Halloween Shopping Scams — Ways to Detect & Avoid
2023 Halloween, similarly to other holidays and events of this year, will…
WinRAR Vulnerability Allows Arbitrary Code Execution
Over the past few weeks, Google's Threat Analysis Group (TAG) has reported…
VMware Releases Patch for Critical vCenter Server RCE Vulnerability
VMware has released a patch for a critical vulnerability in the vCenter…
1Password Hacked Following the Okta Hack
Recent security breach in the 2FA provider Okta appears to affect some…
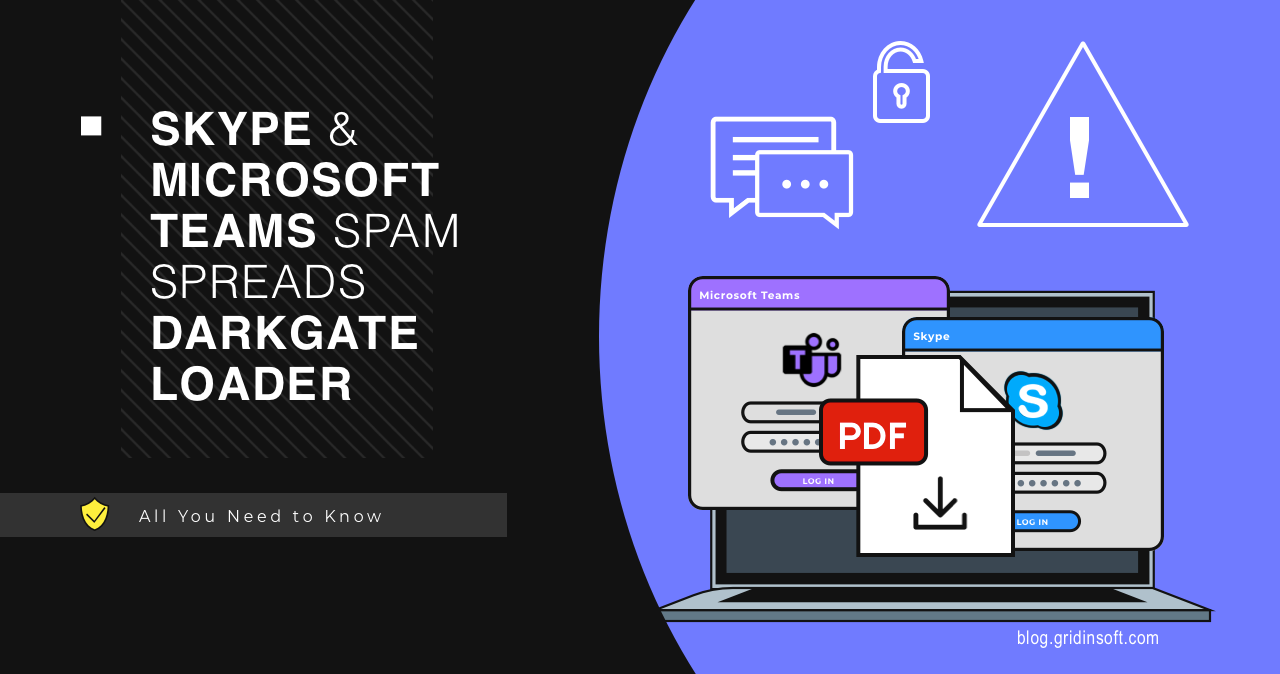
Skype & Microsoft Teams Spam Spreads DarkGate Loader
Over the past few years, DarkGate has been relatively inactive. However, several…
Fake Amazon and Microsoft Tech Support call centers busted
Amazon and Microsoft are partnering with CBI to crack down on multiple…
Ragnar Locker Ransomware Shutdown, Infrastructure Seized
On October 19, 2023, a group of international law enforcement orgs claimed…
Trigona Ransomware Hacked by Ukrainian Cyber Alliance
Trigona ransomware, a novice threat actor active since late 2022, got its…
TOP 10 Most Dangerous Computer Viruses In History
Computer viruses really resemble real ones. They can infect thousands of computers…
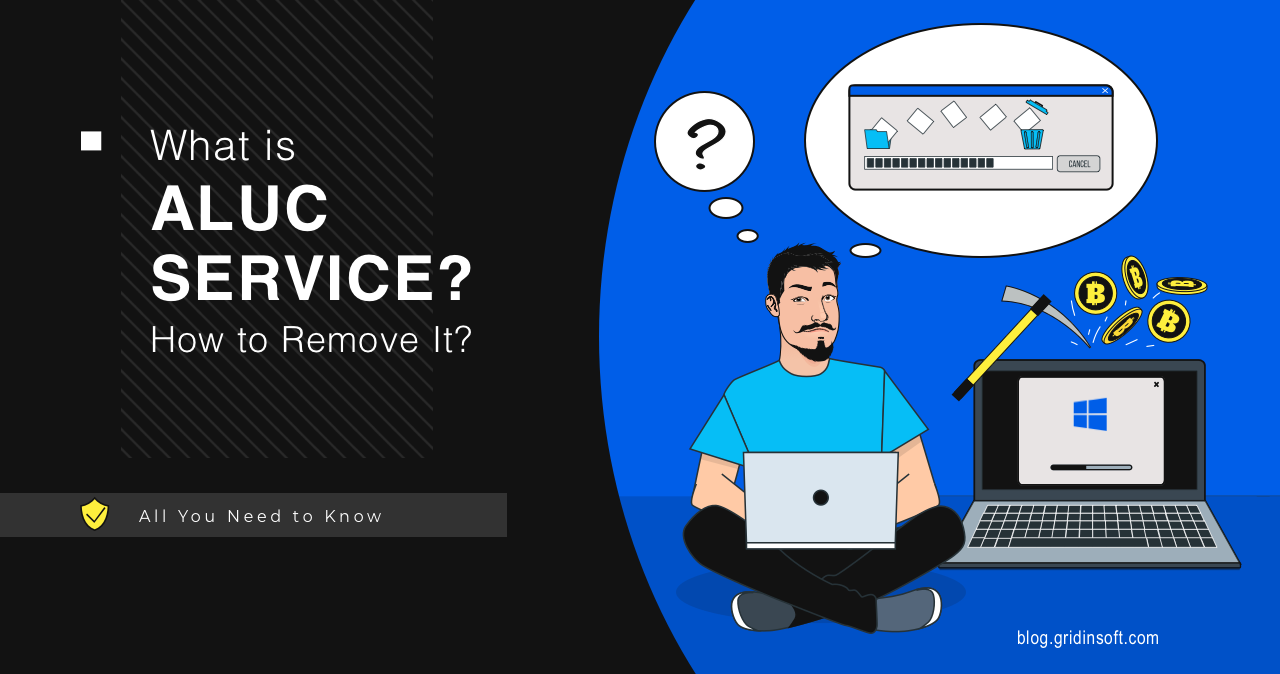
Aluc Service: What Is Aluc Appliaction & How to Remove?
Aluc Service is a strange service you can spectate in the Task…
Exim Vulnerability Allows RCE, No Patches Available
Exim Internet Mailer, a program massively used as a basis for mailing…
Redline and Vidar Stealers Switch to Ransomware Delivery
Cybercriminals who stand behind RedLine and Vidar stealers decided to diversify their…