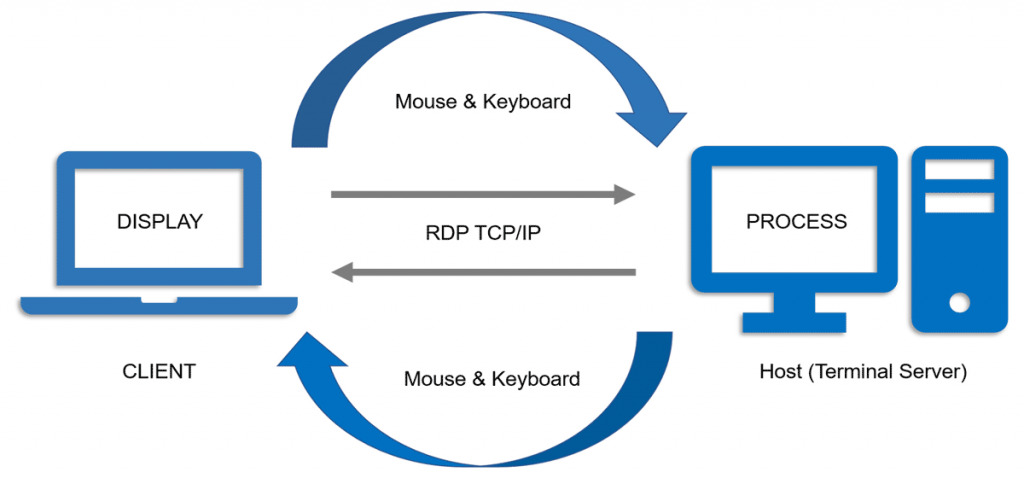
All this is done without using HDMI, USB, or other cables. However, it works fine over Wi-Fi and even over the cellular network if TCP/IP is available. In addition to the advantages, this technology has a disadvantage. Because port 3389 is open, attackers have the potential to penetrate the network directly, bypassing the firewall. For example, suppose you’re familiar with using Citrix Server or Microsoft Windows Terminal Services. In that case, you probably use Remote Desktop Protocol all the time – and may not even be aware of it – using the Remote Desktop (RD) Gateway approach or RD Web Access. which shares similar risks.
Common Remote Desktop Protocol Use Cases
Businesses of all sizes use RDP to access servers, collaborate with other employees, and remotely access desktops to perform tasks similar to those they would perform while in the office. The most common uses of Remote Desktop Protocol include:
- Providing a virtual desktop interface (VDI) to (or in) the cloud using a shared office environment (SOE) for employees or contractors.
- Providing a graphical user interface for remote servers, regardless of location, for maintenance, configuration, and troubleshooting.
- Providing access to help desks, call centers, and support services to remote users who provide technical support.
- Allowing employees, contractors, vendors, or auditors access to the desktop provides a user experience similar to the office.
All of these use cases are necessary to work from any location. However, some of them may be unsafe.
RDP brute force attack explanation
Recently, the number of brute force attacks on RDP connections has increased dramatically. These are automated attacks, and their goal is to hijack the desktop of a corporate computer and infiltrate the corporate network through it. For example, suppose a cybercriminal manages to infiltrate a computer on the corporate network via a remote desktop. In that case, it is easy for him to do all the things a legitimate employee could do, including access to confidential data and corporate email. In addition, illegitimate use of corporate email addresses can lead to phishing attacks (spear phishing). RDP attacks were widespread even before that: about 150,000 attempts were made daily. However, since the beginning of quarantine, when stricter quarantine and self-isolation measures went into effect worldwide, about a million brute force attacks against RDP connections have been attempted every day.
How to secure RDP?
Remote desktop sessions work over an encrypted channel, preventing anyone from viewing your session by eavesdropping on the network. However, there is a vulnerability in the encryption method of earlier versions of Remote Desktop Protocol sessions that could allow unauthorized access to your session via a man-in-the-middle (MITM) attack. You can secure the remote desktop using SSL/TLS. Although a remote desktop is more secure than remote administration tools such as VNC, which do not encrypt the entire session, there are risks every time an administrator is given remote access to the system.
Remote Desktop Protocol protection tips
- Use strong passwords. Before you start using RDP, be sure to implement strong password policies for RDP-enabled accounts.
- Use two-factor authentication. You can use special “third party” software to activate two-factor authentication to prevent unauthorized access.
- Always keep your software up-to-date. One advantage of using RDP over third-party remote administration tools is that all components are automatically updated with the latest Microsoft security patches. Ensure you are using the last versions of client and server software. However, when using other remote desktop platforms, ensure they are as current and supported and that the versions you have installed are up-to-date. Outdated versions may not support high levels of encryption and have other security vulnerabilities.
- Restrict access using firewalls. Use firewalls (both software and hardware) to limit access to the remote desktop listening ports (TCP 3389 by default). Using the RDP gateway is highly recommended to limit Remote Desktop Protocol access to desktops and servers. As an alternative to support connectivity outside the enterprise, you can use a VPN.
- Enable network-level authentication. By default, Windows 10, Windows Server 2012 R2/2016/2019 provides network-level authentication (NLA). Don’t neglect this feature, as NLA offers an additional layer of authentication before establishing a connection. The only exception may be the lack of NLA support by other platforms.
- Limit the users who can log in using a remote desktop. Only give administrative access to those who need it. Suppose you have more than one administrator account on your computer. In that case, it is worth restricting remote access to only those accounts that need it. If the remote desktop is not used for system administration, remove all administrative access via RDP, and allow only user accounts that require the RDP service. Remove the local administrator account from RDP access at the address for departments that manage many machines remotely and add a technical group instead.
- Set an account lockout policy. Configure your computer to block the account after several failed attempts. This way, hackers can’t get access by “brute force” using automatic password guessing tools.
Tips to Decrease the Chance of Remote Desktop Protocol Hacking
Deny direct RDP access to clients or servers outside the enterprise. Opening RDP (port 3389) to networks outside the enterprise is highly discouraged because it is a known vector for many attacks. Instead, after configuring the RDP gateway, configure the nodes should to allow RDP connections only from the gateway node or subnets in the organization that needs it.
Use RDP gateways (best practice). The use of an Remote Desktop Protocol gateway is highly recommended. It allows hard-limit access to remote desktop ports while maintaining remote connections through a single “Gateway” server. When using the Remote Desktop Gateway server, you should restrict all remote desktop services on workstations to allow access only from the Remote Desktop Gateway. The Remote Desktop Gateway server listens for remote desktop requests over HTTPS (port 443). Then, it connects the client to the remote desktop service on the target computer.
Change the default listening port for the remote desktop. Changing the listening port will help “hide” the remote desktop from hackers who scan the network for computers listening on the default remote desktop port (TCP 3389). This provides effective protection against the latest RDP worms such as Morto. (IMPORTANT: do not try this if you are not familiar with the Windows registry and TCP/IP).
Use tunnel connections to the remote desktop via IPSec or SSH. If using a remote desktop gateway is impossible, you can add a layer of authentication and encryption by tunneling remote desktop sessions over IPSec or SSH. IPSec appeared in all Windows versions since Windows 2000, but got a massive quality update in Windows 10. You can use SSH tunneling for remote desktop connections if an SSH server is available.




