Microsoft Threat Intelligence Center (MSTIC) experts announce the disruption of an operation conducted by the Russian-speaking hacking group SEABORGIUM, targeting individuals and organizations in NATO countries.
As a reminder, we previously reported the discovery of a new version of malware from Russian hackers called LOLI Stealer.
The APT group, referred to as SEABORGIUM by Microsoft, has been under researchers’ scrutiny since at least 2017. Other companies track SEABORGIUM under names such as COLDRIVER (Google), Callisto Group (F-Secure), and TA446 (Proofpoint). The group is suspected of carrying out cyber-espionage attacks against military personnel, government officials, think tanks, and journalists in NATO countries, the Baltics, Scandinavia, and Eastern Europe.
In target countries, SEABORGIUM primarily focuses its operations on defense, intelligence, and consulting companies, non-governmental and international organizations, think tanks, and universities. SEABORGIUM has been seen in attacks on former intelligence officers, experts on Russia, and Russian citizens abroad.
MSTIC analysts detail that SEABORGIUM members create fake online identities through email, social media, and LinkedIn accounts. These fake identities are then used in social engineering attacks against targeted individuals and organizations.
Operating under these fake personas, attackers initiate contact with targets to establish conversations and eventually send phishing attachments. Microsoft reveals that the hackers distribute emails with PDF attachments, links to file-sharing sites, or OneDrive accounts hosting PDF documents.
Upon opening such a file, the victim encounters a message stating that the document cannot be viewed, and a special button must be pressed to try again.
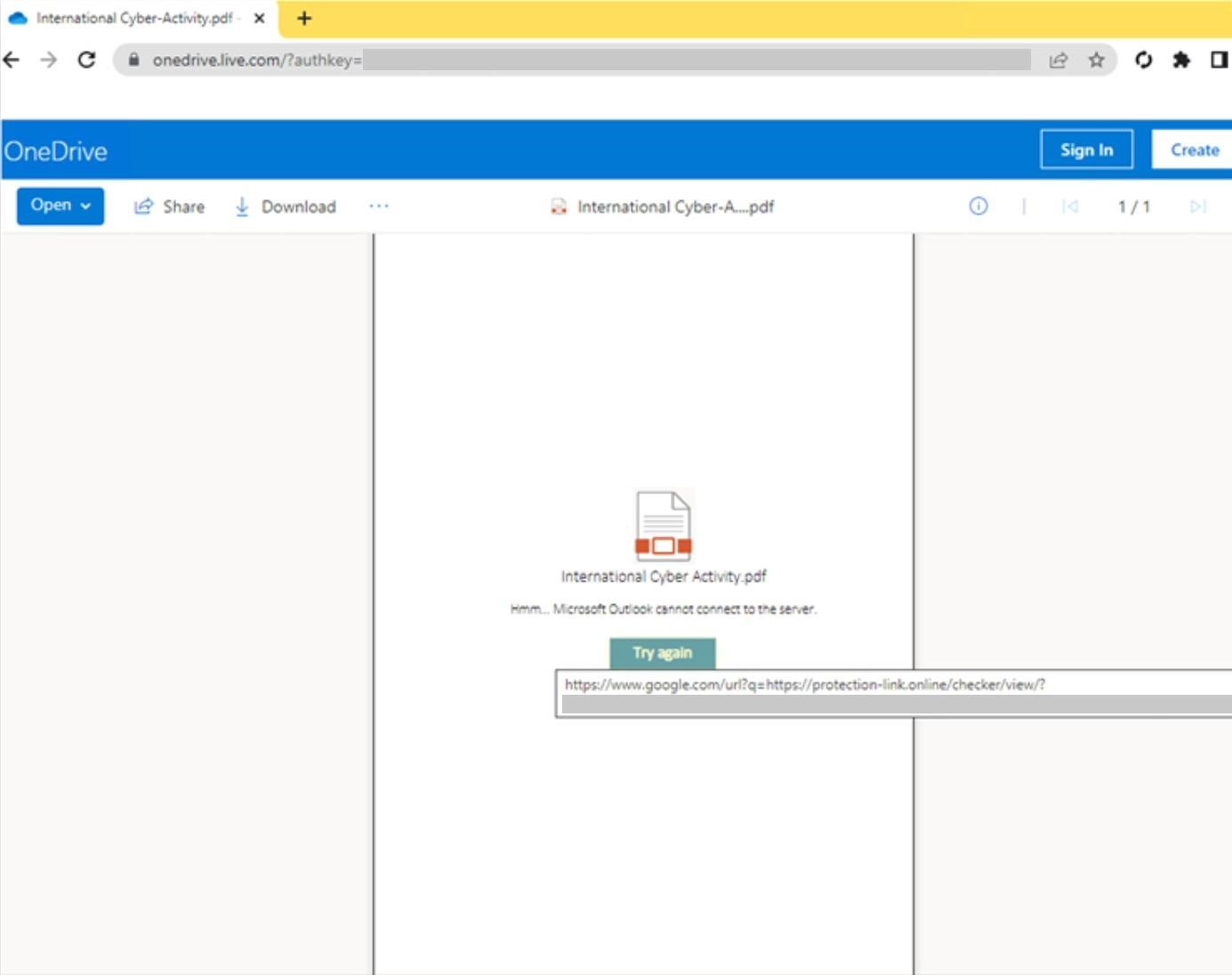
Clicking the button redirects the victim to a landing page running a phishing framework, such as EvilGinx, displaying a login form. Acting as a proxy, EvilGinx enables hackers to intercept and steal entered credentials, along with cookies/authentication tokens generated after login.
These stolen tokens enable attackers to access the compromised user account, even if the victim has two-factor authentication enabled.
According to Microsoft, once access is gained, hackers either pilfer emails and attachments or set up forwarding rules to receive all incoming emails in the victim’s compromised account. The researchers also observed attackers using a hacked account to negotiate on behalf of the victim to obtain confidential information.
MSTIC reports taking several steps to disrupt SEABORGIUM’s malicious campaign, including disabling accounts used for spying, phishing, and email harvesting.
The company has also shared indicators of compromise, including 69 domains associated with the group’s phishing campaigns, utilized to steal credentials from Microsoft, ProtonMail, and Yandex accounts.




