Hackers found a new way of bypassing the email security filters and anti-malware software – corrupted MS Word documents. As usual, they are attached to email messages with lucrative text, and throw people to phishing sites targeting to steal Microsoft account credentials. It is likely possible to extend the trick to other malware spreading tactics that involve MS Office files.
Phishing with Corrupted Microsoft Word Documents
The most recent campaign, discovered by Any.Run researchers, uses a rather unusual tactic. Hackers corrupt the Word file in a specific manner and wrap it into the classic email phishing campaign. This allows the message to bypass spam filters and get to the receiving end.
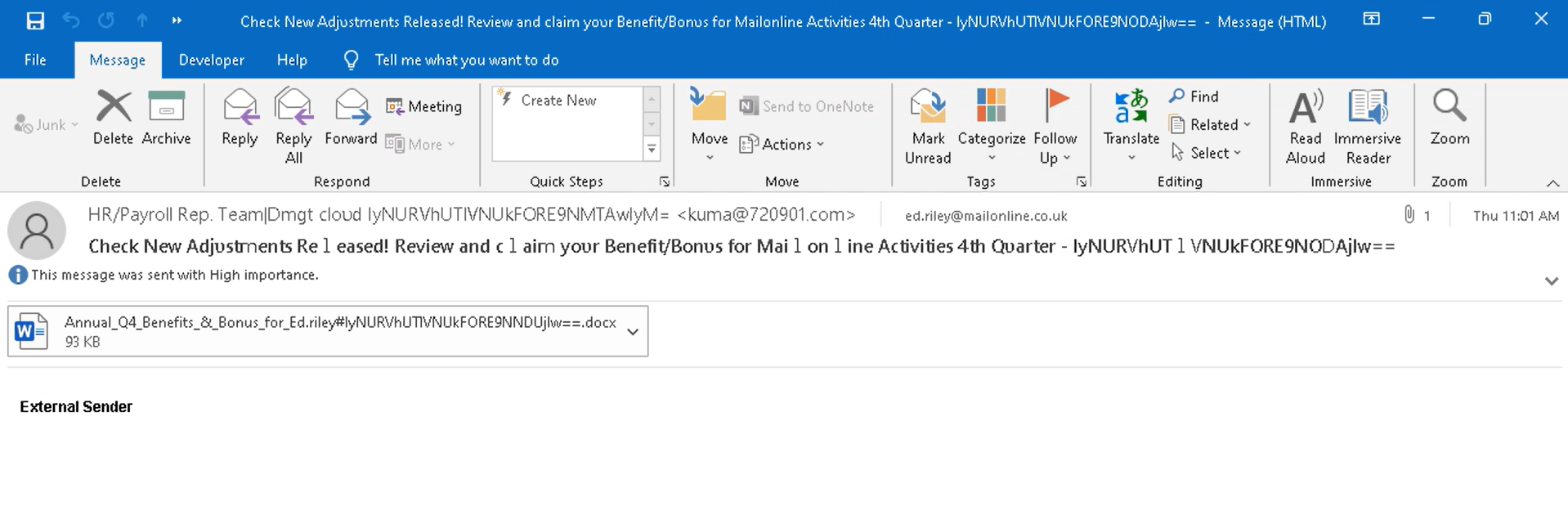
Most of the time, the phishing message pretends to be coming from the user’s employer, about receiving salary bonuses eligible due to the changes in the company’s policy. The attachment is promised to tell more, but when the user tries to open it, they see the message about the file being broken, and an instant offer to recover it.
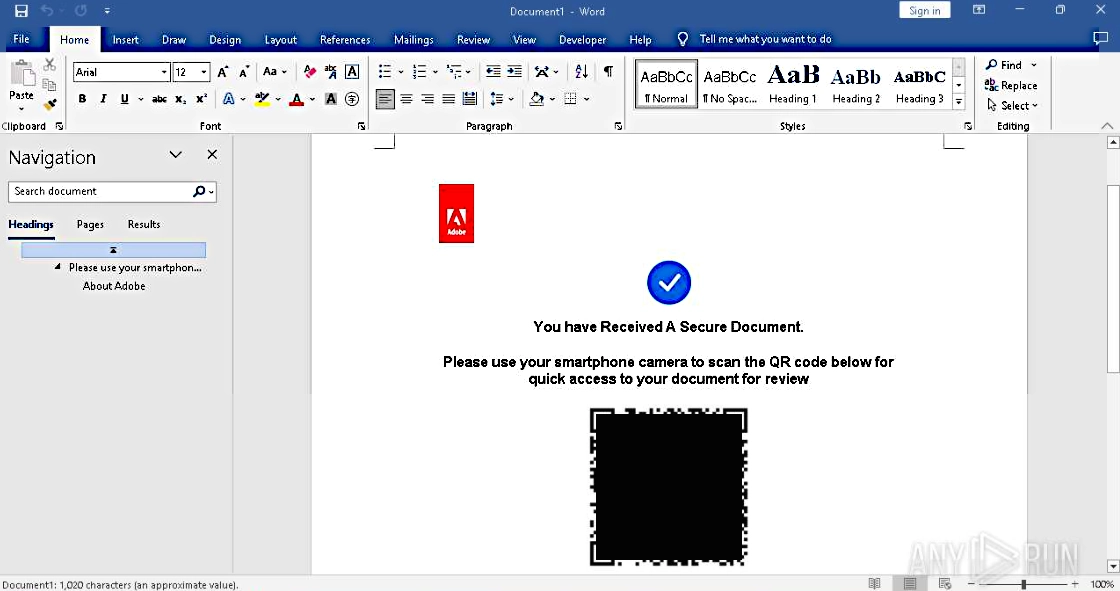
And that is where the main show begins. Attackers corrupt the Word documents only a little bit, so MS Office will be able to recover it and show the contents. At the same time, antivirus programs can’t handle the broken file properly and are stuck on the scanning process.
The file itself contains some generic information about the person being eligible for payroll bonus, and to receive it, they should follow a QR code from below the text. As the code is not interactive, the user expectedly pulls out their smartphone and scans the QR with the camera app. This opens a phishing page pretending to be Microsoft login.
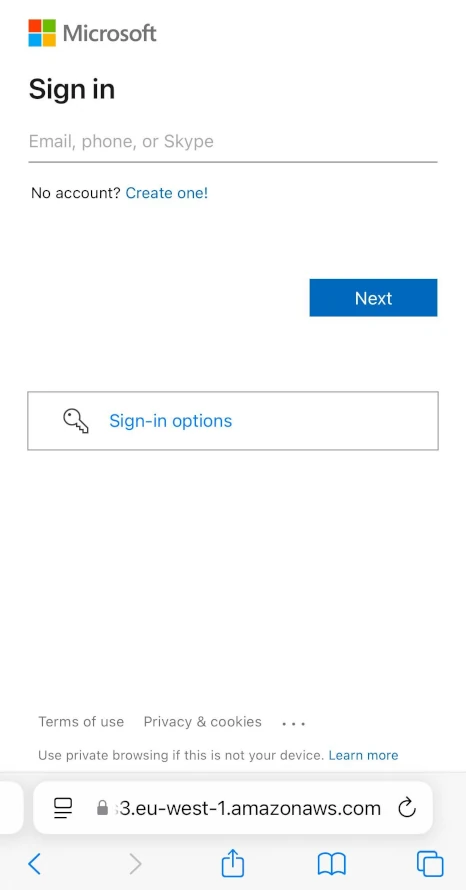
This move with QR code is really smart, as anti-malware software will be able to block the phishing page should the user try opening it. But mobile phones do not have such security solutions, with obvious consequences. The only thing that gives away suspicious origins is URL: it is, expectedly, something totally unrelated to Microsoft.
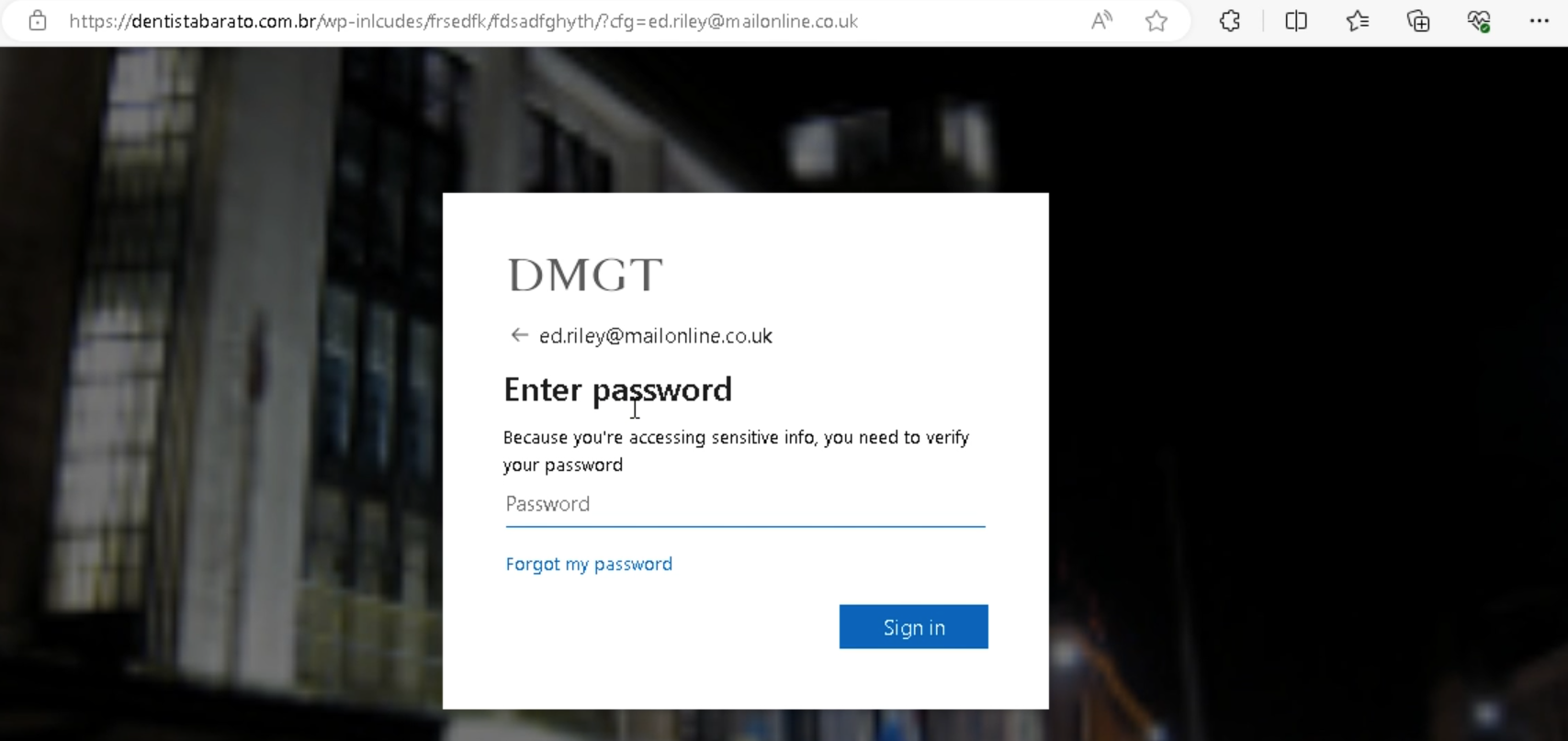
Certain cases of the attack rely both on the QR code and on the link that is opened in the browser the moment after the “recovered” Word documents appear on screen. Though the resulting page is the same – a phishing login page targeting Microsoft accounts.
Hackers also seem to embed personalized links for each user, most likely to improve the legitimate look of the login page. The user’s email is getting embedded into the link before the message is sent, and the phishing site thus contains the address in the login window.
How to Protect Against It?
As the hackers managed to find a loophole in the security mechanisms, relying on them is not an option in that case. That is why one should stay vigilant when dealing with email messages, especially when they feature broken or otherwise fishy files. We have a separate post about recognizing phishing threats that has everything you need to know.
Always pay attention to URL addresses that you type your credentials on. It may look like a real site, even sound like a real one, but be just a well-made copy with malicious intentions. Nonetheless, the website address will never be the same as on the original site, so a quick check here may prevent a lot of problems.