Domain Name Services (DNS) play a crucial role in our IP networks. DNS servers map website names to their corresponding IP addresses. By altering information on a DNS server, you can redirect users to different IP addresses, potentially leading them astray from their intended destinations. One method to achieve this redirection is by modifying files on computers, such as the HOSTS file. This change forces the computer to connect to the IP address specified in the file, bypassing the DNS server query.
Directing someone to a specific IP address becomes simpler when altering the HOSTS file on their machine. However, modifying this file across numerous devices is a challenging task. Consequently, attackers often target the DNS server itself, making a single change that updates the responses for all querying clients. While various methods exist to manipulate DNS servers, most involve gaining control over the server.
What Is DNS and How Do DNS Servers Function?
Let’s revisit what DNS means. The Domain Name System is a foundational internet service that facilitates the conversion of human-readable domain names into machine-understandable IP addresses. Here are some essential components related to DNS:
- IP Address (Internet Protocol): A unique string of numbers assigned to each computer and server on a network, allowing them to locate and communicate with each other.
- Domain: A memorable text name, like “www.google.com,” that corresponds to the IP address of a server, simplifying the process of connecting to websites.
- Domain Name System (DNS): This system translates domain names into IP addresses.
- DNS Servers: These include four types of servers crucial to the DNS lookup process: resolving name servers, root name servers, top-level domain (TLD) name servers, and authoritative name servers. For simplicity, let’s discuss the resolver name server.
- Resolver Name Server: Operating within your system, this server begins the translation process by querying other servers to find the IP address associated with a domain name.
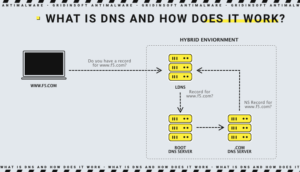
The DNS Lookup Process
When you enter a website’s domain name, the following process unfolds:
- Your web browser and operating system (OS) first attempt to retrieve the domain’s IP address from the computer’s internal memory or cache, if previously visited.
- If the cache doesn’t contain the IP address, the OS reaches out to a resolver name server.
- This resolver then searches through a chain of servers to locate and return the correct IP address to your OS, which relays it to your web browser.
The DNS lookup process is a critical infrastructure component across the internet. However, vulnerabilities in DNS can expose users to security risks, such as malicious redirects, underscoring the importance of awareness and preventive measures.
What is DNS Hijacking?
DNS hijacking, also known as DNS redirection, is a broad term that describes any attack where a perpetrator manipulates an end user’s device into connecting with a fraudulent domain or IP address, under the guise of a legitimate domain. This type of attack can deceive users into thinking they are interacting with a legitimate site when they are not.
There are numerous methods of DNS hijacking, and not all are unlawful. A common legal example is seen with pay-per-use WiFi portals. These services intercept DNS requests before the user has paid for access. Regardless of the user’s settings, all requests direct to a payment server page where the user can purchase WiFi access.
Another prevalent method involves altering the DNS settings on a client’s device. An attacker may change the settings so that the device uses a DNS server under their control instead of a legitimate service like 8.8.8.8. When a user attempts to access a secure site such as their online banking website, the rogue DNS server may redirect them to a fake website. This site acts as a proxy to capture all transmitted data. This technique was famously used by the DNSChanger trojan/malware, which, while now rare, was once a significant threat.
Other hijacking tactics include exploiting vulnerabilities within DNS server software, manipulating DNS registration systems, or utilizing visually deceptive domain names (homograph attacks). One early example of phishing employed a domain named paypaI.com where the letter ‘I’ was capitalized to mimic a lowercase ‘L’, misleading users into thinking it was the legitimate PayPal.com. With DNS now supporting international characters, these attacks have become even more sophisticated and harder to detect.
What is DNS Spoofing
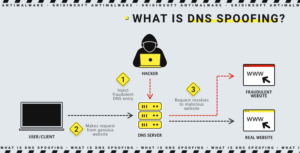
DNS spoofing also refers to any attack that tries to change the DNS records returned to the requester to a response chosen by the attacker. This can include some techniques such as using cache poisoning or some type of man-in-the-middle attack. We sometimes use the terms “DNS hijacking” and “DNS spoofing” as synonyms. This method is also widely used by paid Wi-Fi access points in airports and hotels. In some cases, network security groups can use it as a quarantine tool to isolate an infected device.
Difference Between DNS Spoofing and DNS Hijacking
Although DNS spoofing is often confused with DNS hijacking because both occur at the local system level, they are two different types of attacks. In most cases, DNS spoofing or cache poisoning simply involves overwriting the local DNS cache values with fake ones to redirect the victim to a malicious website. On the other hand, DNS hijacking (also known as DNS redirection) often involves malware infection to hijack this critical system service. In this case, malware hosted on the local computer can change the TCP/IP configuration to point to a malicious DNS server, eventually redirecting traffic to the phishing website.
Conclusion
As you can see, DNS is critical to the day-to-day operation of websites and online services. Unfortunately, attackers may see it as an attractive opportunity to attack your networks. This is why monitoring your DNS servers and traffic is crucial. We must be careful where we go on the Internet and what emails we open. Even the slightest difference, for example, the absence of an SSL certificate, is a signal to check the website you want to visit.