Octalyn Stealer is an information-stealing malware that’s currently being promoted on GitHub – because apparently, even cybercriminals believe in open-source development these days. Contrary to initial reports, this malware is actually written in Pascal/Delphi with a user-friendly control panel, making it accessible even to less technically skilled cybercriminals. This isn’t your garden-variety trojan that just sits around looking menacing. It’s designed with one clear purpose: to systematically extract and exfiltrate your sensitive data.
- The Telegram Connection: A New Twist
- What Does Octalyn Stealer Actually Steal?
- How Does Octalyn Stealer Spread?
- Technical Analysis: Under the Hood
- YARA Rules for Detection
- Detection Names and Technical Details
- Signs Your System Might Be Infected
- How to Remove Octalyn Stealer
- The Bigger Picture: The Democratization of Cybercrime
- What to Do If You’ve Been Compromised
- The Bottom Line
The malware targets Windows systems from XP all the way up to Windows 11, which means it’s not particularly picky about its victims. Whether you’re running that ancient XP machine in your garage or the latest Windows 11 setup, Octalyn doesn’t discriminate – it’s an equal opportunity data thief.
The Telegram Connection: A New Twist
What makes this particular variant interesting is its integration with Telegram for data exfiltration. The “Telegram version” of Octalyn Stealer uses Telegram’s bot API to send stolen data directly to the attacker’s Telegram account. This approach is clever because:
- Telegram traffic appears legitimate to most network monitoring tools
- It’s harder to block than traditional command-and-control servers
- The communication is encrypted by default
- It provides real-time notifications to cybercriminals when new victims are compromised
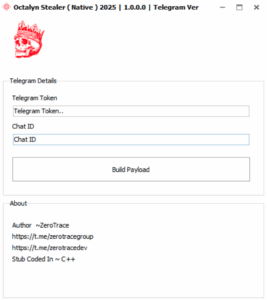
The GitHub repository shows a polished interface where attackers can configure their Telegram bot token and chat ID, making the whole operation disturbingly user-friendly.
Octalyn-Stealer-C-Telegram/
├── OctalynStealer.sln # Visual Studio solution file
├── OctalynStealer/ # Main project directory
│ ├── Program.cs # Main entry point for the application
│ ├── Properties/
│ │ ├── AssemblyInfo.cs # Assembly metadata
│ ├── Config/
│ │ ├── Settings.cs # Configuration for Telegram bot (e.g., bot token, chat ID)
│ │ ├── telegram.txt # Output file for Telegram configuration (generated post-build)
│ ├── Modules/
│ │ ├── BrowserStealer.cs # Logic for stealing browser data (passwords, cookies, history)
│ │ ├── DiscordStealer.cs # Logic for extracting Discord tokens
│ │ ├── TelegramStealer.cs # Logic for extracting Telegram session data
│ │ ├── CryptoWalletStealer.cs # Logic for targeting cryptocurrency wallets
│ │ ├── FileGrabber.cs # Logic for collecting specific files
│ ├── Utils/
│ │ ├── Encryption.cs # Encryption utilities for data exfiltration
│ │ ├── Network.cs # Network utilities for sending data to Telegram
│ │ ├── AntiAnalysis.cs # Anti-sandbox/virtual machine detection
│ ├── bin/
│ │ ├── Debug/
│ │ │ ├── telegram.txt # Generated file for Telegram bot settings
│ │ │ ├── OctalynStealer.exe # Compiled executable
│ │ ├── Release/
│ ├── obj/ # Temporary build files
What Does Octalyn Stealer Actually Steal?
Here’s where things get interesting (and by interesting, we mean terrifying). Based on the source code analysis, Octalyn has quite an appetite for your personal information. It specifically targets:
Browser Data
- All stored passwords from Chromium-based browsers
- Non-expired cookies (perfect for session hijacking)
- Complete browsing histories and bookmarks
- Auto-fill information (usernames, personal details, addresses)
Cryptocurrency Assets
Because what’s a modern infostealer without crypto-stealing capabilities? Octalyn targets:
- Browser extensions: MetaMask, Phantom, BitPay, TrustWallet
- Desktop wallets: Exodus, Atomic
- Wallet files and private keys stored locally
Communication Platforms
Your private conversations aren’t so private anymore. The malware harvests data from:
- Discord: Tokens from both stable and Canary versions
- Messaging apps: Telegram, QTox, Signal, Skype, Viber
- Session tokens that can be used to impersonate you
Gaming Platforms
Even your gaming life isn’t safe. Octalyn goes after:
- Minecraft: Session and account tokens
- Steam: Account credentials and session data
- Epic Games: Launcher tokens
- UbiSoft Connect: Account information
- Growtopia: Account details
VPN and Security Software
It also targets Surfshark VPN credentials and configuration data, because apparently, your attempts at privacy are just another challenge to overcome.
How Does Octalyn Stealer Spread?
The distribution methods for Octalyn are as varied as they are concerning. Since the developers are promoting it on GitHub with detailed tutorials (including YouTube videos), different cybercriminal groups can pick it up and distribute it however they see fit. This means you could encounter it through:
- Phishing emails with malicious attachments
- Social engineering tactics designed to trick you into downloading it
- Software cracks and pirated programs – because that “free” Photoshop might cost more than you think
- Malicious online advertisements that redirect to infected downloads
- Infected removable storage devices like USB drives
The malware can disguise itself as legitimate software or hide within seemingly innocent files. It’s particularly fond of masquerading as popular applications or bundling itself with cracked software.
Technical Analysis: Under the Hood
Based on the GitHub repository analysis, Octalyn Stealer consists of two main components:
The Client/Stub (Pascal/Delphi)
- Compiled with optimization flags for maximum speed
- Uses Windows API for file system and registry access
- Implements Winsock API for network communication
- Designed to be lightweight and stealthy
The Control Panel (Delphi)
- User-friendly GUI for configuring the malware
- Telegram bot integration for data exfiltration
- Real-time victim monitoring capabilities
- Cross-platform support (Windows and Linux)
The fact that there are instructional videos on platforms like YouTube showing how to use this malware demonstrates how the cybercrime landscape has evolved. It’s no longer just about technical expertise – it’s about making malware accessible to anyone with malicious intent.
YARA Rules for Detection
For security professionals and researchers, here are comprehensive YARA rules to detect Octalyn Stealer variants. These rules target the malware’s unique characteristics, including its Telegram integration and data theft capabilities:
rule Octalyn_Stealer_Main {
meta:
description = "Detects Octalyn Stealer main executable"
author = "GridinSoft Security Team"
date = "2025-01-29"
hash = "575f6bde98c678461d47dea3e5dce615ccdb490a096e8b2017176b96d8663af2"
reference = "https://gridinsoft.com/blogs/octalyn-stealer/"
strings:
$s1 = "Octalyn" ascii wide
$s2 = "ZeroTrace" ascii wide
$s3 = "t.me/ZeroTraceOfficial" ascii wide
$s4 = "OctalynTelegram" ascii wide
$s5 = "Stealer" ascii wide
// Telegram bot API strings
$telegram1 = "api.telegram.org" ascii wide
$telegram2 = "sendDocument" ascii wide
$telegram3 = "chat_id" ascii wide
$telegram4 = "bot_token" ascii wide
// Cryptocurrency wallet targeting
$crypto1 = "MetaMask" ascii wide
$crypto2 = "Phantom" ascii wide
$crypto3 = "Exodus" ascii wide
$crypto4 = "Atomic" ascii wide
$crypto5 = "wallet.dat" ascii wide
// Browser data targeting
$browser1 = "Login Data" ascii wide
$browser2 = "Web Data" ascii wide
$browser3 = "Cookies" ascii wide
$browser4 = "Local Storage" ascii wide
// Gaming platform strings
$gaming1 = "minecraft" ascii wide nocase
$gaming2 = "steam" ascii wide nocase
$gaming3 = "epic games" ascii wide nocase
$gaming4 = "growtopia" ascii wide nocase
condition:
uint16(0) == 0x5A4D and
(
(2 of ($s*)) or
(1 of ($s*) and 2 of ($telegram*)) or
(3 of ($crypto*)) or
(3 of ($browser*) and 1 of ($gaming*))
)
}
rule Octalyn_Stealer_Telegram_Component {
meta:
description = "Detects Octalyn Stealer Telegram exfiltration component"
author = "GridinSoft Security Team"
date = "2025-01-29"
strings:
$api1 = "https://api.telegram.org/bot" ascii wide
$api2 = "/sendDocument" ascii wide
$api3 = "/sendMessage" ascii wide
$param1 = "chat_id=" ascii wide
$param2 = "document=" ascii wide
$param3 = "caption=" ascii wide
$header1 = "Content-Type: multipart/form-data" ascii wide
$header2 = "User-Agent:" ascii wide
// Data exfiltration indicators
$data1 = "passwords.txt" ascii wide
$data2 = "cookies.txt" ascii wide
$data3 = "wallets.txt" ascii wide
$data4 = "tokens.txt" ascii wide
condition:
uint16(0) == 0x5A4D and
(
(2 of ($api*) and 2 of ($param*)) or
(1 of ($api*) and 2 of ($data*)) or
(3 of ($param*) and 1 of ($header*))
)
}
rule Octalyn_Stealer_Config {
meta:
description = "Detects Octalyn Stealer configuration files"
author = "GridinSoft Security Team"
date = "2025-01-29"
strings:
$config1 = "Telegram Token" ascii wide
$config2 = "Chat ID" ascii wide
$config3 = "Build Payload" ascii wide
$config4 = "Author" ascii wide
$config5 = "ZeroTrace" ascii wide
$path1 = "\\AppData\\Roaming\\" ascii wide
$path2 = "\\AppData\\Local\\" ascii wide
$path3 = "\\Google\\Chrome\\User Data\\" ascii wide
$path4 = "\\Mozilla\\Firefox\\Profiles\\" ascii wide
condition:
(3 of ($config*)) or
(2 of ($config*) and 2 of ($path*))
}
rule Octalyn_Stealer_Behavioral {
meta:
description = "Detects Octalyn Stealer behavioral patterns"
author = "GridinSoft Security Team"
date = "2025-01-29"
strings:
// File system operations
$fs1 = "FindFirstFile" ascii
$fs2 = "FindNextFile" ascii
$fs3 = "CopyFile" ascii
$fs4 = "CreateDirectory" ascii
// Registry operations
$reg1 = "RegOpenKeyEx" ascii
$reg2 = "RegQueryValueEx" ascii
$reg3 = "RegCloseKey" ascii
// Network operations
$net1 = "InternetOpen" ascii
$net2 = "InternetConnect" ascii
$net3 = "HttpOpenRequest" ascii
$net4 = "HttpSendRequest" ascii
// Crypto API
$crypto1 = "CryptUnprotectData" ascii
$crypto2 = "CryptProtectData" ascii
// Process operations
$proc1 = "CreateProcess" ascii
$proc2 = "TerminateProcess" ascii
condition:
uint16(0) == 0x5A4D and
(
(3 of ($fs*) and 2 of ($net*)) or
(2 of ($reg*) and 2 of ($crypto*)) or
(4 of ($net*) and 1 of ($proc*))
)
}
rule Octalyn_Stealer_Delphi_Signature {
meta:
description = "Detects Delphi/Pascal compiled Octalyn Stealer variants"
author = "GridinSoft Security Team"
date = "2025-01-29"
strings:
// Delphi/Pascal runtime signatures
$delphi1 = "Borland" ascii
$delphi2 = "Embarcadero" ascii
$delphi3 = "@HandleFinally" ascii
$delphi4 = "@TryFinallyExit" ascii
$delphi5 = "System.pas" ascii
// Octalyn specific strings
$octalyn1 = "Octalyn" ascii wide
$octalyn2 = "Stealer" ascii wide
$octalyn3 = "ZeroTrace" ascii wide
// VCL components commonly used
$vcl1 = "TForm" ascii
$vcl2 = "TButton" ascii
$vcl3 = "TEdit" ascii
$vcl4 = "TMemo" ascii
condition:
uint16(0) == 0x5A4D and
(
(2 of ($delphi*) and 1 of ($octalyn*)) or
(1 of ($delphi*) and 2 of ($octalyn*) and 1 of ($vcl*))
)
}
How to Use These YARA Rules
Security professionals can use these YARA rules in various ways:
- Endpoint Detection: Deploy rules on endpoints using YARA-compatible EDR solutions
- Network Monitoring: Use rules to scan network traffic and file transfers
- Malware Analysis: Apply rules during static analysis of suspicious samples
- Threat Hunting: Proactively search for Octalyn variants in your environment
To run these rules, save them to a .yar file and execute:
yara octalyn_rules.yar /path/to/scan/
yara -r octalyn_rules.yar /path/to/directory/
Rule Explanation
Each rule targets different aspects of the malware:
- Octalyn_Stealer_Main: Detects the primary executable using string signatures and functionality indicators
- Octalyn_Stealer_Telegram_Component: Focuses on the Telegram bot API integration for data exfiltration
- Octalyn_Stealer_Config: Identifies configuration files and setup components
- Octalyn_Stealer_Behavioral: Catches the malware based on API calls and behavioral patterns
- Octalyn_Stealer_Delphi_Signature: Specifically targets the Delphi/Pascal compiled variants
These rules are designed to minimize false positives while maintaining high detection rates. They can be customized based on your specific environment and threat intelligence requirements.
Detection Names and Technical Details
Security vendors have been quick to identify Octalyn Stealer, though they each have their own creative names for it:
- Avast: Win32:MalwareX-gen [Trj]
- ESET-NOD32: A Variant Of MSIL/Agent.VJC
- Kaspersky: HEUR:Trojan.Win32.Generic
- Microsoft: Trojan:Win32/Wacatac.B!ml
The fact that it’s getting flagged by multiple security vendors with high confidence levels should tell you everything you need to know about its legitimacy (spoiler: it has none).
Signs Your System Might Be Infected
Octalyn Stealer is designed to operate stealthily, but there are some telltale signs that might indicate its presence:
- Unusual network activity, especially connections to Telegram servers
- Unexpected data usage or network traffic spikes
- Browser settings changing without your input
- Cryptocurrency wallet balances mysteriously decreasing
- Unexpected logouts from various online accounts
- System performance degradation
- Antivirus alerts mentioning the detection names listed above
- Unknown processes running with network access
If you’re experiencing any combination of these symptoms, it’s time to take action. Remember, infostealers like Octalyn work quickly – the longer they remain on your system, the more damage they can do.
How to Remove Octalyn Stealer
If you suspect Octalyn Stealer has made itself at home on your system, here’s how to evict this unwelcome guest:
Step 1: Disconnect from the Internet
First things first – cut off the malware’s communication line. Disconnect your computer from the internet to prevent further data exfiltration while you work on removal. This is especially important with the Telegram variant, as it continuously sends data to the attacker’s account.
Step 2: Boot into Safe Mode
Restart your computer in Safe Mode to limit the malware’s ability to interfere with the removal process. This also prevents it from loading automatically with Windows.
Step 3: Run a Complete System Scan

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Step 4: Check for Persistence Mechanisms
Octalyn might have created scheduled tasks, registry entries, or startup items to ensure it runs every time you boot your computer. A thorough anti-malware scan should catch these, but it’s worth double-checking manually:
- Check Windows startup programs (Task Manager > Startup tab)
- Review scheduled tasks (Task Scheduler)
- Examine browser extensions for suspicious additions
- Look for unknown services running in the background
Step 5: Change All Your Passwords
This is crucial. Since Octalyn specifically targets stored passwords and login credentials, you’ll need to change passwords for:
- All online accounts (email, social media, banking)
- Cryptocurrency wallets and exchanges
- Gaming platforms and digital stores
- Any other services you’ve logged into recently
Step 6: Secure Your Cryptocurrency
If you use cryptocurrency wallets, take immediate action:
- Transfer funds to new wallets with fresh private keys
- Change passwords on all cryptocurrency exchanges
- Enable additional security measures like withdrawal whitelisting
- Monitor your wallets for any unauthorized transactions
Step 7: Enable Two-Factor Authentication
While you’re updating your security, enable two-factor authentication (2FA) on all accounts that support it. This adds an extra layer of protection even if your passwords are compromised.
Step 8: Monitor Your Accounts
Keep a close eye on your financial accounts, cryptocurrency wallets, and other sensitive services for any unauthorized activity. Set up account alerts where possible.
Use Antivirus Software
A good antivirus solution can catch threats like Octalyn before they have a chance to do damage. GridinSoft Anti-Malware offers real-time protection against the latest threats.
Practice Safe Email and Social Media Habits
Don’t open attachments or click links from unknown senders. Even if an email appears to be from someone you know, be cautious – their account might be compromised.
The Bigger Picture: The Democratization of Cybercrime
Octalyn Stealer represents a troubling trend in cybercrime: the democratization of malware development. When such tools are freely available on platforms like GitHub, complete with user manuals and video tutorials, the barrier to entry for cybercrime drops significantly.
This isn’t just about technical sophistication anymore. The Telegram integration shows how cybercriminals are leveraging legitimate services to make their operations more resilient and harder to detect. Unlike ransomware attacks that make their presence known immediately, infostealers work silently in the background, often remaining undetected for months.
The fact that there are instructional videos on YouTube demonstrating how to use this malware is particularly concerning. It shows how cybercriminals are using mainstream platforms to recruit and train new members, turning cybercrime into a more accessible “career path.”
What to Do If You’ve Been Compromised
If Octalyn Stealer has successfully harvested your data, the damage might extend beyond just your computer. Here’s what you should do:
- Contact your bank if you suspect financial information was compromised
- Monitor your credit reports for any suspicious activity
- Consider identity theft protection services if personal information was stolen
- Report the incident to relevant authorities if significant financial loss occurred
- Secure your cryptocurrency by moving funds to new wallets with fresh private keys
- Check your social media accounts for unauthorized posts or messages
- Review your gaming accounts for any suspicious activity or unauthorized purchases
The Bottom Line
Octalyn Stealer is a serious threat that demonstrates how sophisticated and accessible modern malware has become. It’s not content with just disrupting your computer – it wants to steal your entire digital identity and sell it to the highest bidder. The Telegram integration makes it even more dangerous, providing real-time data exfiltration that’s harder to detect and block.
The good news is that with proper security measures and a bit of common sense, you can protect yourself from threats like Octalyn. Keep your software updated, use reputable security solutions, and remember that if something seems too good to be true (like free premium software or “educational” hacking tools), it probably is.
Stay safe out there, and be especially wary of anything that claims to be “educational” but involves stealing other people’s data.