Recent attacks on US military systems and Taiwan companies are distinctive not only by the brave target choosing, but also for the used toolkit. In the case of both targets, attackers used HiatusRAT as an initial access/reconnaissance tool. Aside from being used in these attacks, Hiatus Trojan has other things to boast of.
US DoD and Taiwan Companies Cyberattacks
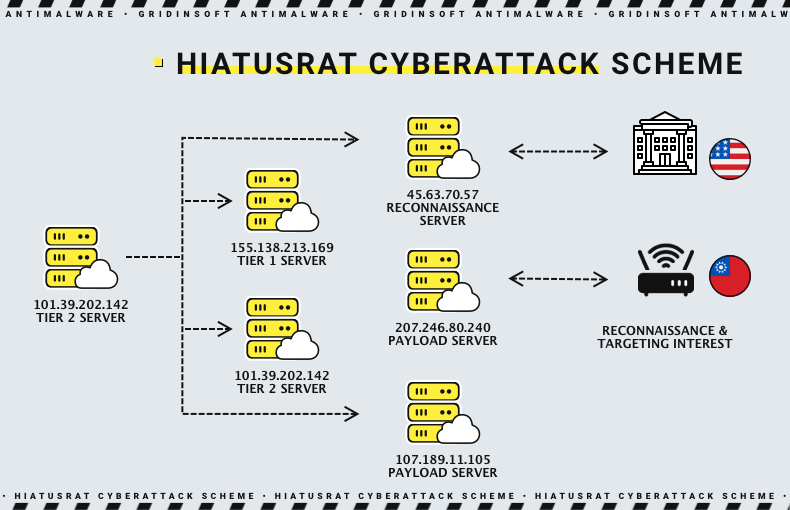
First, let’s clear out the attacks upon quite famed organisations and companies. The long-going cyberattack upon Taiwanese companies and at least one government organisation was detected as early as in August 2023. Lumen researchers who studied the botnet established by the HiatusRAT in the past noticed a new flow of connections that comes from Taiwan IP address zones. Soon after, =cyberattacks on chemical production facilities, semiconductor manufacturers and one municipality were uncovered.
The story around the U.S. Department of Defence is a bit different. Same research group detected traffic coming to the IP addresses associated with the botnet not only from Taiwan but also from the US. Specifically, they discovered that crooks who stand behind the RAT used one of its Tier 2 servers to connect to the DoD server dedicated to work with defence contracts. Fortunately, no deep penetration happened here, and hackers were most probably performing reconnaissance before further actions.
HiatusRAT Analysis
First thing that comes into view when you check the Hiatus is its network architecture. Instead of infecting endpoints, it targets networking devices – at least it was doing so since its emergence in late 2021. Routers are gateways for humongous amounts of information – and having complete control over it may sometimes give you much more than hacking the computers in the network. Though, nothing stops Hiatus from delivering additional payloads to the target systems. Aside from sniffing, such a network of compromised routers can also serve as a network of proxy servers that conceal the real IP address from the target server.
To spread the payload, hackers seek business-grade network routers with vulnerable firmware installed. Firstlings of the botnet were amongst Draytek routers, specifically Vigor 2960 and 3900. Nowadays, malware has builds capable of infecting routers with chipsets based on Arm, i386, x86-64 and MIPS/MIPS64 architectures. This sets up quite a large number of devices, as network infrastructure firmware updates are implemented even more reluctantly than patches to regular software.
Execution flow
The attack chain that enables the RAT injection into the router is not clear even nowadays. Though it is clear that upon gaining initial access, attackers execute a batch script that downloads the payload and an auxiliary utility. The latter is a specific version of a tcpdump, a command-line tool that allows for packet analysis.
Upon execution, the first thing to do for HiatusRAT is kicking out other processes that may be listening to the same 8816 port. If there are any, malware jams one first and proceeds with normal launching. Then, a kind-of-classic step comes: malware gathers basic information about the device it has started on. Among such data is information about its MAC address, architecture, firmware and kernel versions. It also gets precise information about the file system and all files that can potentially be stored in the internal memory.
Once malware is done with these checks, it reads a tiny JSON that contains what appears to be malware config. There, malware retrieves a C2 servers address. Aside from the “main” server, there is one used to receive all the packages gathered with the modified tcpdump tool. The first request to the control server is a classic HTTP POST that contains several fields, with basic system info gathered the step before.
Host: 104.250.48[.]192:443
Accept: */*
Content-Type: application/json
X_UTIME: 1674762549
X_UUID: 005056c00001
X_TOKEN: ffca0c6ca91ce7070c3e5e41d7c983a2
HiatusRAT Functionality
I’ve already mentioned the tcpdump-like tool that supplies a significant part of the RAT functionality. However, it does not stop at this point. Hiatus can receive different commands from the command server, which alter its functionality or even force the malware to melt down. Thing is, some of these functions were not used to the moment, despite being available since the first release of the malware back in 2021.
| Command | Description |
|---|---|
| Socks5 | Sets up a SocksV5 proxy on the hacked device, that allows for port forwarding/listening that comply with RFC 1928 |
| File | Designates the file to read or delete on the infected host; also guides to upload the specified file. |
| Executor | Commands to download and execute the file from the command server. |
| Tcp_forward | Comes with specified forward IP and listening/forwarding port configurations. These changes then applied to router settings, making it forward any TCP traffic through the listening port. |
| Script | Similar to Executor, downloads and runs the script from the C2. |
| Shell | Spawns an instance of a remote shell on the compromised router. Together with Execute and Script, creates the malware delivery functionality. |
| Quit | Self-explaining command, forces malware to melt down with all operations seizure. |
How to protect against network infrastructure attacks?
Well, Hiatus used to aim at routers with some specific architecture and series, but now it covers quite a bit of possible variants. The ways hackers use to deploy this malware are still unclear, so there are not many reactive measures to figure out. Instead, I have several proactive advice for you to stick to.
Use advanced network protection solutions. Well, antivirus programs are not greatly effective at preventing this RAT infection. Meanwhile, network protection solutions, especially ones that are designed to bear on heuristics, can effectively detect and dispatch the intruder just by its behaviour. Network Detection and Response systems, conjoined with SOAR and UBA solutions, can show excellent results at protecting the environment against tricky malware attacks.
Update (or upgrade) your networking devices regularly. Since the key point of the malware injection is vulnerable router firmware, it is essential to keep it updated. Keep an eye on malware attacks that were executed with or via vulnerabilities in networking devices. Usually, device manufacturers release updates in a matter of weeks. Though, there could be unfortunate cases when some really old devices reach end-of-life and are not supported in any form. In this case, you are out for device updating – this is the best and most definite way to get rid of the hazard.
Keep a well-done anti-malware software on hand. I’ve just said that anti-malware programs are not very effective in this case, and I say it is nice to have – so inconsistent of me, isn’t it? The answer is no, as anti-malware programs will serve as a preventive mechanism for malware that HiatusRAT can deliver through its functionality. Multi-layer security structures are always harder to penetrate, at least without triggering the alarm.


