GitLab has released another update that fixes varying degrees of vulnerabilities. Users are advised to apply the updates as soon as possible, as one of the flaws is rated as severe and can potentially lead to Kubernetes agents takeover. The developer of the DevOps software package insists on installing the patch as soon as possible.
GitLab Patches a Critical Unauthorized Access Flaw
On November 13, 2024 GitLab published the 17.5.2, 17.4.4, and 17.3.7 patches for both Community Edition (CE) and Enterprise Edition (EE) under its planned course of software updates. The patches fix 3 vulnerabilities, with one more flaw that has not yet been assigned a CVE ID. These vulnerabilities range in severity from CVSS 5.3 to CVSS 8.5.
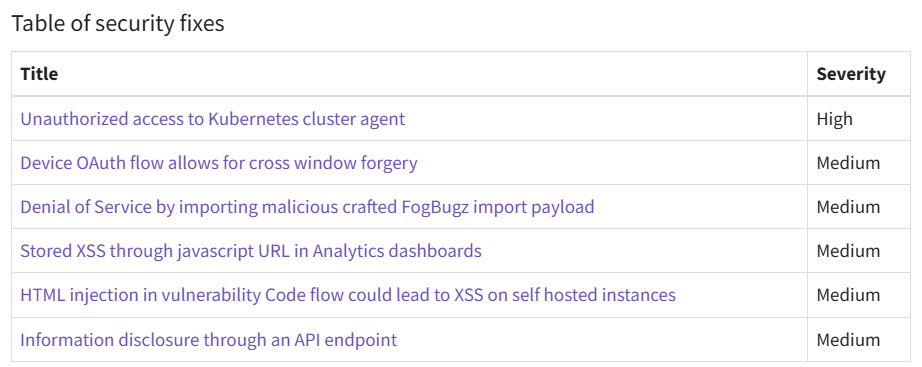
Main attention is attached to the flaw CVE-2024-9693, which grants unauthorized access to Kubernetes agents. Kubernetes is a containerization management utility, used massively in software development, thus the impact of the flaw can be enormous.
Technical Details of Vulnerabilities
Let’s start with the star of the news. CVE-2024-9693 has a CVSS score of 8.5, and stems from improper access control in GitLab CE/EE. Even though it requires some specific conditions to be fulfilled (which GitLab hesitates to disclose), it can potentially give adversaries control over all the container environments managed with Kubernetes.
This, in turn, opens gates for multiple consequences, all of which are less than pleasing for the attacked company. Hackers can leak in-development programs, exposing secrets, ruin the development environment, or inject malicious code into the tested program. The latter, in turn, may easily lead to supply chain attacks.
Other flaws patched in this update are less critical, though still require attention. CVE-2024-7404 is a device OAuth flow vulnerability with CVSS rating of 6.8. It can potentially allow an attacker to gain full API access via the flaw in authentication flow, though granting them only with the victim’s privileges. As GitLab allows for strict permission management, it will likely have much less severe consequences.
The flaw with an undesignated CVE is the Denial-of-Service issue. When importing maliciously crafted content through the FogBugz importer, the program starts taking way too much resources, eventually causing the entire system to stop responding. Due to the said requirement of a specific package, and a need for using a specific program, the CVSS rating is “only” 6.5/10.
GitLab Urges to Update
GitLab strongly encourages users to update to the latest versions — 17.5.2, 17.4.4, and 17.3.7 — to ensure protection against the above vulnerabilities. The only exception for this advice are GitLab Dedicated customers, who do not need to take action as they are out of reach for the flaws.
Fortunately for GitLab users, all the flaws were discovered internally, by the development team. No exploits exist at the moment, and obviously no real-world attacks are happening with these vulnerabilities. This, however, is about to change, as the DevOps software vulnerabilities are always in scope of cybercriminals. Before, there were cases of hackers discovering and exploiting 0-day vulnerabilities in GitLab – go read our post dedicated to it.