The “Internet Is A Dangerous Place” scam is a novel type of threatening email message that targets people with threats of intimidation and exposure. In this fraudulent email, the scammer claims to have obtained some compromising information and recordings. They further demand a ransom to prevent publishing the data to the public.
Internet Is A Dangerous Place Scam Overview
“Internet is a dangerous place”, or “Security status not satisfied” are both names of the same email scam campaign. It falls under the category of sextortion/social engineering frauds, that aim at scaring the victim with the threats of public intimidation and making them send the money.
This scam can take different forms, but its essence remains the same: the so-called hacker claims to have infected the victim’s devices and obtained confidential information. This makes it similar to other email extortion scams. If the victim does not pay the ransom, the hacker will publish this information. Hacker also boasts of infecting the devices of people from victim’s contact list, and collecting similar intimidating information about them as well.
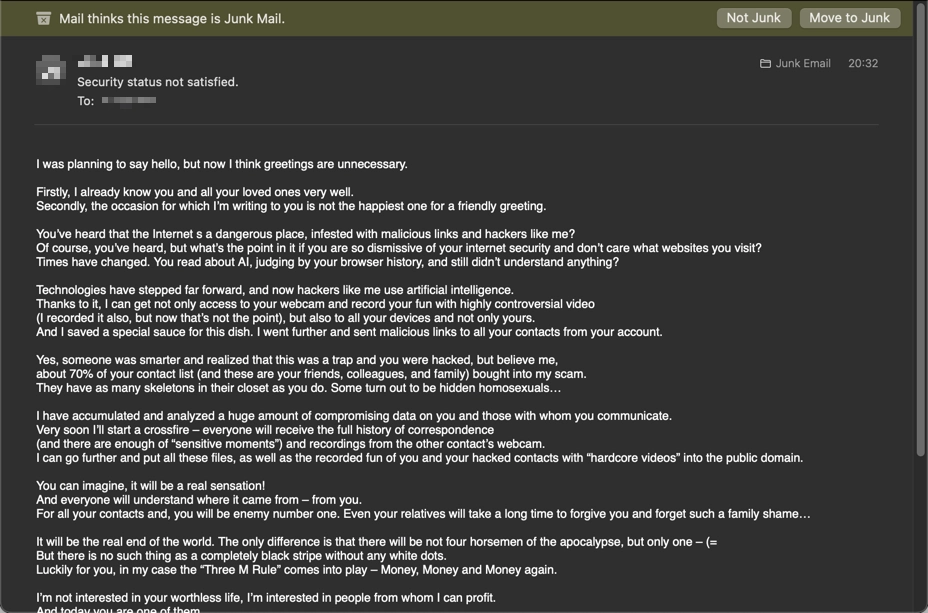
These scam emails are slightly different from each other, but their basic content remains the same. Here is our example:
Let’s get through each element of this scam; I will explain the social engineering tricks that the scammer uses to make the victim believe that all this is for real. Also, I will debunk the mystical AI malware and all the related nonsense, made up entirely for adding mysticality and complexity to the alleged hack.
Fear-inducing Introduction
The message usually begins with an alarming subject line like “Security Status Not Satisfied”. It aims to catch the recipient off-guard, making them more vulnerable to the ensuing threats. The statement “I already know you and all your loved ones very well” is meant to induce fear by suggesting that the sender has intimate knowledge of the recipient’s personal life. It hints at a deep invasion of privacy, which is a potent trigger for anxiety and panic. This is a classic social engineering tactic.
Overall, the header contains vague and general statements that could apply to anyone. There are no specific details that would lend credibility to the sender’s knowledge or threats. Claims about such the ability to infect all contacts and relatives’ devices are hard to prove and are barely realistic. Lastly, the email mentions advanced technologies like artificial intelligence and invulnerable malware. However, it lacks any technical specifics that would make the threats believable.
Collecting Sensitive Information
The scammer continues with claims to have “monitored all your activities” and that “AI-based malware” was used to gather compromising data and record video through the webcam. This is the most intimidating factor of the scam, especially considering the fraudster’s focus on the moment when the user was watching adult content.
One more piece of intimidation is the fact that the user’s supposed recklessness has taken other people’s private life as collateral. Hacker claims that the malware has spread to other devices, including those of the victim’s friends and family. As there’s no way to prove or disprove this, it’s not that hard to take this bait as well. And overall, at this point into the scam, the victim likely believes the text – an ideal point to switch to the main course.
Threats of Publishing Exposing Videos of You & All The Contact Book
The scam reaches its climax with claims that the so-called hacker accessed the device’s webcam and captured video of the victim in a compromising situation. If this were true, the attacker would have attached a short part of this video or a screenshot as proof. This is meant to coerce the victim into paying the ransom to avoid public humiliation.
Perhaps the most desperate move by the fake hacker is the threats to the victim’s relatives and contacts. While this is theoretically possible, in practice, if a hacker did this, they wouldn’t boast about it. Moreover, if the attacker had managed to hack the victim’s contacts, they would at least provide some proof of it.
AI As a Malware
The same applies to the claims about using AI. While it is possible for cybercriminals to use artificial intelligence, they certainly do not use it in the way the so-called hacker describes. A much more prevalent application for this new technology is to write more convincing phishing emails, clone voices, and create deepfake videos.
What the “hacker” supposes is that they used AI to hack into the computer and collect the information. As far as Google knows, there is not a single case of such an application. And believe me, the Web will be set abuzz shall someone pull such a trick.
Ransom Demands
The fraudulent email concludes with a ransom demand, asking for ~$1200-1400 in Bitcoin, with a 48-hour deadline for payment. The scammer threatens to make all collected information and videos public and notify the victim’s contacts, supposedly causing irreparable damage to their reputation.
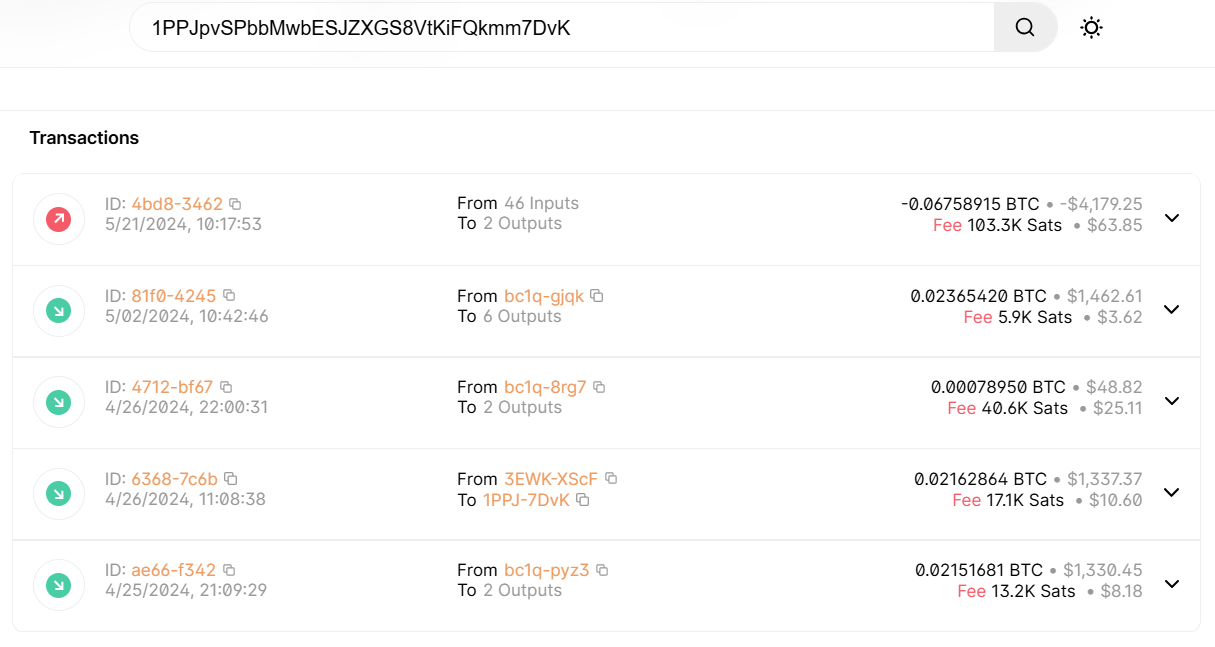
Cryptocurrency wallet address that the hacker specifies reveals some interesting details about how effective this scam is. Emails are sent in thousands every day, but the wallet has only 2 transactions. One of the previously used addresses is naught on any money transfers whatsoever. Nonetheless, $2800 for effectively doing nothing, except for writing and mass-mailing a scary email like a “Internet Is A Dangerous Place”, is still quite a sum.
Is your system infected?
Of course, there is no reason to believe this email, and we just found out why. Nevertheless, to ensure there are no threats on your system, even if unrelated to this email, I recommend scanning your device for malware. You can use GridinSoft Anti-Malware and follow the instructions below.





