Trojan:Win32/Pomal!rfn is a detection commonly encountered when downloading programs like emulators or games. This heuristic detection, flagged by Microsoft Defender, frequently raises questions about whether it represents a genuine threat or a false positive. This comprehensive guide explains the nature of Trojan:Win32/Pomal!rfn, analyzes its potential risks, and provides detailed removal instructions to ensure your system remains secure.
- What is Trojan:Win32/Pomal!rfn?
- Is Trojan:Win32/Pomal!rfn a False Positive?
- Understanding the Detection Name
- Infection Vectors: How Does Trojan:Win32/Pomal!rfn Spread?
- Technical Analysis of Genuine Trojan:Win32/Pomal!rfn Infections
- How to Remove Trojan:Win32/Pomal!rfn
- Prevention and Protection Strategies
- Frequently Asked Questions
What is Trojan:Win32/Pomal!rfn?
Trojan:Win32/Pomal!rfn is a detection signature used by Microsoft Defender that generally indicates the potential presence of an information-stealing malware. These types of threats are designed to operate covertly on infected systems, harvesting sensitive information such as:
- Login credentials for websites and services
- Cryptocurrency wallet keys and access information
- Banking details and financial account information
- Browsing history and stored cookies
- Personal identity information
- Email account access
Once established on a system, Trojan:Win32/Pomal!rfn typically implements persistence mechanisms to ensure it remains active across system reboots. These techniques include creating registry entries, scheduling automated tasks, or modifying system settings to launch the malware automatically at startup. This persistence enables ongoing data theft over extended periods, often without the user’s awareness.
Although the malware generally operates silently to avoid detection, users might observe symptoms such as degraded system performance, unusual network activity, brief console windows appearing and disappearing rapidly, or unauthorized activities in their online accounts.
Source: Data compiled from security research reports, 2023-2024
Is Trojan:Win32/Pomal!rfn a False Positive?
The Trojan:Win32/Pomal!rfn detection frequently generates confusion because it can sometimes represent a false positive. This occurs primarily because the detection relies on heuristic analysis rather than traditional signature-based methods. Heuristic detection examines program behavior and characteristics rather than matching exact code patterns, which can occasionally flag legitimate software that shares behavioral similarities with known malware.
Numerous users have reported instances where Microsoft Defender incorrectly flagged legitimate game files as Trojan:Win32/Pomal!rfn following Steam updates. Similar cases have been documented on Reddit, where programs hosted on GitHub were repeatedly identified as threats after updates.
| Category | False Positive Indicators | Genuine Threat Indicators |
|---|---|---|
| Source | Legitimate download sources (Steam, GitHub) | Unofficial websites, torrents, suspicious emails |
| Timing | Detection appears after official updates | Detection appears after downloading from untrusted sources |
| Software Type | Game files, emulators, development tools | “Cracked” software, free premium software offers |
| System Behavior | No unusual system activity or performance issues | System slowdowns, strange network activity, unauthorized account access |
| Verification | Checksum matches official release | File size or checksum differs from official version |
Other common examples of false positives include programs such as Roin Simulator, TheoTown, and certain network utilities. When these legitimate applications trigger the Pomal!rfn detection, it’s much more likely to be a false detection requiring appropriate assessment rather than immediate concern.
However, it’s crucial to understand that when the detection is legitimate, Trojan:Win32/Pomal!rfn can operate silently in the background without producing obvious symptoms. This stealth approach means that assuming an infection is non-existent due to the absence of visible issues can lead to serious consequences. Victims often only discover the impact later when they experience unauthorized account access, spam emails sent from their accounts, or stolen cryptocurrency funds.
Understanding the Detection Name
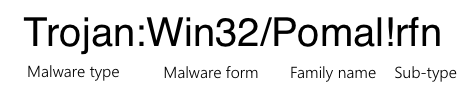
The detection name “Trojan:Win32/Pomal!rfn” follows Microsoft’s naming convention for malware and provides specific information about the threat’s classification. Each component of the name conveys particular details:
- Trojan: Indicates the general category of malware. Trojans are malicious programs that disguise themselves as legitimate software to trick users into installation or execution.
- Win32: Specifies the target platform or operating system. “Win32” refers primarily to 32-bit Windows operating systems, though these threats can also affect 64-bit systems due to compatibility layers.
- Pomal: Represents a generic identifier assigned by Microsoft’s security research team. This label groups malware samples with similar characteristics or behaviors, though the name itself doesn’t describe specific functionality.
- !rfn: Indicates that the detection is based on heuristic analysis rather than a precise, known malware signature. This suffix signals that the identification relies on suspicious behavioral patterns or attributes rather than exact code matching.
Infection Vectors: How Does Trojan:Win32/Pomal!rfn Spread?
Trojan:Win32/Pomal!rfn primarily spreads through several common distribution methods that rely on either user interaction or software vulnerabilities:
Unauthorized Software Sources
The most common infection vector involves downloading software from unofficial or unverified sources. This includes:
- Cracked software and activation tools: Programs that offer paid software for free typically bundle malware as part of the package.
- Pirated games: Unauthorized copies of games often contain modified executable files with embedded malicious code.
- Game emulators from unofficial sources: While legitimate emulators exist, those from questionable sources frequently contain trojans.
- Third-party download sites: Platforms that aggregate software downloads may not verify the security of every file they host.
Phishing and Social Engineering
Trojan:Win32/Pomal!rfn can also spread through targeted or mass phishing campaigns that employ various social engineering techniques:
- Malicious email attachments: Documents that exploit vulnerabilities in office software or contain malicious macros.
- Deceptive download links: Emails or messages that direct users to fake websites hosting the malware.
- Impersonation scams: Communications that appear to come from legitimate organizations or contacts but contain malicious content.
Fake Updates and Software Installers
Another common distribution method involves impersonating legitimate software updates:
- Fake update notifications: Pop-ups or alerts that mimic legitimate software update prompts but deliver malware instead.
- Trojanized installers: Modified versions of legitimate software installers that include additional malicious components.
- Bundled software: Legitimate software that includes optional “extras” that contain malware, often in a way that encourages users to accept the installation without careful reading.
These distribution methods highlight the importance of maintaining cautious online practices and obtaining software only from official, verified sources. Since most infection vectors require some form of user interaction, maintaining awareness and skepticism toward unexpected download prompts or communications serves as the first line of defense against this threat.
Technical Analysis of Genuine Trojan:Win32/Pomal!rfn Infections
When Trojan:Win32/Pomal!rfn represents a genuine infection rather than a false positive, it exhibits several technical characteristics common to information-stealing malware:
System Modifications and Persistence
Once executed, legitimate Trojan:Win32/Pomal!rfn infections implement several persistence mechanisms to ensure they remain active across system restarts:
- Registry modifications: Creating entries in locations such as:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Scheduled tasks: Creating Windows scheduled tasks with random names that execute the malware at specified intervals or system events.
- Startup folder placement: Copying malicious files to the Windows startup folder to ensure execution at login.
- Service creation: Registering as a Windows service with a legitimate-sounding name to blend in with system processes.
Data Collection and Exfiltration
The primary function of Trojan:Win32/Pomal!rfn is to collect sensitive information. The malware typically targets:
- Browser data: Extracting saved passwords, cookies, and browsing history from web browsers including Chrome, Firefox, Edge, and Opera.
- Cryptocurrency information: Seeking wallet.dat files, configuration files for cryptocurrency clients, and credential data for cryptocurrency exchanges.
- System information: Gathering details about hardware, installed software, and user account information to profile the infected system.
- Keystrokes: Some variants implement keylogging functionality to capture credentials entered manually rather than retrieved from storage.
After collection, the malware packages this data and transmits it to command and control (C2) servers using encrypted communications. This exfiltration process often occurs during periods of normal network activity to blend with legitimate traffic, making detection more difficult.
Anti-Analysis Techniques
More sophisticated variants of Trojan:Win32/Pomal!rfn employ various techniques to evade detection and analysis:
- Code obfuscation: Using encrypted or encoded malicious code that only decrypts during execution.
- Virtual machine detection: Checking for the presence of analysis environments and altering behavior if detected.
- Delayed execution: Implementing sleep timers or waiting for specific user actions before activating malicious functions.
- Fileless techniques: Operating primarily in memory to avoid leaving artifacts on the disk that could trigger security software alerts.
These characteristics align with trends observed in modern information-stealing malware, which increasingly prioritizes stealth and persistence over immediate, destructive actions. This approach allows for longer-term data harvesting and potentially greater financial returns for the attackers.
How to Remove Trojan:Win32/Pomal!rfn
When dealing with a potential Trojan:Win32/Pomal!rfn infection, the approach depends on whether you believe the detection is a genuine threat or a false positive. If you’re uncertain, using a third-party security solution provides an effective method for verification and removal if necessary.
Automatic Removal with GridinSoft Anti-Malware
For reliable detection and removal of Trojan:Win32/Pomal!rfn, GridinSoft Anti-Malware offers a comprehensive solution that can identify even sophisticated variants of this threat. This approach is particularly valuable when you’re uncertain whether Microsoft Defender’s detection represents a genuine infection or a false positive.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Manual Verification and Removal Steps
If you prefer to investigate and potentially remove the threat manually, follow these steps carefully. This approach is recommended only for advanced users comfortable with system modification:
- Boot into Safe Mode with Networking: Restart your computer and press F8 during startup to access Advanced Startup Options, then select “Safe Mode with Networking.”
- Verify the detection details: In Windows Security, examine the detection details to identify the specific file location and name associated with the Trojan:Win32/Pomal!rfn alert.
- Assess legitimacy: Research the filename and location online to determine if it’s a known legitimate program commonly flagged as a false positive.
- Check Task Manager: Open Task Manager (Ctrl+Shift+Esc) and look for suspicious processes, particularly those with random names or unusual file locations.
- Examine startup items: Use the System Configuration utility (msconfig) to review startup items for suspicious entries.
- Inspect scheduled tasks: Open Task Scheduler and look for recently created tasks with obscure names or suspicious actions.
- Check registry for persistence: Use Registry Editor to examine common autorun locations:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- Remove malicious components: Delete any identified malicious files and registry entries.
- Reset browsers: Reset all installed browsers to their default settings to remove potential browser extensions or modifications.
- Update all software: Ensure your operating system and all applications are updated to the latest versions to patch potential vulnerabilities.
If you’ve determined the detection is a false positive for legitimate software you’ve intentionally installed from a trusted source, you can add an exclusion in Windows Security to prevent future alerts. However, use this option with caution and only for software you’re absolutely certain is safe.
Prevention and Protection Strategies
Preventing Trojan:Win32/Pomal!rfn and similar threats requires a proactive security approach combining safe computing practices with technical protective measures:
Safe Software Practices
- Download from official sources: Obtain software exclusively from official websites or authorized distribution platforms like the Microsoft Store, Apple App Store, or Google Play.
- Avoid cracked software: Never use “cracked” or pirated software, as these frequently contain malware and provide no legitimate update path or security fixes.
- Verify downloads: Check file hashes or digital signatures when available to confirm software authenticity before installation.
- Read installation screens carefully: During installation, pay close attention to all screens and decline any optional bundled software that wasn’t part of your intended download.
Email and Web Security
- Exercise email caution: Be skeptical of unexpected attachments or links, even from apparently familiar sources.
- Verify sender identities: Confirm the legitimacy of email senders before opening attachments or clicking links, particularly for messages requesting action or information.
- Use email filtering: Enable advanced spam filtering options in your email service to reduce exposure to malicious messages.
- Implement web protection: Consider using browser extensions that block potentially malicious websites and scripts.
System and Security Configuration
- Keep systems updated: Apply operating system and application updates promptly to patch security vulnerabilities that malware might exploit.
- Use a comprehensive security solution: Implement a robust security product that includes real-time protection, heuristic analysis, and behavioral monitoring capabilities.
- Enable User Account Control (UAC): Maintain UAC settings at their default level or higher to receive prompts before programs make changes to your computer.
- Configure macro security: Disable automatic macro execution in office applications or enable them only for trusted documents.
- Implement regular backups: Maintain current backups of important data to minimize the impact of potential security incidents.
By combining these preventative measures with ongoing vigilance, you can significantly reduce the risk of Trojan:Win32/Pomal!rfn infections and similar security threats. Remember that proactive prevention is always more effective than reactive removal after an infection has already occurred.
Frequently Asked Questions
Is Trojan:Win32/Pomal!rfn always a real threat?
No, Trojan:Win32/Pomal!rfn is not always a real threat. This detection is based on heuristic analysis, which examines program behavior rather than specific code signatures. As a result, it sometimes generates false positives for legitimate software, particularly game files, emulators, and development tools. Common false positive scenarios include detections after Steam game updates or when running certain GitHub-hosted applications. However, when the detection is accurate, it typically indicates information-stealing malware capable of harvesting sensitive data from your system.
How can I tell if the Trojan:Win32/Pomal!rfn detection is a false positive?
To determine if a Trojan:Win32/Pomal!rfn detection is a false positive, first consider the source of the file – legitimate software from official sources like Steam or verified developers is more likely to be a false positive. Check if the detection appeared immediately after an official update. Research the specific filename online to see if others report similar false positives. Scan the file with multiple antivirus engines using services like VirusTotal. If you’re still uncertain, using a third-party security solution like GridinSoft Anti-Malware for a second opinion can help verify whether the detection is legitimate or a false alarm.
What information can Trojan:Win32/Pomal!rfn steal from my computer?
When genuine, Trojan:Win32/Pomal!rfn can steal various types of sensitive information including saved browser passwords, autofill data containing personal details, credit card information stored in browsers, cryptocurrency wallet credentials and private keys, session cookies that could enable account takeovers, banking credentials, email account access information, and general system information used to profile your computer. This stolen data is typically transmitted to remote command and control servers operated by attackers, who may use it for identity theft, financial fraud, or sell it to other cybercriminals on underground marketplaces.
Can I safely ignore a Trojan:Win32/Pomal!rfn detection for software I know is legitimate?
You can cautiously ignore a Trojan:Win32/Pomal!rfn detection for software obtained from verifiably legitimate sources if you’re confident it’s a false positive. For additional certainty, verify the software’s digital signature or hash against the developer’s published values, scan with multiple security tools for consensus, and monitor system behavior after allowing the software to run. If you choose to ignore the detection, consider adding a specific exclusion for that file in Windows Security rather than disabling protection entirely. However, exercise extreme caution with this approach and only apply it to software you’re absolutely certain is legitimate.
How can I prevent Trojan:Win32/Pomal!rfn infections?
Prevent Trojan:Win32/Pomal!rfn infections by downloading software exclusively from official sources like developer websites or authorized app stores, avoiding pirated software and activation tools, exercising caution with email attachments and links, keeping your operating system and applications updated with security patches, enabling User Account Control (UAC) to receive prompts before programs make system changes, using comprehensive security software with real-time protection, being skeptical of unsolicited download prompts or update notifications, and implementing regular system backups to protect your data in case of infection.