A new Windows malware called Ov3r_Stealer is spreading through fake Facebook job ads, according to a report by Trustwave SpiderLabs. The malware is designed to steal sensitive information and crypto wallets from unsuspecting victims. Let’s delve into the mechanics of these deceptive ads, and Ov3r_Stealer.
Ov3r_Stealer Abuses Facebook Job Ads
Scammers use elaborate job ads posted on Facebook. These seem legitimate at first glance and target a wide range of job seekers with the promise of lucrative opportunities. As the experts at Trustwave clarify intruders use a PDF file that masquerades as a legitimate document hosted on OneDrive. Prospective victims are lured into clicking an “Access Document” button embedded within the PDF, which initiates a chain of malicious events.

The Ov3r_Stealer infection chain is a sophisticated cyber system designed to compromise systems and steal sensitive data. Being a rather classic infostealer, it primarily attracts attention due to the unusual way of propagation. It begins with deceptive tactics, ensuring persistence for data collection and stolen crypto. The infection chain is next:
1. Initial Access
To direct the victim to the surprise PDF, a fake Facebook account posing as Amazon CEO Andy Jassy is created with a link to OneDrive. After clicking “Access Document” from the Facebook page, a .url file is downloaded, which starts the second step.
2. Payload Downloading
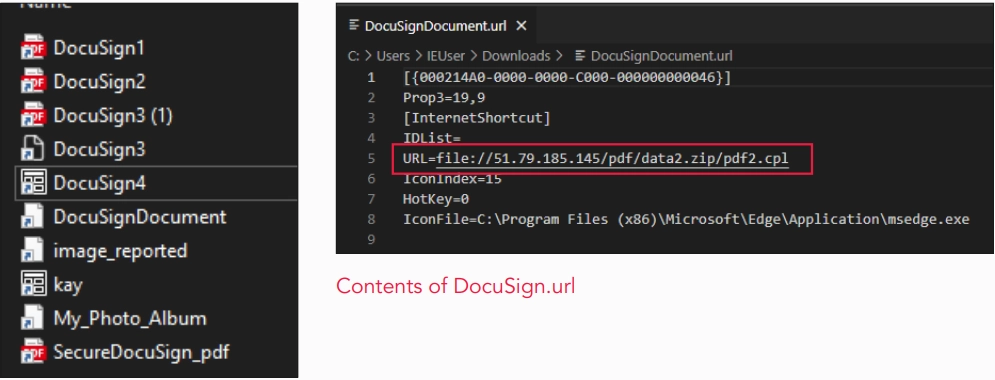
After clicking on the Access Document button, the victim is taken to a .url file to download. It is masquerading as a legitimate ‘DocuSign’ document. The .url file directs to an IP address with a pdf2.cpl file inside the data2.zip archive on the remote host. Since this is a Windows Panel (.cpl) file, Windows allows this operation. Further, the final payload of this malware is also targeted at Windows-based systems.
3. Additional Loaders
At this stage, the malware may utilize additional loaders or components to further execute and propagate. The loaders are used to facilitate the installation and execution of the final payload, allowing the malware to function efficiently and effectively in the compromised environment.
4. Final Payload
There are three files that make up the final payload, and each loader stage brings them in: WerFaultSecure.exe, Wer.dll, Secure.pdf. Once executed, the malware will establish persistence to ensure it is always running and exfiltrate specific data to a monitored Telegram channel.
5. Gaining Persistence
To ensure its continued presence and operation within the compromised system, the malware establishes persistence mechanisms. This may involve modifying system settings, creating registry entries, or scheduling tasks to ensure that the malware remains active and operational even after system reboots or security scans.
6. System Surveillance & Data Collection
Once established within the compromised system, the malware begins collecting sensitive data and discovering valuable information. This stage may involve scanning the infected device for credentials, cryptocurrency wallets, and other valuable data, as well as identifying potential targets for further exploitation.
7. Data Exfiltration
The final stage of the malware operation involves exfiltrating stolen data from the compromised system to external servers or channels controlled by the attackers. This may include transmitting sensitive information such as credentials, financial data, or proprietary information to remote locations, enabling the attackers to harvest and exploit it for nefarious purposes.
Similarities with Phemedrone Stealer
Experts note that Ov3r_Stealer shares some similarities with another stealer malware called Phemedrone Stealer, which we covered recently. Both malware use the same GitHub repository (nateeintanan2527) and the same infection chain involving PDF files, URL files, CPL files, and PowerShell loaders. They also exploit the same Microsoft Windows Defender SmartScreen bypass flaw (CVE-2023-36025) to evade detection. There is actually one more malicious program that exploits the same SmartScreen Vulnerability, dubbed Mispadu – check out our report.
(Source: Trustwave)
The only serious difference between the subject and a Phemedrone is that the latter is written in C#, while Ov3r_Stealer is written in C++. The report suggests that Phemedrone may have been re-purposed and renamed to Ov3r_Stealer by the same or different threat actors. Either way, such similarities are rarely a coincidence in the malware world.
How to Protect Against Malware in Ads?
Malware that spreads through advertisements is nothing new, thus the recommendations and effective counteraction measures are well elaborated. As major ad providers struggle (or are unwilling) to filter malicious ads, the best option is to avoid interacting with them at all. If the thing from the banner attracted your attention, it is better to go check it by yourself. Benign advertisers always mention their website either on the banner or in the description, so you won’t get lost there.
A more reactive though more reliable and relaxed approach is using advanced anti-malware software. Stealer malware rely on stealthiness, but they can barely disguise their malignant activity – and here is where heuristic detection shines. With its advanced Proactive Protection mode, GridinSoft Anti-Malware will be able to prevent malware infections at their very beginning.





