Online scams have existed in one form or another since the advent of the internet itself. As the Internet has evolved, scammers have devised new ways to deceive users, and what was relevant ten years ago may not be applicable today. In this post, I have compiled the most current types of online scam and their identifying features.
Fake Shop Online Scam
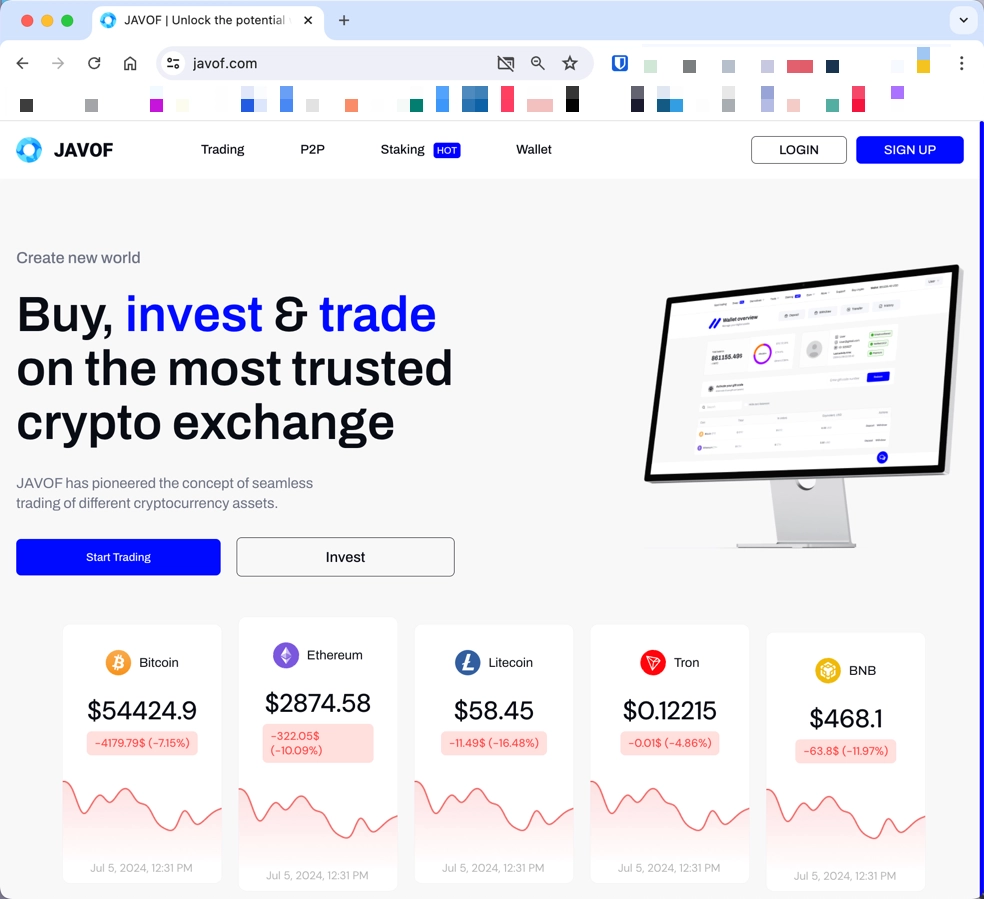
Among all the online scams one that I stumble by particularly often is fake online stores, which today are perhaps the most common type of scam. This is not surprising, as the events of the last 4 years have given a significant boost to e-commerce and online shopping. Unlike legitimate stores, these shops will never send you any goods whatsoever, or, in the best case scenario, just a cheap counterfeit from China. The reason is that the store essentially does not exist. If you have a more detailed look, you will see just a landing page made with a template that contains pictures stolen from other sites and a payment form.
The main signs that a store is fake include overly huge discounts (usually between 50% and 95%) and urgent calls to act quickly (such as “3 hours 59 minutes left in the sale” or “only 4 items left at this price”).This is obviously false, and you may see the countdown resetting upon refreshing the page. Another sign is exclusively positive reviews combined with the inability to leave your own feedback. Also the “About Us” and “Contact Us” pages have some distinctively senseless text. It often contains vague, abstract text, and sometimes this section is unfilled at all. The contact form may also list (if at all) the address of a random pavilion in China and a nonexistent email address.
To make the scam page more visible, con actors launch aggressive advertising campaigns, typically on social media. They often prefer Facebook to other platforms for its massive audience and well-known advertising engine. Interestingly enough, the latter, albeit having sturdy protection against traffic arbitrage, shows a rather poor counteraction to this type of scam.
How Does it Work?
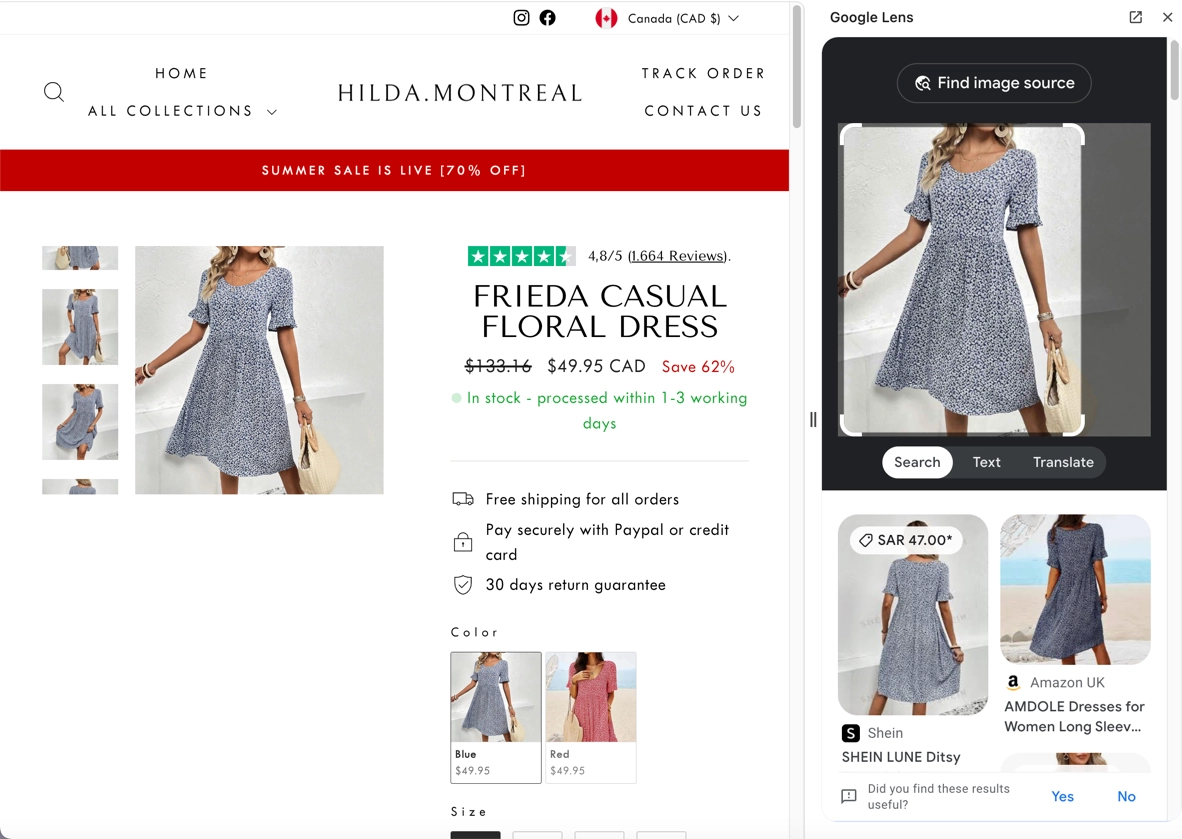
Allow me to briefly explain how this works: using online website builders, crooks create themed online store templates, typically for clothing, shoes, home decor or other popular items. All product photos are usually taken from legitimate online stores; you can verify this by performing a reverse image search. Scammers register it on the cheapest domains like .site, .top, .fun, or .store, and then just wait for the victims to come by. Typically, these are one-day sites that do not stay online for long.
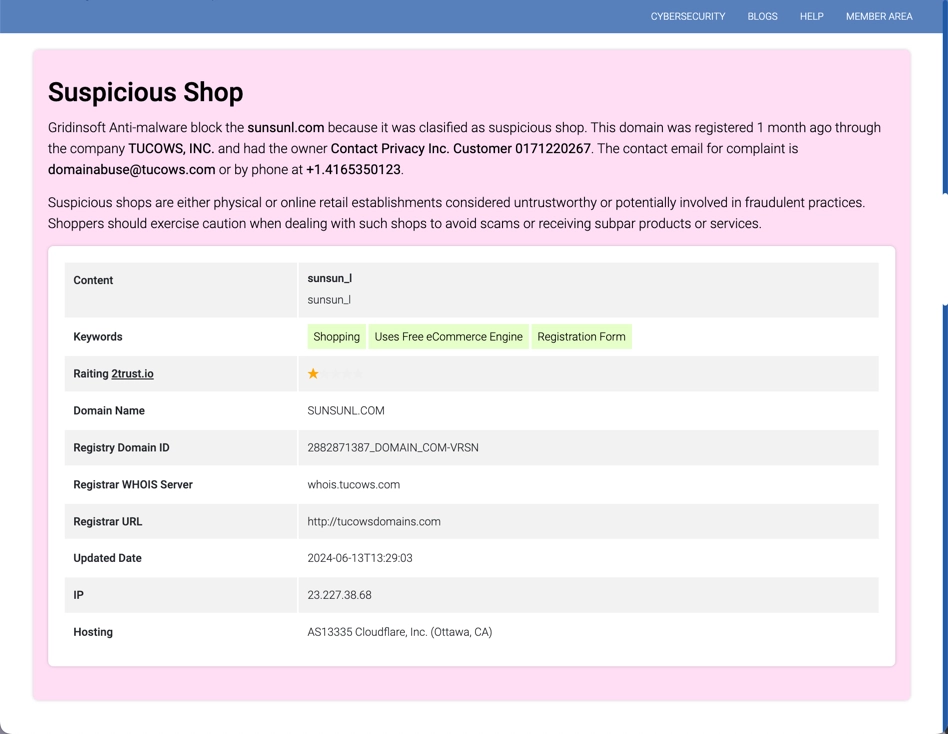
The only functional button on such a site is the “buy” button, which, once clicked, prompts you to enter the recipient’s address and pay for the item. Obviously, no one will send the item. Even when the buyer actually receives something, as I said, it is usually the cheapest replica from Temu or Aliexpress. Some scammers even surprise by sending a box of trash instead of the expected package or an old T-shirt instead of a branded one.
Potential Risks
There are several risks involved here. Firstly, you risk losing your money. Although these sites often guarantee a money-back, be sure, no one will refund your money. The second risk is the exposure of confidential information. Scammers obtain all the details — full name, home address, email, and card information. This is a great jackpot for crooks, who may later attempt to use this information for further scams. In some cases, these details may be sold on the Darknet.
If you have fallen victim to a fraudulent online store, it is important to take the following steps to minimize damage and attempt to recover your money. First, contact your bank and report the fraud. This might help to get your money back. Then, disable the option for online payments on the card you entered on the fake site. If possible, take screenshots of all transactions and any correspondence with the seller (if any).
Crypto Scams
Another prevalent type of online scam is cryptocurrency fraud. This works almost the same way as in the previous example. Scammers use templates to create many identical websites that differ only by name. These sites often associate themselves with celebrities, such as Elon Musk, Bill Gates, Vitalik Buterin and other renowned persons of the crypto world.
These sites operate in several different modes: as exchangers, trading platforms, or airdrop scams. Modus operandi of all of them is rather simple: pretending to be something, while not being it, and instead either stealing users’ money, cryptocurrency and personal data.
The main risk of this scam is the scammers withdrawing funds from your wallet. By gaining access to your private keys, scammers can easily transfer all your funds to their addresses. In the case of fake airdrop distributions, the website may use a smart contract with malicious code. After connecting, the “drain” script activates, automatically transferring all funds from the connected wallet to the scammer’s wallet. They also happily help themselves to the data that users leave during authentication. Such manipulation may end up with identity theft in future.
Targeting Ways
Main promotion ways for crypto scams differ from ones used by other scams. Frauds typically launch massive ads through TikTok, Instagram and other similar platforms with short content. By abusing indexing mechanisms these platforms use, they can reach an enormously wide audience in just a few days.
If you become a victim of a crypto scam, you must gather evidence. Take screenshots of all transactions, any correspondence (if available), and related websites. Then, contact the bank authority and the service that provided you with the hot wallet. You can also contact their support team to get more detailed instructions on how to report the fraud. After all, change your account login details, especially if you use that password on more than one site.
Online Scam: Phishing
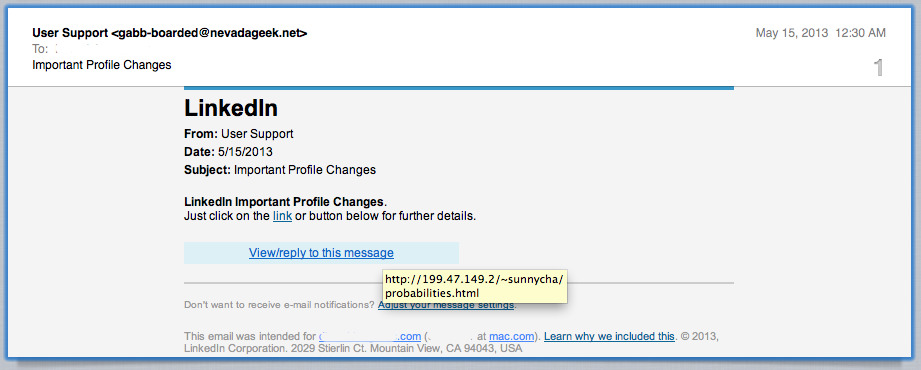
One of the oldest types of online scam is phishing. This attack relies not on technical, but human factors, which in fact makes up for its longevity and effectiveness. Scammers create exact replicas of the login pages for popular legitimate services. Most commonly, these are Microsoft Azure, Apple ID, Amazon, PayPal, and less frequently, social media.
These pages look identical to the real ones, but almost always have a different URL. The most recent phishing scams, as of mid-2024, are hosted on Microsoft Azure service, which adds a well-noticeable particle in URL. This is also the reason why phishing scams bypass most of the filters. Such are extremely short-living, staying online for just a few days.
Falling for this scam risks giving your login credentials to scammers, which can lead to further problems. This could result in losing access to your account, as scammers may log in and try to change the password. If you use the same password for multiple accounts, the security of those accounts is also at risk.
One particular promotion ways phishing scams exploit for all the time is email spam. Crooks that stand behind all this launch a mass-mailing campaign that comes to the users as a routinely-looking message which asks to update some stuff related to the account. The link to the phishing site is additionally masked by anchoring it to a piece of text that contains the legitimate URL.
If you become a victim of phishing, regardless of the account type, the first thing to do is change your password. This action will block the scammers’ access to your account. Next, enable two-factor authentication (2FA) on any accounts that might have been compromised if not already enabled. I recommend using 2FA wherever possible.
Fake Job Online Scam
Fake job scams is a particularly novice type of online scam that targets people searching for employment. They particularly aim at ones seeking for a remote job – a rather widespread demand since 2020. Scammers that operate this kind of fraud stand off by being pretty inventive and avoiding using templated websites.
There are several types of this fraud that are met the most often. The first one involves performing simple online tasks for a reward. Tasks might include clicking on links, watching advertisements, or viewing videos. However, the pay for these tasks is so low that earning $10 could take a week of watching videos. In exchange, that site takes quite a lot of users’ personal information, and will likely sell it for much more than the pathetic sum they promise as the reward.
Social Media As a Communication
Another type of job online scam mostly takes place on social media. The victim stumbles upon a site that offers a “well-paid remote job” by seeing an ad on social networks like Facebook or LinkedIn. In most cases, the website the user sees appears legitimate, making it difficult to suspect anything wrong. Further, the site asks the victim to fill out a form on the website and provide information about themselves. In some cases, people may see the payment request, allegedly for handling document processing or training. After this payment, the site completely stops responding; all the ways to reach the site back appear non-functional. Scammers simply disappear with all the users’ personal data and, optionally, the payment.
The third variant of this scam resembles the first but differs in operation. Scammers find potential victims on social networks and offer them a good passive income opportunity. This involves performing simple interactions with a website daily, promising a good reward for these actions. Initially, victims are allowed to “withdraw” a small amount. Later, victims are encouraged to “upgrade their task level” by paying a certain fee. But once they do this payment, the cost of tasks increases. Scammers continually persuade the victim to upgrade again and again. When the victim attempts to withdraw funds at a certain point, the website simply starts spitting out errors. Scammers may reassure the victim that the issue will be resolved soon. Finally, they disappear, stop responding, and the website likely ceases to exist.
Potential Risks
In most cases of this type of online scam, all money transfers occur through cryptocurrency. This practically eliminates the possibility of retrieving funds or identifying the scammers. The main risk, however, is the leakage of personal information. Considering that people happily share SSN, ITIN and other sensitive documents, with fair expectation that it is needed for the job, the possible damage goes far beyond what other scams can do. Another edge of the risk is financial loss, a small one in the case of “document processing”, and a much larger one (up to several thousand dollars) with the “task updating” scheme.
You should practice basic internet hygiene to avoid falling victim to such scams. Approach any offers of easy money with suspicion. If you’re promised large sums for simple tasks, it’s likely a scam. The same, if you’re asked to visit a previously unknown website for job searching and fill out a form, don’t rush. Please perform your own research, Check the site on our URL checker, Google it, and read reviews. In most cases, this will shed light on the situation.
If you’ve become a victim of such a scam, first stop communication and block the scammer. Then, report the user on the platform where they contacted you. Find the website on review platforms and leave a detailed review describing your situation to warn other users. If you’ve provided confidential information (like credit card details), block the online payment option and inform your bank that your card details have been compromised. This will prevent unauthorized transactions using your card. If you’ve entered your passwords anywhere, change them immediately.