A targeted attack on Chrome extensions publishers compromised the add-ons uploaded to Chrome Web Store, leading to a potential compromise of over 2 million users around the world. This was discovered by Cyberhaven, a cybersecurity company that was hacked and got its extension infused with malicious code. The research of their own hack revealed even more compromised Chrome extensions.
Chrome Extensions Hacked and Infected with Spyware
At the brink of the New Year Eve, California-based cybersecurity company Cyberhaven reported about being compromised. Hackers accessed their internal files through a phishing attack on one of the employees that has publisher access to Chrome Web Store. The attack was likely targeted on this person specifically, and performed on Christmas – at the moment when vigilance is at its minimum.
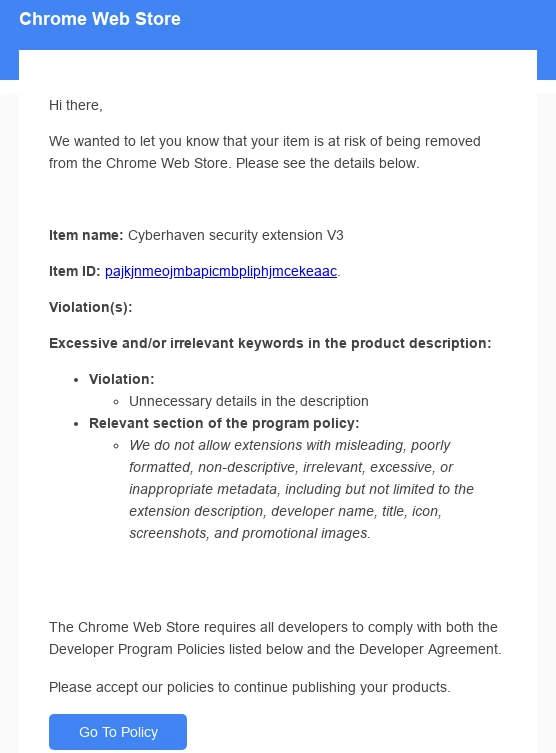
The only thing they did was upload a slightly changed version of the company’s browser extension, executing a supply chain attack. Yet these changes are what made it possible for researchers to uncover the entire campaign going on unnoticed.
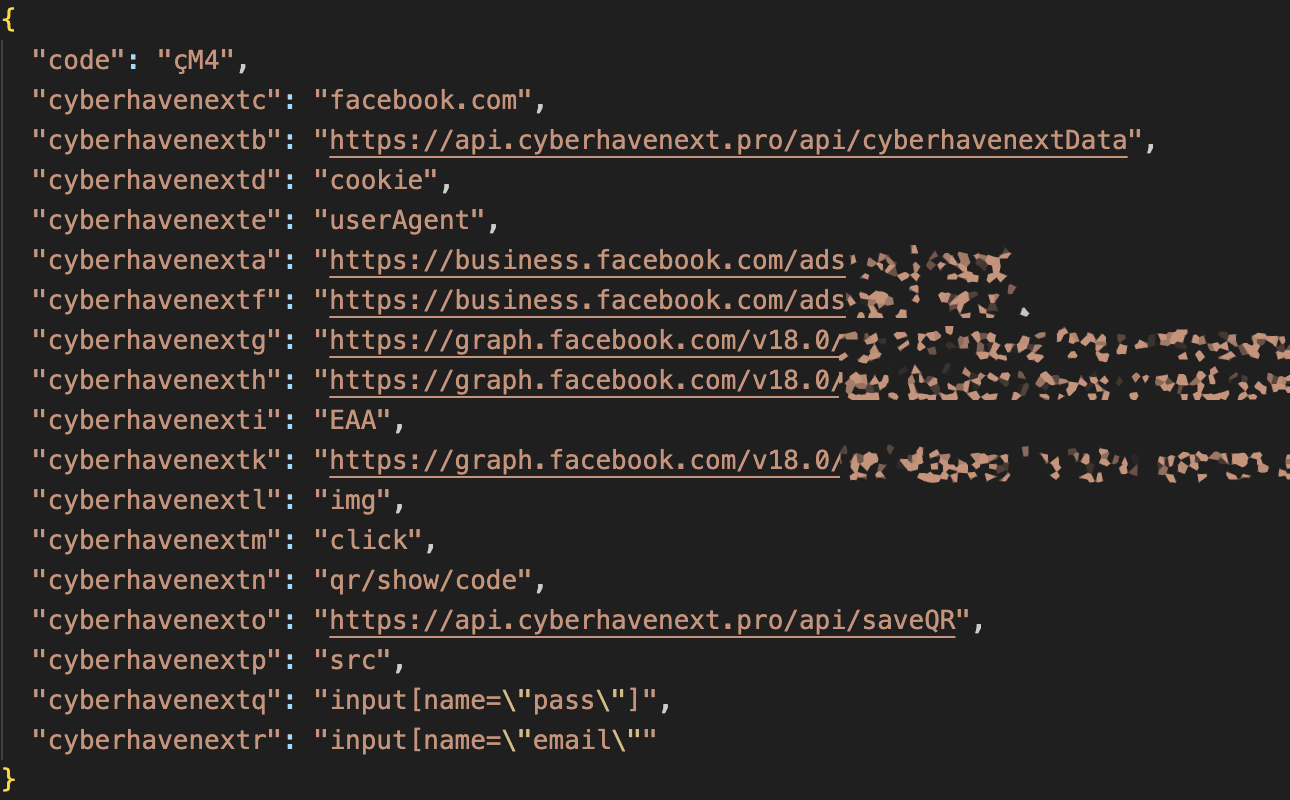
What hackers added were several pieces of malicious code that made the extension connect to the command server – cyberhavenext[.]pro (see our analysis), collect user data from specific websites. Researchers note it being particularly targeted at Facebook business accounts, a behavior we have previously seen in Ducktail infostealer malware.
Data types collected by malicious Chrome extensions
- Facebook user access token
- Facebook user ID
- Account information
- Connected business accounts
- Advertising accounts
Cybercriminals may be interested in Facebook business accounts due to the advertising campaigns that they typically run. Accessing one means putting hands on the image and a credit card linked to the account, meaning that con actors can promote their shady things at the cost of someone else.
25 Compromised Chrome Extensions Discovered
Researchers did not stop on documenting the attack on Cyberhaven and found numerous other Chrome extensions with malicious modifications. They found 25 extensions that have a total of over 2 million users, according to Chrome Web Store data.
List of compromised browser extensions
- AI Assistant – ChatGPT and Gemini for Chrome
- Bard AI Chat Extension
- Email Hunter
- Visual Effects for Google Meet
- Keyboard History Recorder
- Vindoz Flex Video Recorder
- VidHelper Video Downloader
- Earny – Up to 20% Cash Back
- GPT 4 Summary with OpenAI
- Bookmark Favicon Changer
- Search Copilot AI Assistant for Chrome
- Parrot Talks
- AI Shop Buddy
- Sort by Oldest
- Wayin AI
- Reader Mode
- TinaMInd AI Assistant
- VPNCity
- Castorus
- Uvoice
- Internxt VPN
- Rewards Search Automator
- ChatGPT Assistant – Smart Search
- Primus
- Tackker – online keylogger tool
All of the extensions were originally created and uploaded by legitimate companies, yet after being compromised they’ve started to show the exact same behavior as in the case of Cyberhaven. Most likely, all the activity is arranged by the same group of criminals, and through more or less the same infection path.
At the moment, extensions are getting removed from Chrome Web Store, with the corresponding notification in the web browser. Thing is – this alert says nothing about what has happened; the user may have their accounts hijacked, and remain clueless until the visible signs show up. Consider checking the list above for the extensions you may have installed, this can save you a lot of time, effort and money.
One major detail of the overall attack scheme is another Chrome add-on, called Privacy Policy Extension. It is created by hackers, and gets installed after clicking through the steps offered in the phishing email, and carries infostealer functionality. Interestingly enough, it got its listing approved by Chrome Web Store Security after a review, which says a lot about how effective that security is.
How to protect yourself?
Phishing is bad, yet supply chain attacks are even worse. The app may come from a trusted developer, and still deal damage because of hacker activity. In this specific case, only a reliable network security solution could have stopped the malicious activity.
GridinSoft Anti-Malware is equipped with a top-notch network protection module that scans network connections and blocks suspicious activity. It checks both the database of known threats and the properties of the website or server, concluding whether there is any danger to the system. Give it a try by clicking the banner below – there is a 6-day free trial waiting for you.





Great insights! This post is very informative and well-written. Thanks!
I agree, but since I am not “great” with technology, how can I learn more on how to protect my data on internet in a very very simple way ??