Fullerton India, a large lending institution from India, appears to be hacked back in early April 2023. It is confirmed by the LockBit ransomware Darknet blog, where hackers listed the company, and now, over a month later, published all the leaked information.
Fullerton, LockBit – who are they?
Fullerton India Credit Company, or shortly Fullerton India, is a major lending company that operates in almost all the country. It offers a wide range of lending programs, targeted at both individuals and businesses. The company has almost 700 branches all over India, which allows it to outreach even small towns and villages. Latest reports issued by the company say about ~2.3 million of customers, net assets of over 2.5 billion, and around 13,000 employees. Such companies – pretty large and related to the financial sector – always were in scope of cybercriminals.
LockBit gang is an infamous hacker group, active since 2019. They passed 3 major “epochs” since then, expanding their operations and offering new solutions for their “product”. Gang uses ransomware-as-a-service operation form and offers a wide range of supplementary services to their “main” product – ransomware. Specific approaches used in malware design, together with the mentioned services, allow this malware to be the fastest among the massively used ones. All that made LockBit gang the most successful ransomware on the market: its share in total attacks is over 40%. Seems that at some point, they decided to have a break from ransoming American companies and try out something new.
LockBit Publishes Data Leaked From Fullerton India
Files encryption is not the only problem created by threat actors. Before launching the ciphering process, crooks often steal all the data they can reach. LockBit applies a specific tool that allows them to extract more data for shorter periods of time. Then, hackers ask for the additional ransom – otherwise, the data will be published or sold to the third party. Such a practice is known as double extortion. LockBit, however, is known for applying another way to press on their victims. Aside from threatening to publish data, they launch a DDoS attack upon the victim’s network, and keep it going until the ransom is paid. It is not clear if hackers used that trick as well.
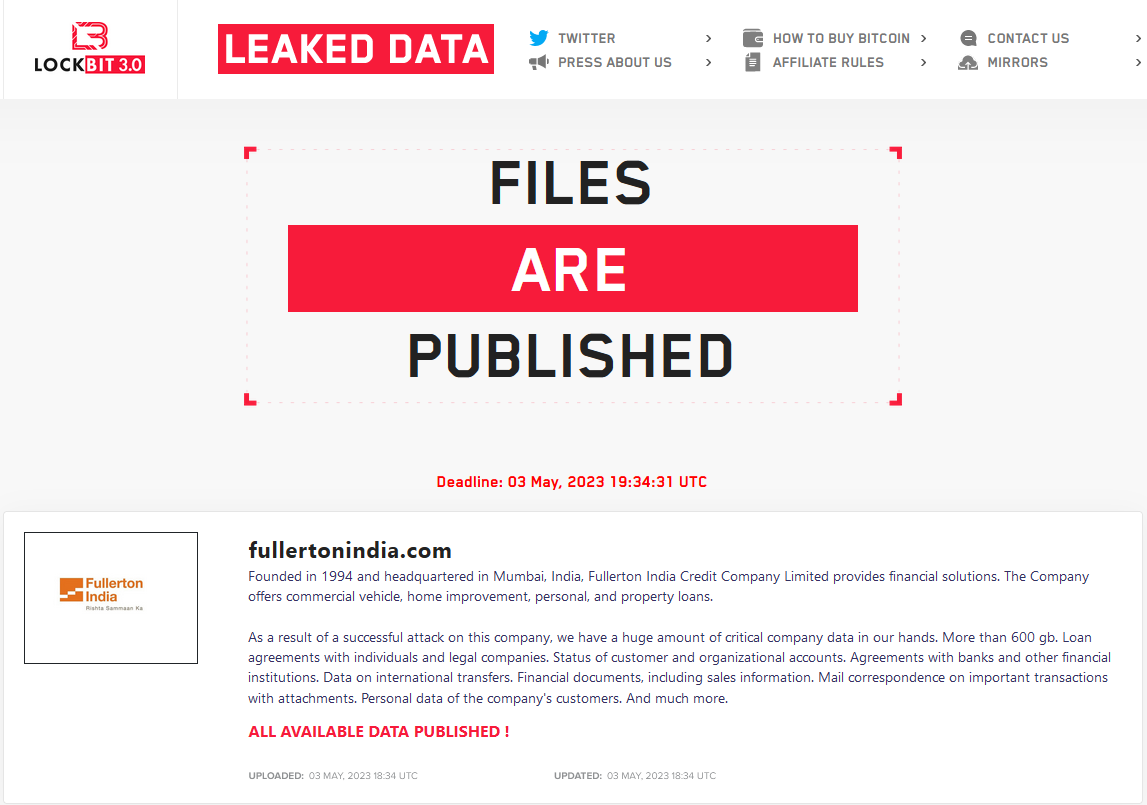
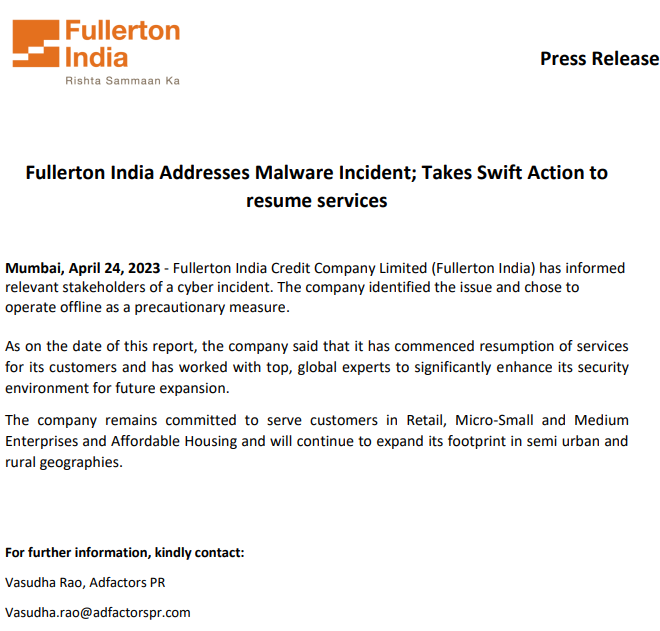
Bearing on the data available in the surface and dark Web, I can assume that the exact breach happened around late March – early April. First deadline was set on April 29, which means Fullerton was listed ~2 weeks before. Now, however, the final date is set to May 3 – four days past the previous date. Hackers also specified that the company can delay the deadline for $1,000/day. Simple maths suppose that the company already spent $4,000, and it is not clear whether they paid a ransom for data decryption. The cybercriminals’ demand for avoiding data publishing – $3 million – is definitely not paid. Fullerton themselves reported about the cyberattack only on April 24.
In the note present among other information about the attacked company, LockBit specifies the amount of leaked data – 600 gigabytes. They also shared some details regarding data categories available in the leak:
How Dangerous is Fullerton Leak?
Most data LockBit gang got their hands on is related to company operations. Thus, the key danger and damage there goes towards the company’s image. Fullerton is not a publicly-traded company, thus info about the hacks cannot harm someone because of share price shed. Nonetheless, ransom amounts typically asked by the LockBit group are tangible – much more tangible in fact than the cost of cybersecurity improvements that could prevent the attacks in future.
The risk of any cyberattack is the fact that hackers can have a peek into a company’s internal architecture. Considering tight relationships between ransomware gangs, especially ones from Russia, it is logical to suppose that another group of hackers may be interested in attacking companies like Fullerton. And instead of doing a long research in order to find the entry point, they can simply ask their “colleagues” – and get all the information immediately. Security measures should be taken as quickly as possible – and that is true for any cybersecurity incident.
How to protect against LockBit ransomware?
Despite having advanced payload and auxiliary software, LockBit shares spreading ways with other ransomware. Email spam is the king of the hill, used in over 60% of all cyber attacks around the world. Though more target-specific approaches may be used – like RDP exploitation or using other network vulnerabilities. Protecting against them requires a multi-directional approach that is quite hard to implement in one step.
First of all, guide your personnel regarding spam emails. Detecting the fake email may be obvious for a knowing person, though not all people know how to do that. The easiest way to uncover the fraud is to check the email address – it will differ from the genuine one. Still, there were cases where hackers have been using compromised business emails to perform further attacks. For that reason, I’d recommend having a peek into a dedicated article about email phishing and ways to recognize it.
Counteracting network breaches requires the use of specific software. Passive approach is possible – yet far less effective than the use of proactive software solutions. The latter, actually, are represented as Network Detection and Response systems. They combine properties of network monitors, firewalls and (partially) anti-malware programs, giving out a secure shield over the entire network.
Adhere to the latest news regarding vulnerabilities. Top-rated security is possible only in an environment which is hard to exploit. When cybersecurity researchers uncover vulnerabilities, or hackers use a new one in the wild, it is recommended to find and fix these breaches. Consider having several cybersecurity blogs on a quick dial – and the numbers of your software vendors as well. Nothing saves you more than a fast reaction.




