EpiStart or EpiBrowser is a Chromium-based web browser that is often installed without the user’s explicit consent. After installation, it passes all search queries through a chain of dubious pages, then delivers results by a different search engine. In this post, I will explain how did this browser appear and how to remove it for good.
EpiStart (EpiBrowser) Overview
EpiStart, also known as EpiBrowser, is a rogue web browser based on the open-source Chromium project. Unlike conventional browsers, it does not function as a typical search tool, but instead forces users through a fake search engine (epibrowser.com). This site lacks the ability to generate search results independently and ultimately redirects users to legitimate search engines such as Yahoo.
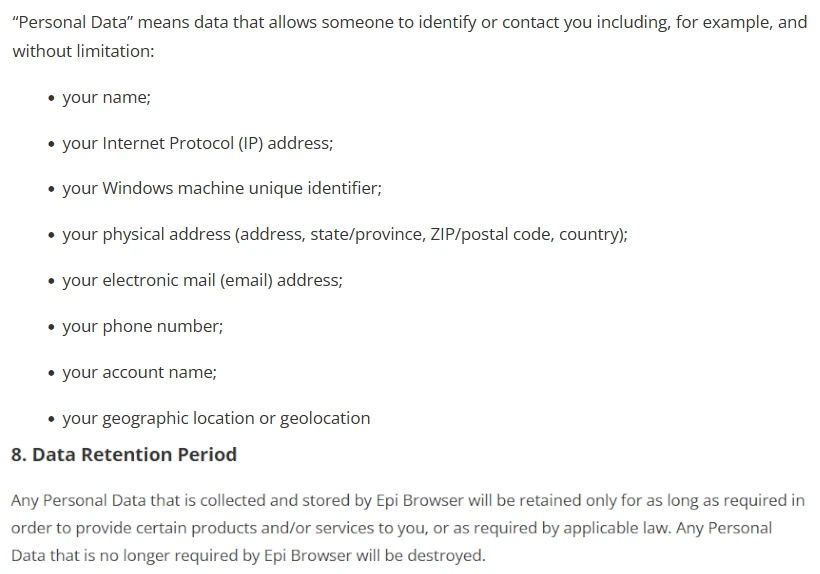
On their official website, the developers of this pseudo-browser claim partnership with Yahoo. That, however, does not restrict them from collecting all possible user information upon every search query. That redirect through the EpiBrowser website is made for exactly this purpose.
The classification of EpiBrowser as a Potentially Unwanted Application (PUA) stems from its questionable distribution tactics and intrusive behavior. Many users report encountering this browser unexpectedly, which raises concerns about its installation methods. Additionally, rogue browsers like EpiStart can engage in data collection, potentially harvesting browsing history, login credentials, and financial details. The data may then be shared or sold to third parties, further heightening privacy risks.
How did I get EpiBrowser?
EpiBrowser has its own official website, though funnily enough, there is no downloading link on it. The page is purely decorative, with minimal info about the web browser itself, and some concerning information on its data handling practices. The developers openly claim collecting tons of user data, and holding it for whatever time period they want.
To understand the whole picture, it’s worth starting with the distribution and installation process of this software. Many users get EpiStart installed unknowingly, often through software bundling. For example, many Reddit users complain about this thing appearing after running some questionable program installers.
Another common distribution method involves deceptive pop-up ads and misleading websites. Some users may be tricked into downloading EpiBrowser after seeing fake alerts claiming their current browser is outdated or insecure. Clicking on such messages often initiates the installation of unwanted software without explicit user consent. Similarly, some ads can execute scripts that download and install unwanted apps or even malware automatically when clicked.
What’s Wrong?
EpiStart (EpiBrowser) functions by hijacking users’ web activity. Upon installation, it alters system settings to make itself the default browser. Unlike traditional browser hijackers that modify an existing browser’s configuration, EpiStart circumvents these limitations by being a standalone application. This means that even if users attempt to reset their browser settings, EpiStart remains unaffected, maintaining control over search queries and web navigation.
The main feature of this rogue browser is its forced redirection. It has its own search tool. But this tool cannot process search queries by itself. So, when users attempt to conduct searches, they are first led to epibrowser.com, a fake search engine. This intermediary page then forwards users to Yahoo or other search providers, depending on factors such as geolocation. The presence of a fake search engine suggests that EpiStart may be designed to generate revenue through affiliate marketing or ad fraud schemes.
Additionally, the browser has the potential to function as adware. Advertising-supported software typically injects excessive ads into web pages, displaying pop-ups, banners, and in-text advertisements. These ads may not always be safe—some could lead to phishing sites, promote deceptive software, or even trigger silent downloads of more unwanted applications.
EpiStart may also collect browsing data, including visited websites, cookies, search queries, and other user-specific information. Such data is often used for targeted advertising but can also be exploited for malicious purposes if shared with third-party advertisers or cybercriminal networks.
How To Remove EpiBrowser?
If a user discovers EpiStart on their computer, they may be able to uninstall it through standard removal methods. However, some Reddit users have reported difficulties in doing so, suggesting that EpiStart may employ persistence techniques to resist deletion. What’s worse, spreading ways this browser utilises suggests there could be much more unwanted programs.
In such cases, running a system scan with security software like GridinSoft Anti-Malware is advisable to detect and remove any hidden components. Download it by clicking the banner you see below and run a Full Scan, to clean every last corner of your computer.
To avoid installing unwanted applications like EpiStart, users should always download software from official sources and verify its legitimacy before proceeding with installation. Using “Custom” or “Advanced” settings instead of “Quick” installation allows users to review optional components and decline unnecessary add-ons. Additionally, users should remain cautious while browsing, as intrusive ads often disguise themselves as legitimate content.





