Mobile Security
Microsoft warns of dangerous vulnerability in Surface Pro 3 devices
Microsoft engineers have published a security bulletin on a new vulnerability affecting Surface Pro 3 tablets. The bug could be…
Ukrainian cyber police arrested ransomware operators who “earned” $150 million
Ukrainian Cyber Police have arrested two operators of an unnamed ransomware. It is reported that the operation was carried out…
Experts showed fraudulent payments from a locked iPhone with Apple Pay and a Visa card
Scientists talked about how to make fraudulent payments using Apple Pay with a Visa card on a locked iPhone. This…
Encryption algorithms for 2G networks have been intentionally weakened
A group of scientists from several European universities published a report on encryption algorithms for 2G networks, which many information…
Google stopped trying to shorten URLs in the address bar
Google’s experiment with attempt to shorten URLs (hiding parts of the URL from the address bar) has finally failed and…
SpiKey technique allows opening the lock by recording a sound of a turning key
Scientists from the National University of Singapore have published a…
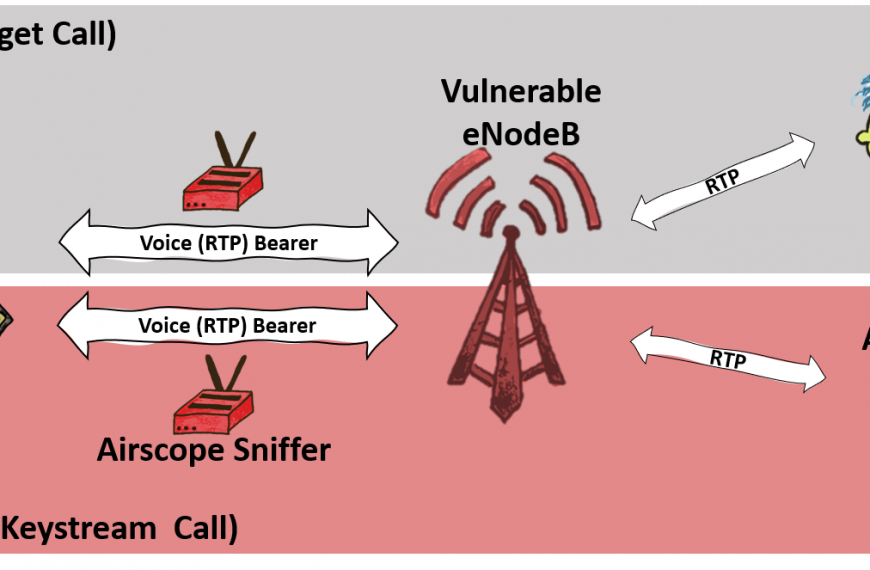
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in…
Citrix expects attacks on fresh issues in XenMobile
Citrix engineers released a number of Citrix Endpoint Management patches…
Media Reports that Garmin Paid Ransom to WastedLocker Malware Operators
In July 2020, Garmin, the manufacturer of wearable electronics and…
Vulnerabilities in old GTP protocol could affect 4G and 5G networks
Experts cautioned that vulnerabilities in the old GTP (GPRS Tunneling…
Qatar obliged citizens to install “spyware” for containing COVID-19 pandemic
As part of the fight against the spread of coronavirus…
Hackers Attacked Ghost Blogging Platform and LineageOS Servers Using Salt Vulnerabilities
According to the development team of the Ghost blogging platform,…
For iOS was discovered a new exploit, with the help of which China traced the Uyghurs
Specialists of the information security company Volexity discovered a new…
NASA staff faces exponential increase in number of hacker attacks
Representatives of the space agency said that recently NASA staff…
The number of “coronavirus” cyberattacks increased to 5,000 per day
Check Point experts estimated that the number of “coronavirus” cyberattacks…
Two new malware can steal cookies from Android apps
IS experts discovered two new malware for Android (recognized as…
More than 40% of Android users are at risk of cyberattacks
According to a study by Which company, more than 40%…