The Aruba.it email scam is a phishing campaign using fake emails that appear to be from Aruba S.p.A., a well-known Italian company providing domain and web hosting services. Scammers aim to deceive recipients by posing as Aruba and requesting urgent action, such as domain renewal, on a fake website that mimics the official aruba.it page.
Aruba.it Email Scam Overview
The Aruba.it email scam is a phishing attack that exploits the name of Aruba S.p.A., an Italian web hosting and domain registration service. In this scam, fraudsters send fake emails to users, claiming there’s an urgent need to renew their domain with Aruba. The emails look official, often using the Aruba branding, and include a link to a website designed to mimic the real aruba.it login page.
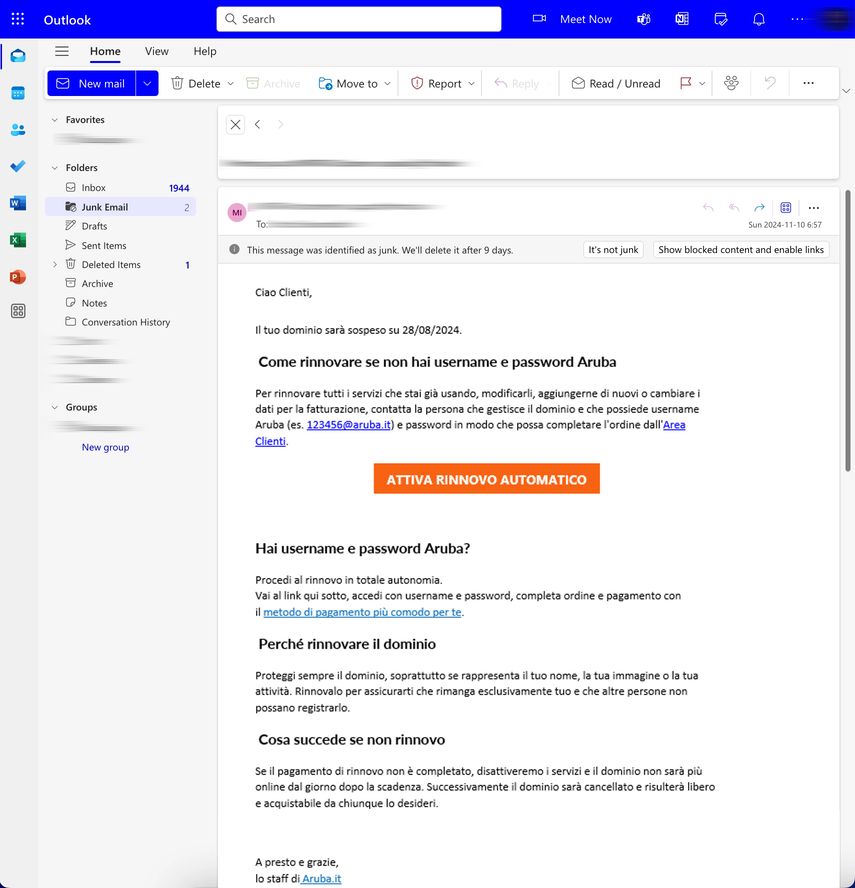
The goal is to trick recipients into entering their login credentials, which the scammers then steal for malicious purposes. It’s a classic phishing scam aimed at getting sensitive information through an email that seemingly comes from a trusted sender. Aruba S.p.A. themselves have no involvement in these emails – it’s just their name is used by scammers to deceive people.
If you receive an email like this, it’s best to ignore and delete it. You can also report a violation using this service. Avoid clicking on any links or providing any information, as the scam is designed solely to steal your data.
Aruba.it Email Scam Variants
This scam comes in at least two flavours, or at least two are well-noticeable forms at the moment of writing this post. Here are their key traits and reasons why they are effective.
Domain expiration warning. The email falsely warns that the recipient’s domain will expire soon, urging them to renew immediately. As such situation threatens website administrators with losing the domain name and going through a lengthy parking process once again, they tend to rush the attached link.
Renewal Issue Notification. Here, the email claims that an automatic renewal attempt was unsuccessful, asking the user to complete the renewal process manually. This is a rather typical issue administrators face in the website maintenance process. The message raises no question so recipients tend to follow the links with little to no doubt.
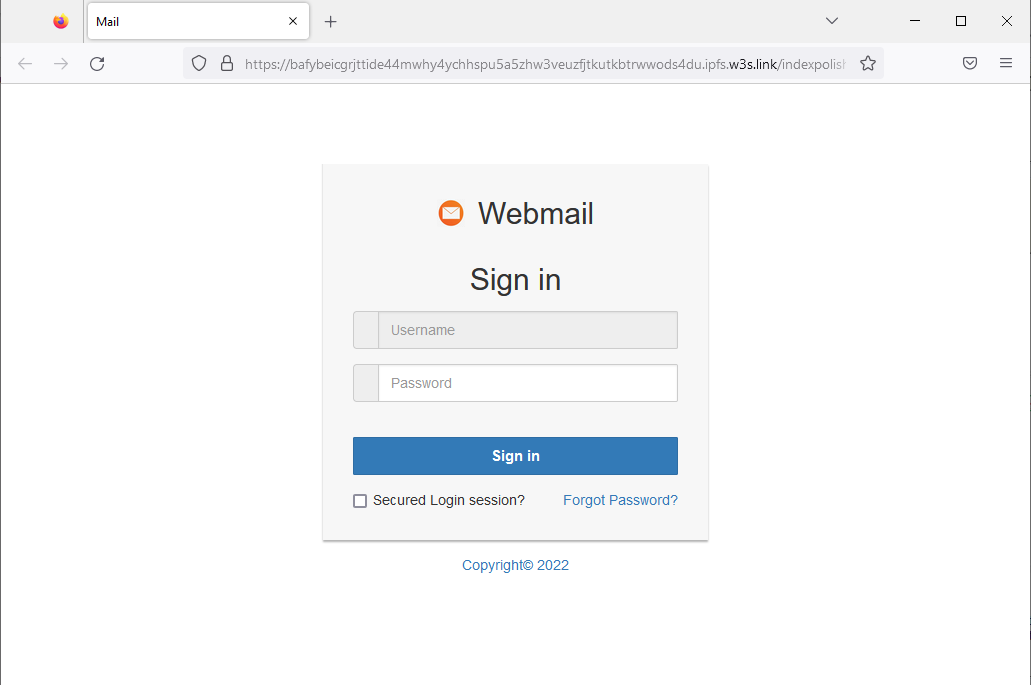
Both versions include a link to a deceptive website, commonly using addresses like aruba-vu[.]com, which closely resembles aruba.it. Though, in a selection of cases attackers don’t even bother with making a website with a similarly-looking URL, and use a completely unreadable one. But the fake site always mirrors the appearance of the official site to trick users into entering their Aruba login credentials.
Purpose of the Scam
The primary purpose of the Aruba.it email scam is to steal users’ login credentials for their Aruba accounts. Once scammers have access to these credentials, they can exploit the stolen data in several ways.
First, they may directly access victims’ email accounts or other associated services, allowing them to monitor personal communications, extract further private information, or take over additional accounts linked to that email. They can also sell this stolen data to other cybercriminals on the black market, who may use it for various forms of cybercrime, such as identity theft or fraudulent purchases.
Second, since many people use the same password across different platforms, scammers can use the compromised credentials to access other online accounts the victim may have, such as social media, banking, or other service accounts. This creates even more opportunities for scammers to cause harm, leading to a wider breach of personal information and potential financial loss for the victim.
Potential Damage
Risks related to Aruba.it scams are vast, though there is one pretty straightforward one. It is about gaining access to the hosting account, which allows attackers to take complete control of the website(s) related to the hijacked account. This can lead to attackers placing malicious code on the site. This code can infect visitors’ devices or redirect users to phishing pages, aiming to steal data.
Additionally, a compromised hosting account grants access to databases that often store users’ personal information, such as names, email addresses, and passwords. This allows attackers to steal this information, leading to data breaches and potential losses for both customers and the site owner. If the account belongs to a corporate site, attackers may also gain access to internal company information.
Another risk involves using the hosting service to send spam, exploiting the reputation of the compromised site. This can lead to the website’s IP address or domain being blacklisted, negatively impacting SEO and damaging the site’s reputation with both search engines and users.
To block any malicious websites from opening, so they can’t harm you in any way, consider using a reliable anti-malware tool with the network protection feature. GridinSoft Anti-Malware offers such protection along with a strong malware removal capabilities. Try it out – just click the banner below.




How can someone make me give credit card information..by texting me over the phone…please let me know