Csrss.exe is an important Windows process, which may sometimes consume a lot of system resources and puzzle the users with such behavior. Some people may mistake it for trojan virus and try to terminate it forcefully. So, is csrss.exe dangerous? And how to fix the issues it creates? Let’s find out.
What is Csrss.exe?
Csrss.exe is a legitimate Windows process with the full name of Client Server Runtime Process and is critical to the system. This process is present in all modern Windows versions, and it is not uncommon to notice several instances running back to back. Such a phenomenon is normal and is not considered a sign of viruses. The system runs one upon the startup, and terminating it leads to BSoD.
This process in Windows 7, 8, and 10 is responsible for console programs, shutdown processes, starting another vital process – conhost.exe – and other critical system functions. It uses a few resources in normal mode, so there is no reason to terminate it. It is needed for System shutdown, Virtual DOS Machine (VDM) support and other system functions such as Ctrl+C and Ctrl+Break signal processing, user switching, and mounting and unmounting disks. As a legacy function, csrss.exe is responsible for opening the console window, but only to the extent of launching the conhost.exe process.
Csrss.exe BSOD – How to Fix?
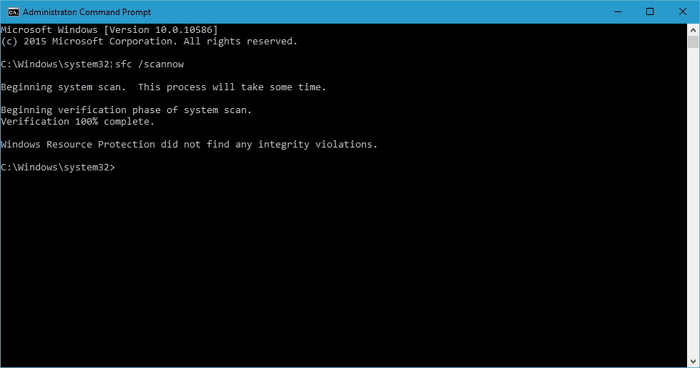
Sometimes, after unsuccessful manipulations with the Csrss.exe file or other system files, the Windows may become unstable or not start. The corruption of important Windows system files can cause this. The solution is as follows:
Go to the Troubleshooting menu – Advanced Options – Command Prompt in the recovery environment. At the command prompt that launches, execute the following command:
sfc /scannow /offbootdir=C:\ /offwindir=C:\Windows
After entering the command, press Enter and wait for the process to complete. This may take some time, but be sure to wait until the end, as it is required to finish the system files’ repair. After that, close the command prompt and restart your computer.
Analysis a Real Trojan Virus
We found several samples of Csrss.exe as Trojan Virus.
They can be downloaded from the Internet by the users themselves. Often when users open unknown files from the spam message, they infect the computer with different kinds of virus-like malware. But the malware developer usually has a plan B. They attach similar viruses to installing various free programs. Hence, if you skip the installation process and don’t look to the advantage setting, then ready that your computer will be infected with a virus-like this.
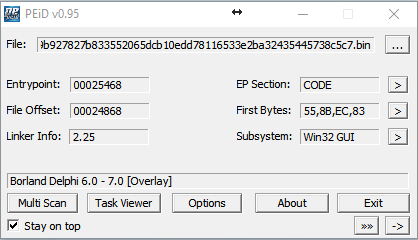
We discovered a sample of Trojan.CoinMiner written in Delphi, which is distributed via spam mail:
GridinSoft Anti-Malware detect it as “Trojan.Win32.CoinMiner.dd”
MD5: 922e0891ae30ac3adb3a09cb963570cc
SHA1: 77feeefff422519cdb63faa438fea87e5e70882a
Other antivirus programs detect Trojan.CoinMiner (csrss.exe) as:
| DrWeb | Trojan.Hosts.6838 |
| Emsisoft | Trojan.Agent.CEQQ (B) |
| ESET-NOD32 | a variant of Win64/BitCoinMiner.AP potentially unsafe |
| Kaspersky | not-a-virus:RiskTool.Win64.BitCoinMiner.cev |
Trojan Miner Drop Files:
C:\Windows\MicrosoftU
Auto.bat
Start.vbs
Start2.vbs
Hide.bat
Start.bat
Start2.bat
1.bat
2.bat
Srvany.exe
Csrss.exe
Srvanyx.exe
After Trojan.CoinMiner has been unpacked. It hides its presence using the strings in Hide.bat, setting the hidden and system attributes to the folder and files.
Attrib C:\Windows\MicrosoftU + S + H / S / D
Attrib C:\Windows\MicrosoftU\*. * + S + H / S / D
Trojan Miner uses the name of one of the system files “csrss.exe” to hide its presence in the system.
Csrss.exe virus starts with the following parameters:
- Stratum + tcp: //xmr.pool.minergate.com: 45560 – Resource for which “mining” will be entered
- [email protected] – user login from whom the extraction will be introduced
- Cryptonight – Mining algorithm
Another parameter is how many threads the program will work in. This “miner” has a formula for calculating the number of processor cores involved. It is in the .bat file that launches the “miner” for the first time:
Set / a CPU =% NUMBER_OF_PROCESSORS% / 2 + 1
Srvanyx -a cryptonight -o stratum + tcp: //xmr.pool.minergate.com: 45560 -u [email protected] -p x -t% cpu%

High CPU & GPU Troubleshooting
If you encounter abnormal GPU and CPU consumption by the csrss.exe process, you should first check the file location. To verify it, right-click on it and select “Open file location“. It should be located at “%SYSTEMROOT%\system32“.
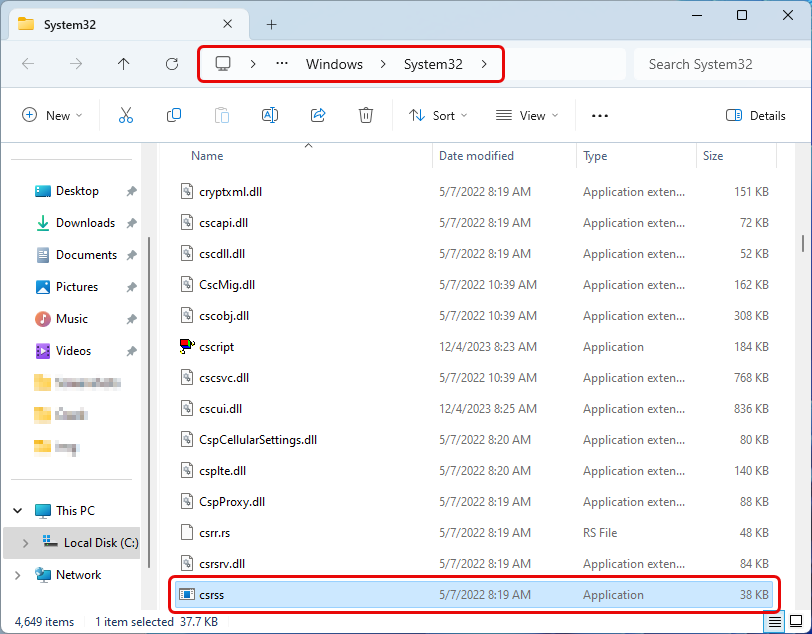
Next, right-click on the file and select “Properties“, then the “Details” tab. This file’s Product Name should be “Microsoft® Windows® Operating System“. Also, the Copyright section should be “© Microsoft Corporation. All rights reserved.”
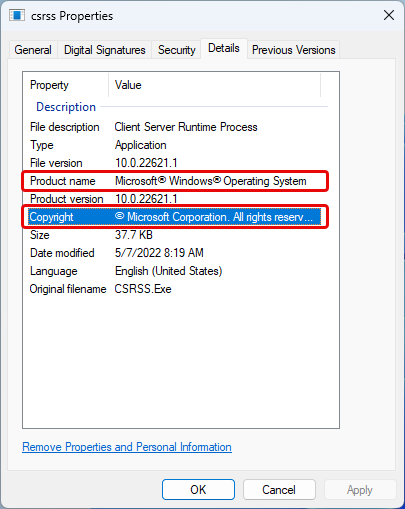
If it is the original csrss.exe file, it may cause a high CPU/GPU load due to incorrect operation of the functions it is responsible for.
The Client Server Runtime Process’s excessive GPU consumption was previously a recognized problem in one of the Windows cumulative updates. However, Microsoft addressed the issue through various updates and hotfixes. You may still be using an older Windows version with this problem. If so, go to the Windows updates section and click “Check for updates“.
The next step is to update your GPU drivers. If you have an Nvidia, open Geforce Experience, and under the “Drivers” tab, click “Check for updates” and follow the instructions. If you have an AMD GPU, check the Radeon software for updates. It is vital to download drivers from official websites. Please avoid using low-trust sites or third-party installers like driver packs.

If the problem persists, run an SFC scan. To do this, run Command Prompt as administrator and paste the “sfc /scannow” command into it.
If the process csrss.exe still loads the device after all the manipulations, you can create a new user profile. To add a new user profile to your PC, go to Settings (gear icon) and select Accounts. Under Family & Other Users, click Add another person to this PC. Choose “I don’t have this person’s sign-in information” and then select “Add a user without a Microsoft account”. Fill in the details and click Next. Remember to grant administrator privileges only to those you trust.
Note: This guide is relevant for users of Windows 10. Windows 11 lacks the option to add a local account and asks you to use a Microsoft account.
Is CSRSS.exe trojan virus?
First, any claim that the “csrss.exe” file located in “C:\Windows\System32\” is a trojan virus is false. Low user knowledge along with unintelligible process names make system process names an excellent option for hiding malware. Usually, the malware tries to infect or disguise itself as critical system processes of the operating system. Also, many viruses use the name of that process or executable file to disguise itself so as not to make you suspicious. Each session creates a separate process, allowing the simultaneous running of several dozen processes.
Nevertheless, it is a good reason to worry if the csrss.exe high CPU and GPU load is constant. But even in this case, there are two options for abnormal process behavior: malware and user profile corruption. The original executable “csrss.exe” file is stored only in one place – in the “C:\Windows\System32\” directory. If only one OS is installed on the device, substituting or overwriting this file in the standard directory is almost impossible.
That being said, finding the files named “csrss.exe” in other directories on your PC is a sign of malware activity. To remove the threat, launch GridinSoft Anti-Malware.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.