The US cybersecurity agency CISA warned about the ongoing exploitation of a critical-severity flaw in Array Networks’ secure access gateway products, including the Array AG and vxAG. Chinese hackers are taking advantage of this vulnerability in Array Networks gateways, which leads to corporations being compromised and their data leaked.
CISA Alerts About Critical Vulnerability Under Active Exploitation
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical advisory urging federal agencies to patch a severe vulnerability. This flaw affects Array Networks AG and vxAG secure access gateways, letting hackers access the network ignoring all the protection measures.
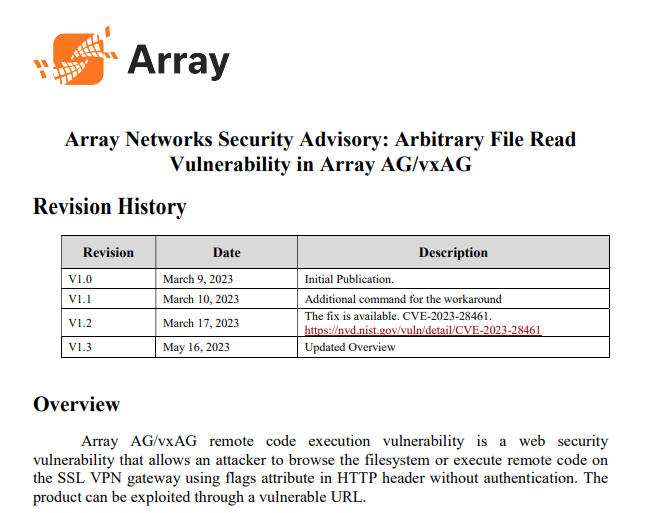
It is tracked as CVE-2023-28461, and has been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog due to confirmed reports of active exploitation. CISA recommends that Federal Civilian Executive Branch agencies apply the fixes by December 16, 2024, to safeguard their networks. Though the same is relevant for all organizations that use Array Networks solutions, as exploitation is highly likely.
The CVE-2023-28461 vulnerability, rated 9.8 on the CVSS scale, stems from missing authentication controls in the software. This flaw allows attackers to execute arbitrary code remotely. Thus, attackers can bypass security mechanisms by exploiting a flaw in how the system processes HTTP headers.
Specifically, they manipulate a “flags” attribute to gain unauthorized filesystem access or execute malicious commands. This vulnerability impacts SSL VPN gateways and critical components of enterprise network security. As the result of a successful exploitation, hackers can get access to the entirety of network, which always ends up badly.
Exploitation In the Wild
This vulnerability exploitation has been linked to Earth Kasha a.k.a MirrorFace, Chinese state-affiliated cyber-espionage group. The group is known for targeting Japanese entities and, more recently, organizations in Taiwan, India, and Europe.
They frequently target sensitive political, industrial, and diplomatic sectors. Earth Kasha’s operations reflect strategic goals aligned with China’s geopolitical interests. The research of real-world exploitation reveals that Earth Kasha is actively exploiting CVE-2023-28461 and other vulnerabilities, namely CVE-2023-27997 in Fortinet FortiOS and CVE-2023-45727 in Proself.
In one of the latest campaigns, Earth Kasha targeted a European Union diplomatic entity to deploy the ANEL backdoor. They used the 2025 Osaka World Expo as a disguise for their emails; the attached files were injecting the backdoor into the systems.
Out of 60 identified cyber groups, 15 Chinese-affiliated actors have exploited at least one of the most frequently targeted flaws. VulnCheck service estimates that over 440,000 internet-facing hosts remain vulnerable, leaving organizations worldwide exposed to potential compromise.
Array Networks addressed the flaw in March 2023 by releasing version 9.4.0.484, which contains the necessary patches. Agencies and organizations using these products should ensure their systems are updated immediately to mitigate potential risks.