On October 28, 2024 Dutch cyber police launched a website reporting a massive success in their recent anti-cybercrime activity, following Operation Magnus. Law enforcement managed to take over and disable the vast majority of infrastructure belonging to two infostealer programs – RedLine and META. The main part of the operation took part in the Netherlands and Belgium.
RedLine and META infostealer malware disrupted in Operation Magnus
Under the course of Operation Magnus, law enforcement agencies of 6 countries – US, Australia, Germany, UK, Belgium and Portugal, managed to take down Web infrastructure of infostealer viruses and arrest two individuals involved in malware operations. The information, along with a lot of details, comes from the official website of the operation, established swiftly after its finish.
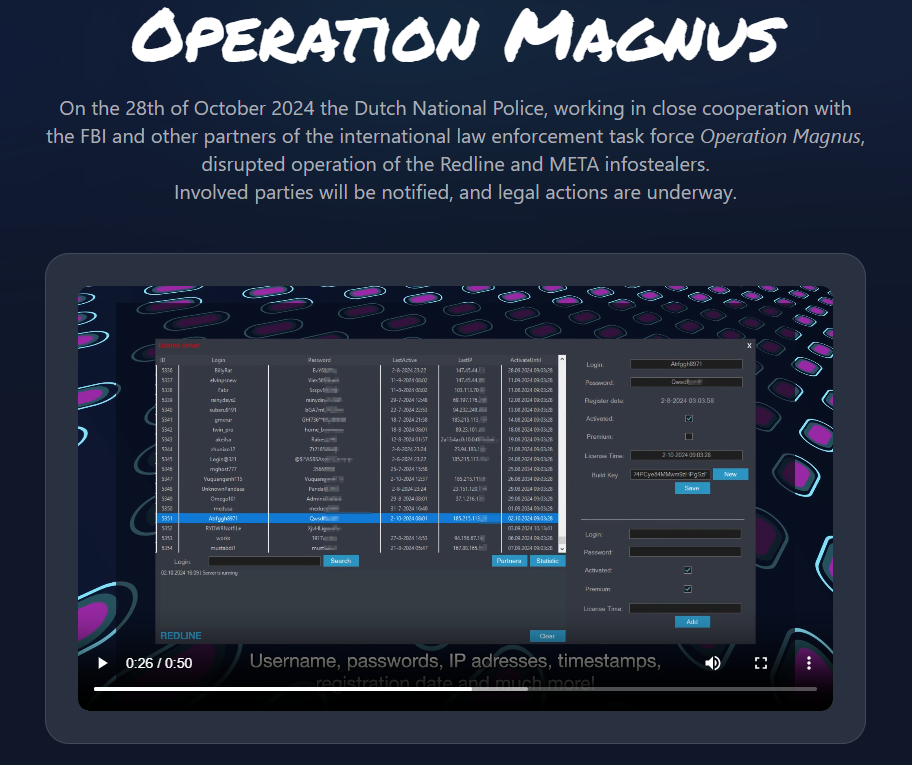
The website features an interesting video, with the recordings of what they’ve managed to capture during the operation. Among other things are source codes of the malware, all access credentials for C2 panels, Telegram bot, and all the server infrastructure required to handle the malware users.
According to this exact video, law enforcement agencies apparently get their hands into the infrastructure much before disrupting the operations, and slipped in a forged update. This update, in turn, leaked all the important information of malware users (i.e. ones who bought the subscription and used it to spy on people). Such data will be quite handy for cyber police to find and detain the attackers.
And that is exactly what the promise to do, at least according to the video. It ends with the lines “Thank you for installing this update. We are looking forward to seeing you soon!”, with an icon of cuffed hands in the middle.

This operation in its core principles aligns with the tactic that law enforcement all around the planet opted for in their effort against cybercrime. Instead of chasing headmasters of malware operations, they disrupt infrastructure, collect all the available data and detain all the malware operators who come by. This tactic allowed disrupting operations, though temporarily, of even the toughest malware groups like QakBot and LockBit.
Two Hackers Arrested, 1200 Servers Taken Down
The overall network infrastructure of two malware families consisted of over 1200 servers, located in multiple countries around the world. Getting access to all of them was actually the reason for involving such a significant number of law enforcement agencies from different countries.
Key initiator of the campaign is Eurojust, who coordinated the effort in different parts of the world. Aside from disabling that huge amount of virtual servers, Netherland’s National Police managed to get 2 physical servers – a much more valuable asset in terms of pushing the investigation further.
In Belgium, Federal Police arrested two people accused of managing the network infrastructure. Their personalities as well as actual roles in malware operations are to be disclosed, but I guess they are far from being top management of the malware gang. It is well known that RedLine originated from Russia, and it is highly likely for META infostealer to be a similar story.
What are these infostealers?
RedLine and META viruses are both infostealers that target at collecting as much user information as possible. Online account credentials, session tokens, cookies, crypto wallet information – they pick everything they can reach to on the attacked machine, and then stay in to eavesdrop on possible other info.
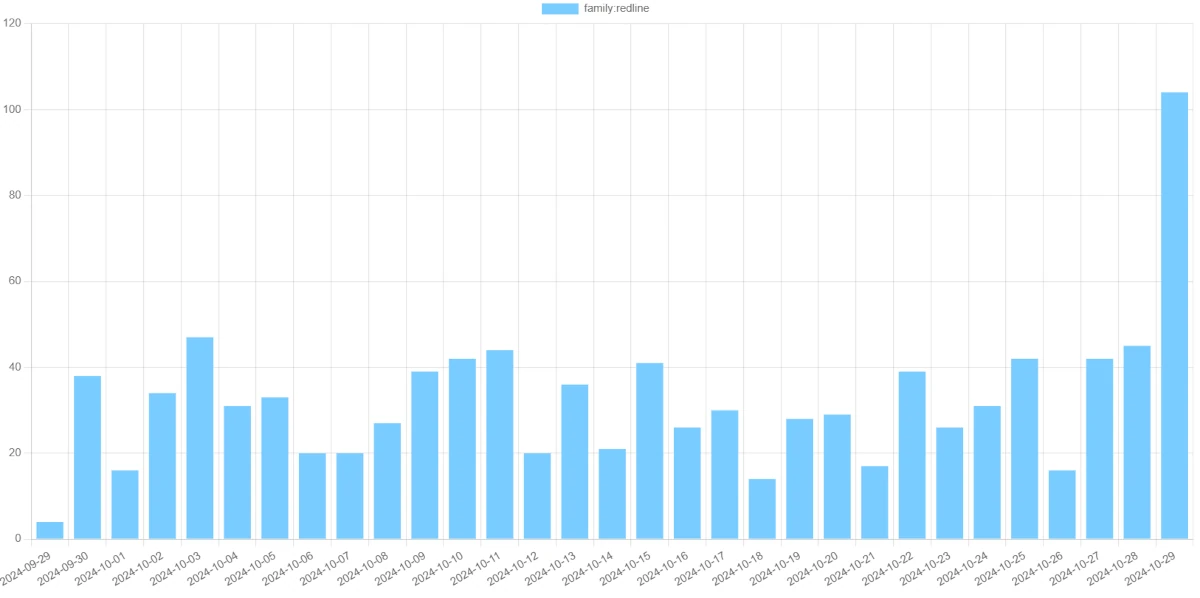
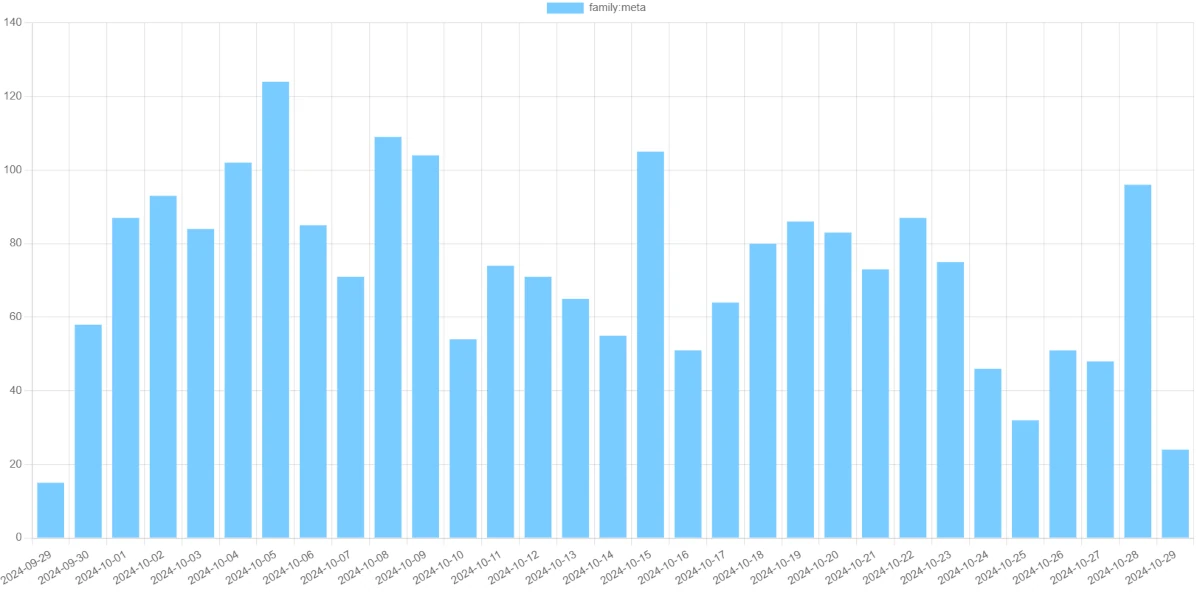
Both malware samples are pretty widespread, with RedLine reaching over 50 infections daily. Though, this is far from its prime-time: back in the days, new infections appeared in hundreds per day. META lastly had higher volumes of infection recently, though due to its shorter activity span, there is not too much to say about its past.
As Operation Magnus turned out, the viruses are pretty much the same in terms of codebase, exactly, META repeated the older RedLine infostealer. Such rebranding is a common practice among different malware families, especially when one of the developers leaves the project and decides to start over under a different name. Though, no such things were happening around RedLine recently, so there’s no clear understanding why this happened.