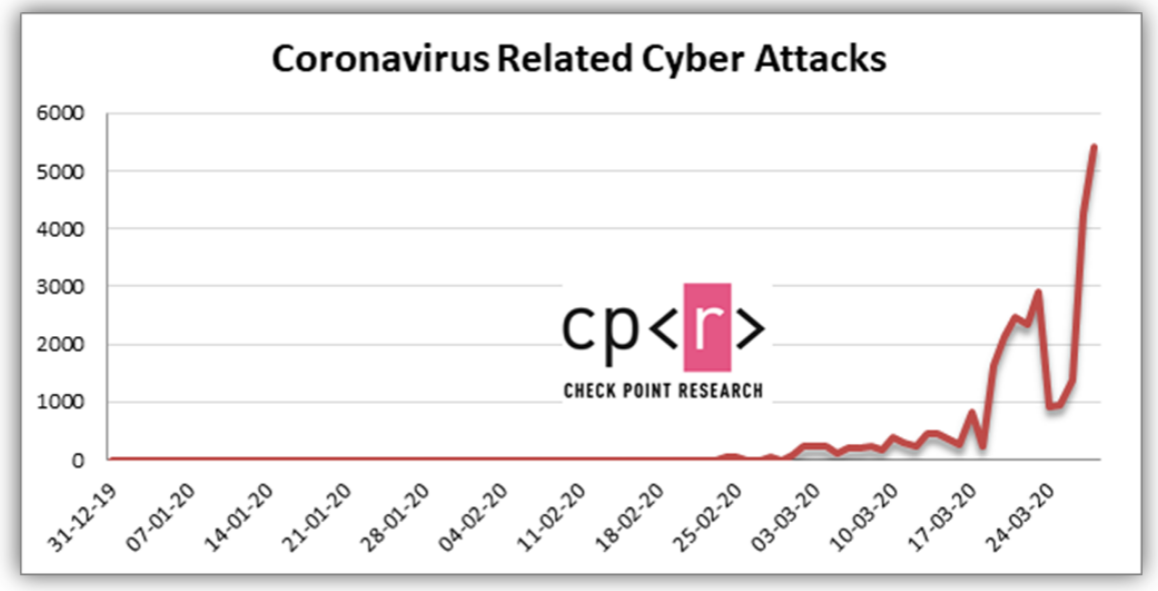
Check Point experts estimated that the number of “coronavirus” cyberattacks increased to 5,000 per day, and number of attacks on sites posing as Netflix services doubled.
Researchers say the total number of cyberattacks has declined since the onset of the coronavirus pandemic and subsequent economic downturn. However, the number of attacks related to COIVD-19 has significantly increased against this background – in fact, on this blog, news on this topic appears more and more often.
In the period from January to March 2020, researchers recorded a monthly decrease in hacker attacks on organizations by 17% around the world. However, since mid-February, there has been a significant increase in the number of attacks associated with coronavirus.
So, only in the last two weeks their number has risen sharply from several hundred to more than 5,000 per day. On average, more than 2,600 attacks are made daily.
The following resources are potentially malicious:
- Sites with the word “corona” or “covid” in the domain;
- files whose names include the word “corona” or related words;
- files distributed by e-mail mentioning the coronavirus in the subject line.
84% of all attacks were triggered by phishing sites from which fake emails were sent even allegedly from WHO. In approximately 2% of cases, the transition to a malicious website was carried out from a mobile device.
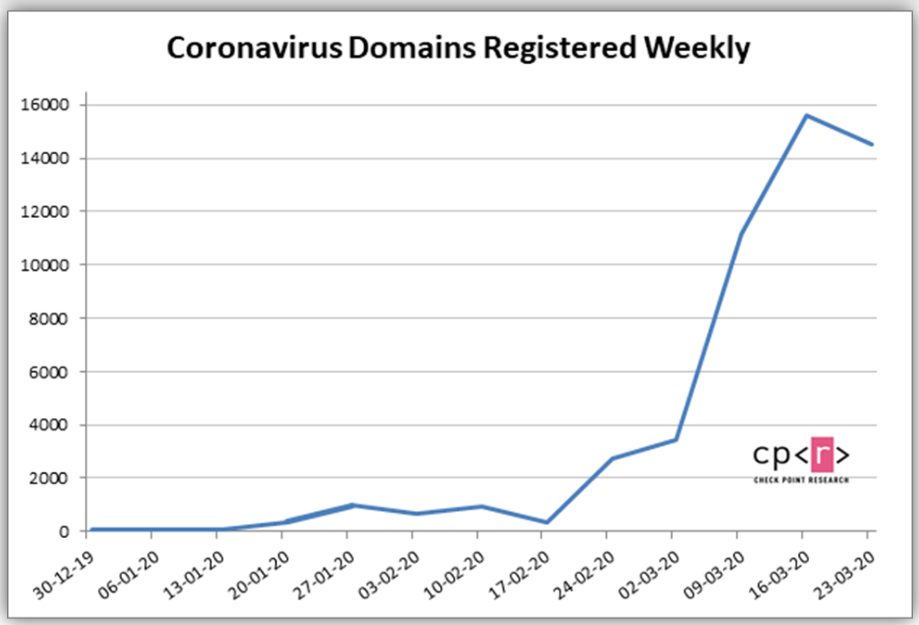
Over the past two weeks, more than 30,103 new domains related to the theme of coronavirus have been registered, of which 0.4% (131) were found to be malicious, 9% (2,777) were considered suspicious. Thus, since January 2020, a total of more than 51,000 coronavirus-related domains have been registered.
Also, the pandemic and the global transition to remote job led to an increase in the number of Netflix subscribers, which, in turn, aroused interest in the streaming platform by scammers. Over the past two weeks, there has been a twofold increase in phishing attacks by sites posing as Netflix’s original resources. On some of these sites, attackers install payment systems in order to fraudulently receive money and personal data of users.
Fake Netflix
“Obviously, a significant increase in the number of cyberattacks is associated with the active dissemination of news about coronavirus worldwide. Because a large number of people now are forced to work from home, attackers have shifted their focus of attention from large businesses to private users. As a result, we see an increase in malicious attacks on resources such as Zoom or Netflix,” — says Check Point Software reresentative. – In order not to become the next victim of cyber fraud, it is extremely important to exercise increased caution and attention. This is especially true for suspicious sites, links or files received by mailing.”
Check Point experts advise to adhere to the following recommendations for safe behavior on the Internet, so as not to become a victim of online fraud:
- Pay attention to spelling errors in site names and in mailing lists.
- Be careful with files received by e-mail from unknown senders, especially if you are asked to perform an atypical action when opening them.
- Make sure you order goods from an official store. One way to do this is not to click on the links with ads from emails, but to find the company you need on Google and follow the link on the page with the search results.
- Beware of “special offers.” For example, the offer of “an exclusive medicine for coronavirus” should be in doubt.
- Make sure that you use different passwords for each application and each account.




