The RegAsm.exe process is an important component of the Windows operating system associated with the .NET Framework. This utility is designed to register .NET assemblies in the Windows registry, allowing COM clients to call managed applications. Let’s analyze its functionality and see whether malware can abuse it.
What is RegAsm.exe?
RegAsm.exe (Assembly Registration Tool) is a command line utility that provides users and developers with the ability to register CLR (Common Language Runtime) assemblies in the Windows Registry. The main function of this utility is to create registry entries that link COM class identifiers and interfaces to the corresponding .NET classes. Thanks to this process, it is possible to use functionality written in .NET languages (e.g., C# or VB.NET) in applications developed in unmanaged languages (e.g., C++). This expands the possibilities of integrating different software.
How does it work?
The process is run via use Visual Studio Developer Command Prompt and Visual Studio Developer PowerShell using the following syntax:
RegAsm.exe assembly_name.dll [options]
Here “assembly_name” is the file name of the assembly to be registered.
Possible “options” include:
- /codebase – adds information about the assembly location to the registry, which allows CLR to find the assembly by its path;
- /tlb – creates a type library (TLB file) for the assembly, which is necessary to use it as a COM object;
- /registered – uses only versions of types already registered in the registry;
- /unregistered – removes information about the assembly from the registry.
Can RegAsm.exe be a Virus?
Although RegAsm.exe itself is a legitimate Microsoft utility for registering Windows builds. Its name can be used by malware to disguise its activity. It is a common method used by viruses and other types of malware to call themselves by the names of legitimate system files. This is done in order to confuse the users and antivirus programs.
Finding this process in Task Manager is not so easy. RegAsm.exe is launched only to perform build registration and terminates immediately afterwards. Therefore, its presence in the Task Manager will be very brief. In such a case, the user may simply not notice this process if they do not look at the Task Manager exactly at the moment of its execution.
Malware may create or download a file named RegAsm.exe (not original, obviously) in an inappropriate location (such as in a user’s folder or temporary folders) and run it from there to avoid detection. To figure out if RegAsm.exe process is legitimate or malware, there are a few steps you can take:
1. Checking the location of the file:
The default location of the RegAsm.exe file on Windows 10/11 systems depends on the version number of the Microsoft .NET Framework.
Default is:
C:\Windows\Microsoft.NET\Framework64\[version]\RegAsm.exe
(“version” – is the version of the .NET Framework, for example, v4.0.30319 for .NET Framework 4.5 and above.)
To verify the presence and exact location of RegAsm.exe on your computer, you can use the search function in Windows Explorer or run the following command at the command line (CMD):
dir C:\ /s /b | findstr RegAsm.exe
This command will also search for the RegAsm.exe file across the entire C drive, showing full paths to files that match the search criteria. If the file that you’ve encountered in the Task Manager has a different location, this may be a sign of malicious activity.
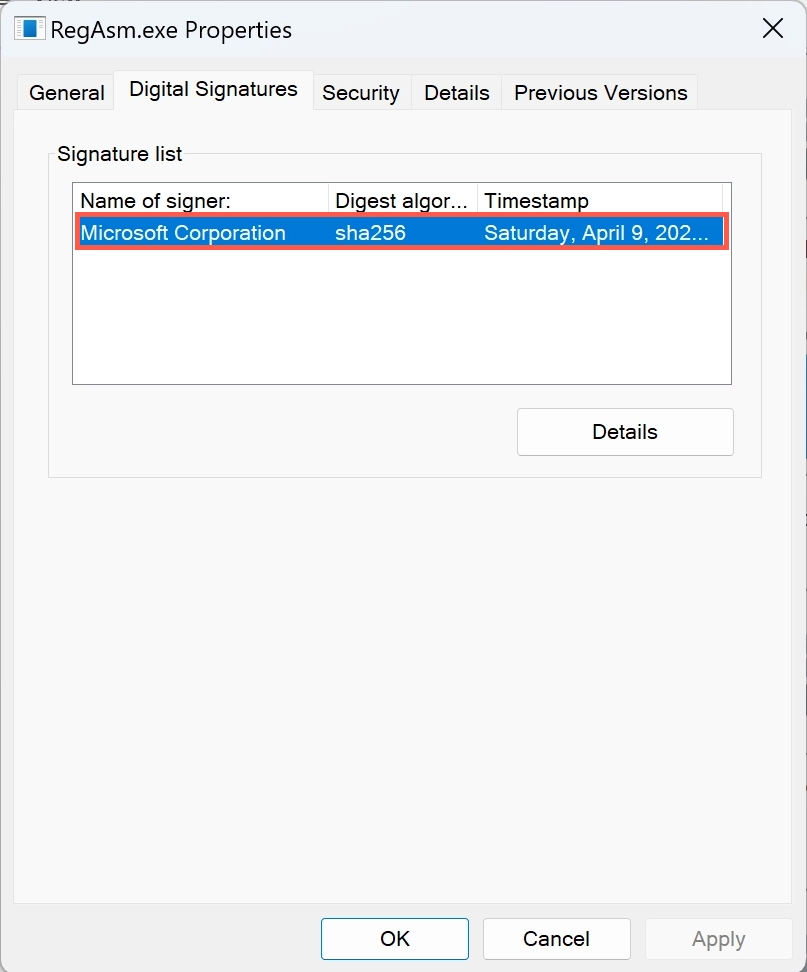
2. Digital signature verification:
Legitimate Microsoft files usually have a digital signature indicating their origin. Checking the file signature in the properties can show whether the file is edited or not.
Also RegAsm.exe can be used by attackers to register malicious assemblies on the system. Malicious code registered as a COM server can be invoked by other applications, potentially compromising the system. It is especially dangerous if an attacker gains access to an account with administrative privileges.
Can I remove RegAsm.exe from my PC?
Uninstalling RegAsm.exe is not a recommended action, as it is a standard and important component of Microsoft .NET Framework in the Windows system registry. This action may disrupt the functionality of applications that depend on this utility and may cause software errors on computer.
But if you are absolutely sure that RegAsm.exe has been modified or replaced by a malicious program, then you can remove the malicious copy of the file. However, you should not remove the legitimate utility itself.
The best way to remove malware is to use antivirus software, which can also scan for and remove other threats. GridinSoft Anti-Malware is such software. It will easily find the suspicious file and remove it.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.





