If you’re seeing PUA:Win32/Packunwan detected by your antivirus, don’t panic. Your computer might be running slower than usual. You’re seeing annoying ads pop up everywhere. Your browser homepage changed without permission. Strange programs are starting up with Windows.
This guide will help you remove this unwanted software completely. Follow these step-by-step instructions to eliminate the threat. We’ll start with manual methods you can try right now.
| Detection Name | PUA:Win32/Packunwan |
| Threat Type | Potentially Unwanted Application (PUA), Packed Malware |
| Detection Source | Microsoft Defender, Windows Security |
| Primary Function | System information collection, unwanted advertisements, browser modification |
| Common Sources | Freeware bundles, cracked software installers, fake driver updaters |
| Potential Payloads | Adware, browser hijackers, system information stealers, additional PUAs |
| Risk Level | Medium to High – Can lead to privacy compromise and system instability |
Packunwan usually comes bundled with free software downloads. It disguises itself as a helpful driver updater. The program is packed and encrypted to hide from antivirus software. This makes it harder to detect and remove.
What is PUA:Win32/Packunwan?
PUA:Win32/Packunwan is not your typical adware. It does much more than show unwanted ads. The program collects way too much information about your system. It tracks your browsing habits. It changes your browser settings without asking.
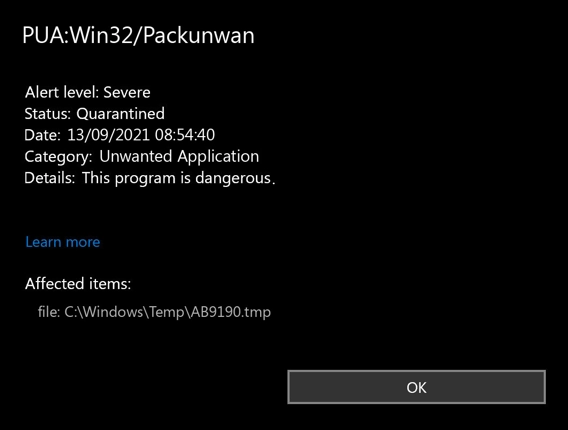
You might notice your homepage changed to something you didn’t choose. Your default search engine is different. Pop-up ads appear constantly. Your computer feels sluggish. These are classic signs of browser modification threats.
The program also behaves like information stealing malware. It gathers system details, location information, and installed software lists. This data collection happens in the background without your knowledge.
Manual Removal Steps
Manual removal takes time but works well if you follow each step carefully. Start with these methods before trying automatic tools. You can remove Packunwan yourself with some patience.
Step 1: Preparation
Restart your computer in Safe Mode first. This prevents Packunwan from running while you remove it. Safe Mode loads only essential Windows processes.
- Press Windows key + R to open Run dialog
- Type “msconfig” and press Enter
- Go to Boot tab and check “Safe boot”
- Select “Minimal” option
- Click OK and restart your computer
Back up your important files before starting. Create a restore point in case something goes wrong. This gives you a safety net during the removal process.
Step 2: Identify Malicious Processes
Open Task Manager to find suspicious processes. Packunwan often runs multiple processes with random names. Look for processes using high CPU or memory.
- Press Ctrl + Shift + Esc to open Task Manager
- Click on “More details” if needed
- Look for processes with strange names or no publisher
- Check processes using high CPU or network activity
- Right-click suspicious processes and select “End task”
- Note down the process names and file locations
Step 3: Remove Malicious Programs
Check your installed programs list. Packunwan might appear under a different name. Look for recently installed programs you don’t remember downloading.
- Open Settings (Windows key + I)
- Go to Apps > Apps & features
- Sort by “Install date” to see recent installations
- Look for suspicious programs with generic names
- Uninstall any programs you don’t recognize
- Also check Control Panel > Programs and Features
Common fake names include driver updaters, system optimizers, and PC cleaners. Remove anything that sounds too good to be true.
Step 4: Delete Malicious Files
Packunwan creates files in common Windows directories. Delete these files manually if you found them in Task Manager. Check these locations:
C:\Users\[Username]\AppData\Local\Temp\C:\Users\[Username]\AppData\Roaming\C:\ProgramData\C:\Windows\Temp\C:\Program Files\(check for suspicious folders)C:\Program Files (x86)\(check for suspicious folders)
Be careful when deleting files. Only remove files you’re sure are malicious. When in doubt, scan the file first with Windows Defender.
Step 5: Clean Startup Programs
Remove Packunwan from your startup programs. This prevents it from running when Windows starts. The malware often adds multiple startup entries.
- Press Ctrl + Shift + Esc to open Task Manager
- Go to “Startup” tab
- Look for suspicious programs with “High” startup impact
- Right-click and select “Disable” for unknown programs
- Also check Windows key + R, type “shell:startup”
- Delete any suspicious shortcuts in the startup folder
Step 6: Registry Cleanup
Packunwan creates registry entries to maintain persistence. Remove these entries to prevent it from coming back. Be very careful with registry editing.
- Press Windows key + R, type “regedit”
- Navigate to these locations:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce- Delete any suspicious entries pointing to Packunwan files
Create a backup of your registry before making changes. Export the registry keys before deleting them. This lets you restore them if needed.
Step 7: Check Scheduled Tasks
Packunwan might create scheduled tasks to restart itself. Remove these tasks to stop the malware from returning.
- Press Windows key + R, type “taskschd.msc”
- Open Task Scheduler
- Look through the task list for suspicious entries
- Check tasks that run frequently or at startup
- Delete any tasks related to Packunwan
Step 8: Clear Browser Data
Packunwan tracks your browsing and modifies browser settings. Clear all browser data to remove tracking cookies and reset changes.
- Open each browser you use
- Clear all browsing data, cookies, and cache
- Reset browser settings to defaults
- Remove any unknown browser extensions
Browser Cleanup
Packunwan often installs browser extensions and changes settings. These changes can persist even after removing the main program. Clean your browsers thoroughly.
Remove Malicious Browser Extensions
Check all your browsers for suspicious extensions. Packunwan might install extensions that look legitimate but track your browsing.
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect browser-based changes from Packunwan, reset your browser completely. This removes all modifications and starts fresh.
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
- Choose Reset and Clean up and Restore settings to their original defaults.
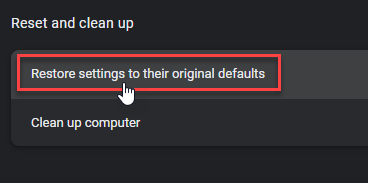
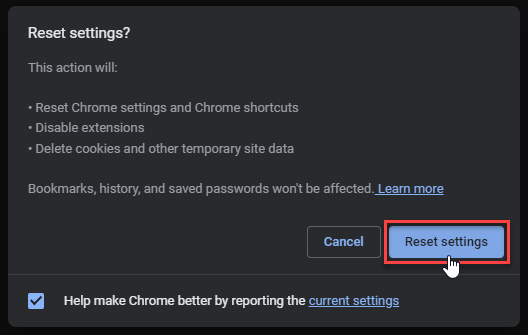
- Tap Reset settings.
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
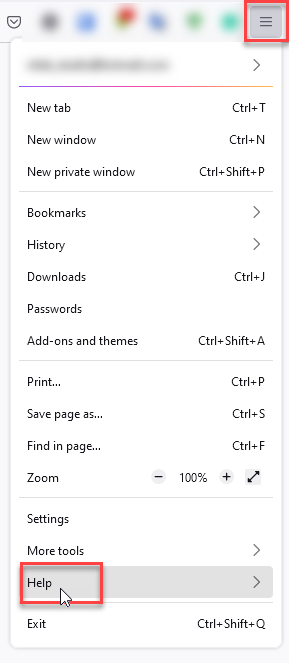
- Choose More Troubleshooting Information.
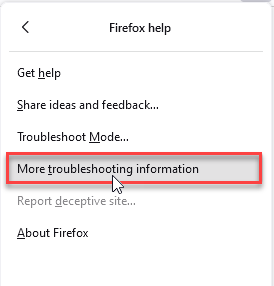
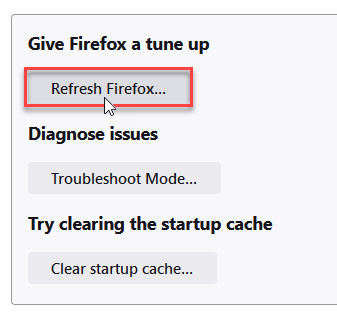
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
How Packunwan Works
Understanding how Packunwan operates helps you recognize similar threats. The malware uses several techniques to avoid detection and maintain persistence.
System Information Collection
Packunwan gathers extensive system information. It checks your computer’s location settings for no clear reason. This behavior is typical of other PUA families.
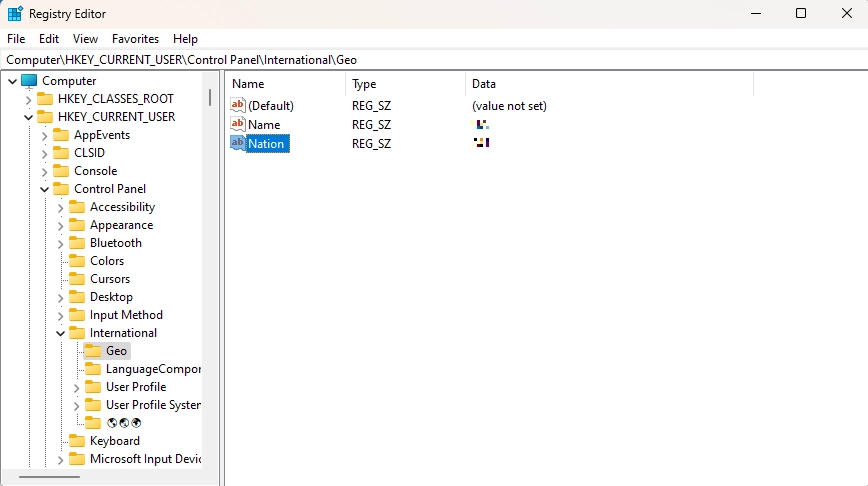
The program queries registry entries for country codes and system configurations. It builds a profile of your system and location. This information could be valuable to cybercriminals.
Packunwan also checks for virtual machines and sandbox environments. It queries SCSI registry keys to detect analysis tools. This anti-analysis technique is common in modern malware.
Packing and Obfuscation
The malware uses RC4 encryption to hide its payload. Packing makes the program harder to analyze and detect. It also helps bypass basic antivirus protection.
Packunwan creates files with misleading extensions. It disguises malicious files as legitimate system components. This tactic is similar to fake system optimization tools.
Network Communications
The program creates excessive network traffic. It contacts remote servers frequently for unclear reasons. This behavior suggests it might download additional payloads.
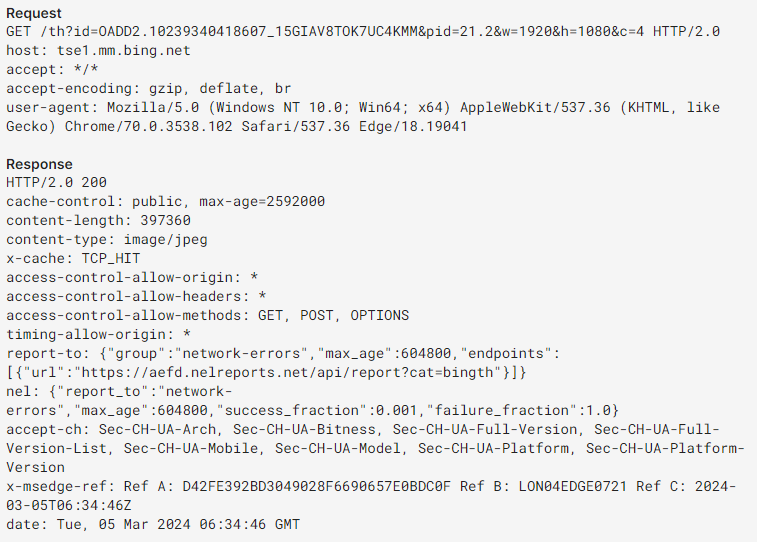
Legitimate driver updaters don’t generate this much network activity. The excessive communications suggest Packunwan does more than advertised. It might be downloading additional threats or reporting collected data.
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of packed malware like Packunwan. Professional anti-malware software can find hidden components and registry changes that you might miss.
Automatic tools are especially helpful with packed malware. They can unpack and analyze encrypted payloads. This gives you complete removal without manual registry editing.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

How to Prevent Future Infections
Preventing Packunwan infections is easier than removing them. Follow these simple practices to keep your computer safe.
Avoid Fake Driver Updaters
Never download driver updaters from unknown websites. Windows Update handles most driver updates automatically. Use official manufacturer websites for specific drivers.
Be suspicious of programs that claim to fix multiple system problems. These “all-in-one” tools often contain potentially unwanted applications. Stick to well-known, reputable software.
Be Careful with Free Software
Free software often comes with unwanted extras. Always choose custom installation when downloading freeware. Read each installation screen carefully.
Avoid software bundles that include “recommended” programs. These bundles often hide malware like Packunwan. Similar tactics are used by unwanted programs and bundler families.
Keep Your Security Software Updated
Enable Windows Defender real-time protection. Keep your antivirus definitions updated. Real-time protection can block Packunwan before it installs.
Consider using additional security layers. Browser-based protection can block malicious download sites. This prevents infections from online scam patterns.
Regular System Maintenance
Run regular system scans to catch threats early. Check your installed programs monthly. Remove software you don’t use or recognize.
Monitor your system performance. Sudden slowdowns or strange behavior might indicate malware. Early detection makes removal much easier.
Frequently Asked Questions
What is PUA:Win32/Packunwan and why is it dangerous?
Packunwan is a potentially unwanted application that collects system information and displays unwanted ads. It’s dangerous because it tracks your browsing, changes browser settings, and might download additional malware. The program uses packing and encryption to hide from antivirus software.
How did PUA:Win32/Packunwan get on my computer?
Packunwan typically comes bundled with free software downloads, cracked programs, or fake driver updaters. It installs when you download software from untrustworthy websites or click on fake system optimization ads. The program hides its installation in “recommended” software bundles.
Can I remove PUA:Win32/Packunwan manually?
Yes, you can remove Packunwan manually by following the steps in this guide. Start by uninstalling suspicious programs, then clean your browser, remove startup entries, and delete malicious files. Manual removal takes time but works if you’re careful and thorough.
Is it safe to delete Packunwan processes and files?
Yes, it’s safe to delete Packunwan processes and files. The program doesn’t provide any legitimate functionality despite claiming to be a driver updater. Removing it will improve your system performance and protect your privacy. Use Windows Update for legitimate driver updates instead.
How can I prevent Packunwan and similar threats?
Avoid downloading software from unknown websites, especially driver updaters and system optimizers. Always choose custom installation for free software and read each screen carefully. Keep Windows Defender enabled and updated. Only download software from official sources.
What if manual removal doesn’t work completely?
If manual removal doesn’t work or if Packunwan keeps coming back, use GridinSoft Anti-Malware for automatic removal. Professional anti-malware tools can find hidden components and packed payloads that manual removal might miss. They also clean registry entries more thoroughly.
Why does Packunwan collect so much system information?
Packunwan collects system information to build a profile of your computer and location. This data might be sold to other cybercriminals or used to target you with specific scams. The extensive data collection goes far beyond what a legitimate driver updater would need.
Can Packunwan steal my personal information?
Yes, Packunwan can access personal information through its browser tracking and system information collection. It monitors your browsing habits, collects location data, and catalogs installed software. While not technically spyware, it crosses privacy boundaries without your consent.
Indicators of Compromise
Use these indicators to identify Packunwan infections on your network or system. Security professionals can use this information for threat hunting and detection.
- PUP.Win32.Packunwan.bot: ecef8b1c9dd550b1489657395895161f17a8e8f68f33ac9547f5c03dc7efe66f
- Malware.Win64.Packunwan.cl: d1ff7034fe046470ae9608c606ae080ce5b75ac5ba95ffcbd14480ba1c6e7a3e
- Malware.Win32.Packunwan.cl: 19abf6dbcc035b408efe6e717f0e52e55174a178fc3f85196af434c371a3e3b1
- PUP.Win32.Packunwan.bot: a79ea553a54f1681bc9282076b5e66df0775c434f8da71029e15972e7fca3873
- PUP.Win32.Packunwan.bot: a7fecfc225dfdd4e14dcd4d1b4ba1b9f8e4d1984f1cdd8cda3a9987e5d53c239
- PUP.Win32.Packunwan.mz!n: 5c2d11f8eba4b3e7b41c95dfef4314dd72ee30273cce999d74da09e29eeb7c3f
- Malware.Win32.Packunwan.sa: f917dfe20a29f8a887ba9ebaaa096bb1fef9d7a1512e4f8590d2afcd751f0385
- PUP.U.Packunwan.bot: 1f72bcae890c0b9197be2b3f20ff984f6ba50c9459509176390cdc30111dc4a0
- PUP.Win32.Packunwan.ca: 8e064b8cd910bc554cfac28568c9b71abc07f405f71b91ff5cbd8b6488e617f5
- PUP.Win32.Packunwan.bot: e9b75ffe66b19fed9594e79730eb6bcecf4ea8bc648585cb76a0c53961486c03
Conclusion
PUA:Win32/Packunwan represents how unwanted software has evolved beyond simple adware. It uses sophisticated techniques like packing, anti-analysis, and extensive data collection. These features make it closer to malware than traditional potentially unwanted programs.
You can remove Packunwan using the manual steps in this guide. Focus on removing the program from your system completely, cleaning your browsers, and preventing future infections. Be thorough with each step to ensure complete removal.
For faster and more reliable removal, consider using professional anti-malware software. Automatic tools can handle the technical aspects while you focus on prevention. Remember that staying safe online requires constant vigilance and good security practices.
If you’ve found this guide helpful, you might also want to read about other PUA families, software bundling tactics, and general malware facts. Understanding these threats helps you recognize and avoid them in the future.