Top famous Ransomware hack groups in 2022
Let’s have a look at the bad boys of this year. During…
Texting Spam: How to Stop Spam Text Messages
What does spam mean in texting? Receiving random text messages from unknown…
Difference Between IPSec and SSL
In the last couple of years, remote work has become integral to…
Huge Ransomware List by Gridinsoft Research – Part #2
We talked a lot about notorious ransomware examples in Part #1 of…
Huge Ransomware List by Gridinsoft Research – Part #1
Ransomware is rightfully considered one of the most dangerous types of malware.…
Android Malware. Is Malware on Android Phone Possible?
Android malware is a common name for all malicious software present in…
How Not to Stumble on Scam Websites
Every year, one in ten Americans will be victimized by a scam…
Dangerous WhatsApp Scams You Should Avoid
WhatsApp scams are constantly evolving, and some are difficult to identify. However,…
Spyware Attack: Red Flags You’re Dealing With Spyware
Spyware is probably one of the oldest but most dangerous types of…
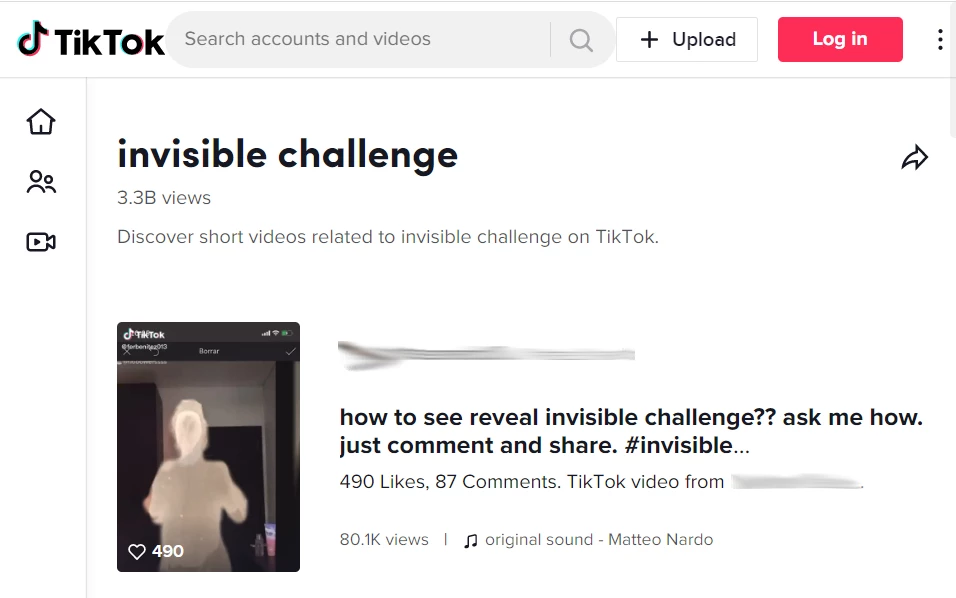
TikTok Invisible Challenge Is Used to Spread Malware
TikTok Invisible Challenge became yet another host for threat actors. Crooks found…
WhatsApp Hacked, Almost 500 Million Users Exposed
On November 28, 2022, information regarding a new WhatsApp breach appeared. The…
Online Dating Scams: How to Avoid Romance Scam
Online dating scammers get you to believe that their fake romances are…