A recent report by Avast researchers identified an old-timer malware called GuptiMiner. It uses the eScan antivirus update mechanism to stealthily inject backdoors and cryptocurrency mining programs into users’ computer systems and large corporate networks. This is further evidence that cybercriminals are adapting their techniques to bypass modern security measures. Let’s look at the situation.
Campaign discovery and GuptiMiner
Avast specialists analyzed the activity of the GuptiMiner malware active since 2018. GuptiMiner is a sophisticated malware that aims at spreading backdoors and performing hidden cryptomining in corporate networks. The malware utilizes a multi-stage infection chain. It starts by hijacking antivirus software updates through man-in-the-middle (MitM) attacks. This allows attackers to substitute legitimate updates for malicious ones.
Avast informed eScan and India CERT of the found vulnerability, which was successfully patched on July 31, 2023. However, since users rarely install more than one antivirus, this limits the ability to detect and analyze the full scope of GuptiMiner’s activities.
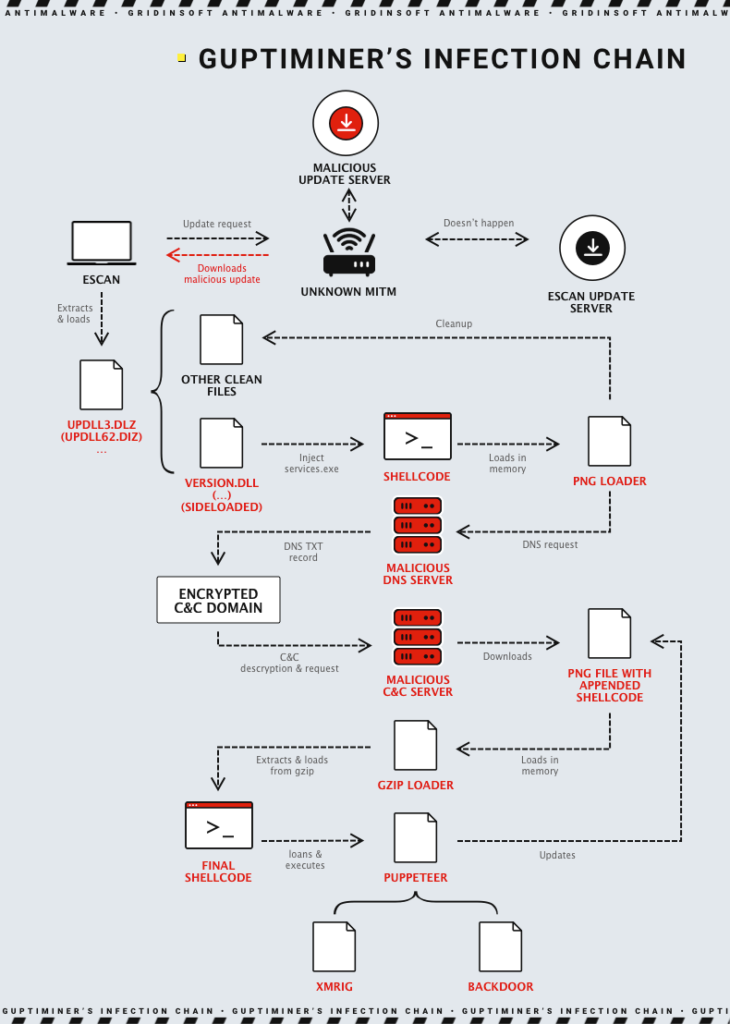
This malware uses a complex infection chain. The attack starts by intercepting eScan antivirus updates. The update program is downloaded from the server, but in its path is an attacker who substitutes it with a malicious one. Next, eScan decompresses and downloads the package, initiating a chain of infection using a DLL. This DLL allows the virus to control further downloads and code execution.
Next, GuptiMiner uses a sideloading technique to inject malicious code into trusted processes, which allows the program to remain invisible to antivirus systems. The malware also communicates with remote command and control (C2) servers to receive commands and updates. This allows attackers to control infected systems, run additional malicious processes, or conduct cryptocurrency mining.
How does GuptiMiner work?
GuptiMiner analysis revealed that the malware used a variety of sophisticated techniques to install and hide its presence on the system. Key techniques included sideloading DLL, modifying system files, and using forged digital signatures to simulate legitimacy.
Also, one of the characteristic features of GuptiMiner is its ability to modularize infections. This includes performing DNS queries to the attacker’s DNS servers and extracting useful data from innocent-looking images. In addition to its core functionality of installing backdoors, GuptiMiner unexpectedly spreads the XMRig miner used to mine the Monero cryptocurrency.
The process of dynamically assigning mining threads for XMRig:
xmrig_shellcode_copy_ = xmrig_shellcode_copy;
num_cores_ = num_cores;
dword_140020908 = 25;
xmrig_shellcode_copy-›max_cpu_usage = '53';
xmrig_shellcode_copy_->threads = '1';
if (num_cores_ >= 6)
xmrig_shellcode_copy_-›threads = '2';
if ( num_cores_ >= 8 )
xmrig_shellcode_copy_->threads = '3';
The malware has been identified as potentially linked to the Kimsuky, a prominent North Korean hacking group. This indicates possible state sponsorship and a high degree of organization of the attacks. Before, North Korean hackers showed a certain degree of interest in acquiring cryptocurrency. So, this should not be too much of a surprise.
Two Different types of Backdoors
While analyzing the GuptiMiner malware, researchers identified two different types of backdoors. Both types of backdoors were designed to function as part of a large-scale and well-planned campaign. But each was designed to perform specific tasks on infected corporate networks.
- The first type of backdoor is a modified version of PuTTY Link, which is used to scan SMBs on the local network. This backdoor allows lateral movement (horizontal propagation of malware within the network) to access potentially vulnerable systems running Windows 7 and Windows Server 2008. This facilitates the exploitation of vulnerabilities in legacy operating systems.
- The second type of backdoor is multifunctional and modular. It accepts commands from the attacker to install additional modules and specializes in finding and stealing locally stored private keys and cryptocurrency wallets. This approach allows attackers to monitor infected systems for long periods of time and activate additional malicious features if necessary.





