New Threat: YourCyanide Ransomware
CMD-based ransomware YourCyanide, currently under development, has been found and analyzed recently by the Trend Micro group of malware researchers. The malware in question does not yet do the data encryption, but it performs almost all the rest of the functionality. Although YourCyanide contains many additional functions, its genealogy hints that the disputed program will mainly be a BTC-extorting cipher, while the other features are secondary.
YourCyanide is a continuation of the GonnaCope – Kekware – Kekpop line of ransomware. It contains a set of sophisticated self-protective measures, which, at one point, even includes a looped command to render a black screen so that the user can’t even access the machine until the malware finishes its setup.
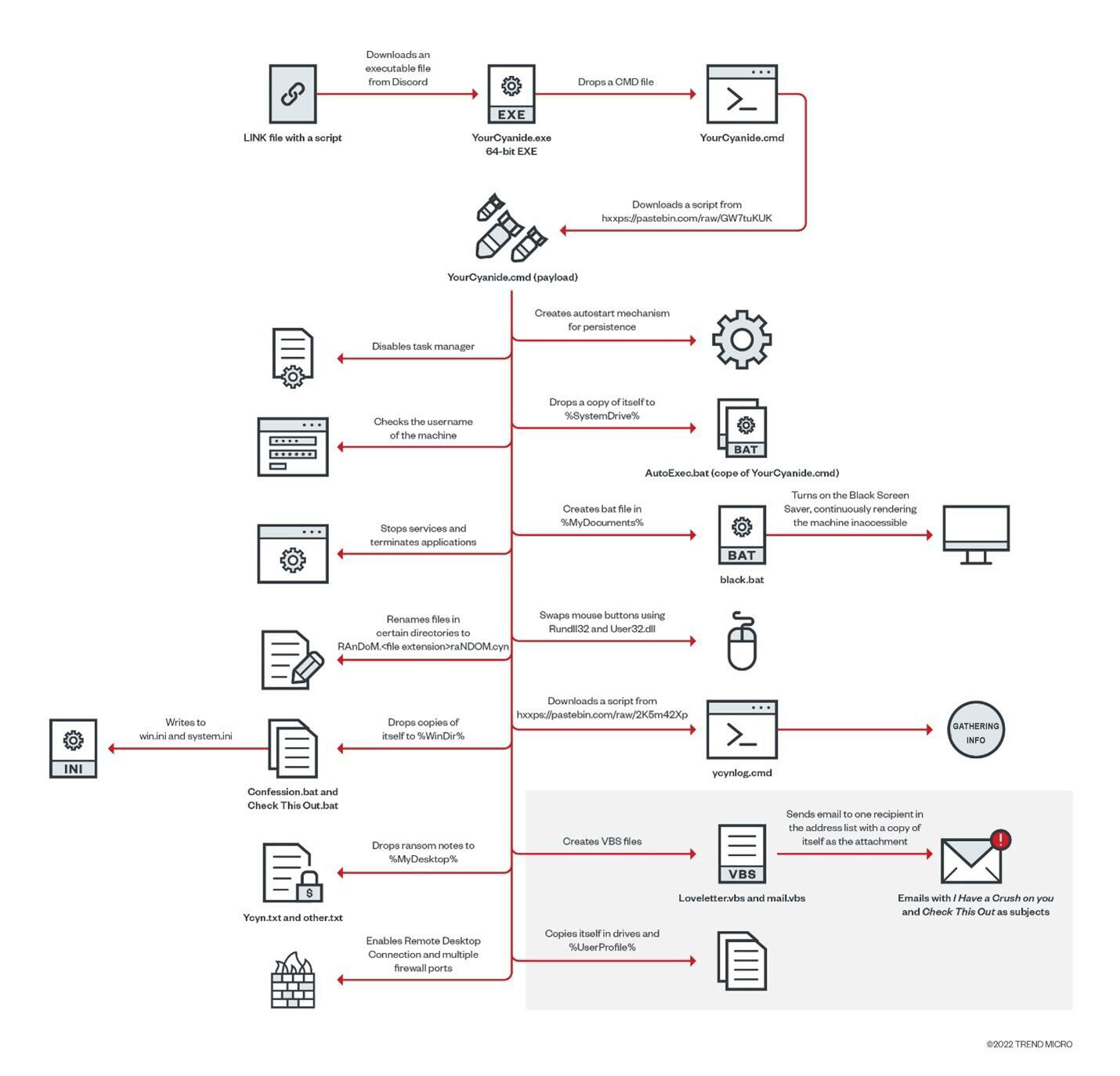
Extra functions include collecting various information: the list of running applications, browser-stored passwords, Minecraft credentials, etc. The data is delivered to the crooks via a Telegram chatbot.
YourCyanide spreads itself over the network via email (watch out for “I have a crush on you” and “Check this out” subjects) and rewrites its copies to all available drives of the victim’s machine.
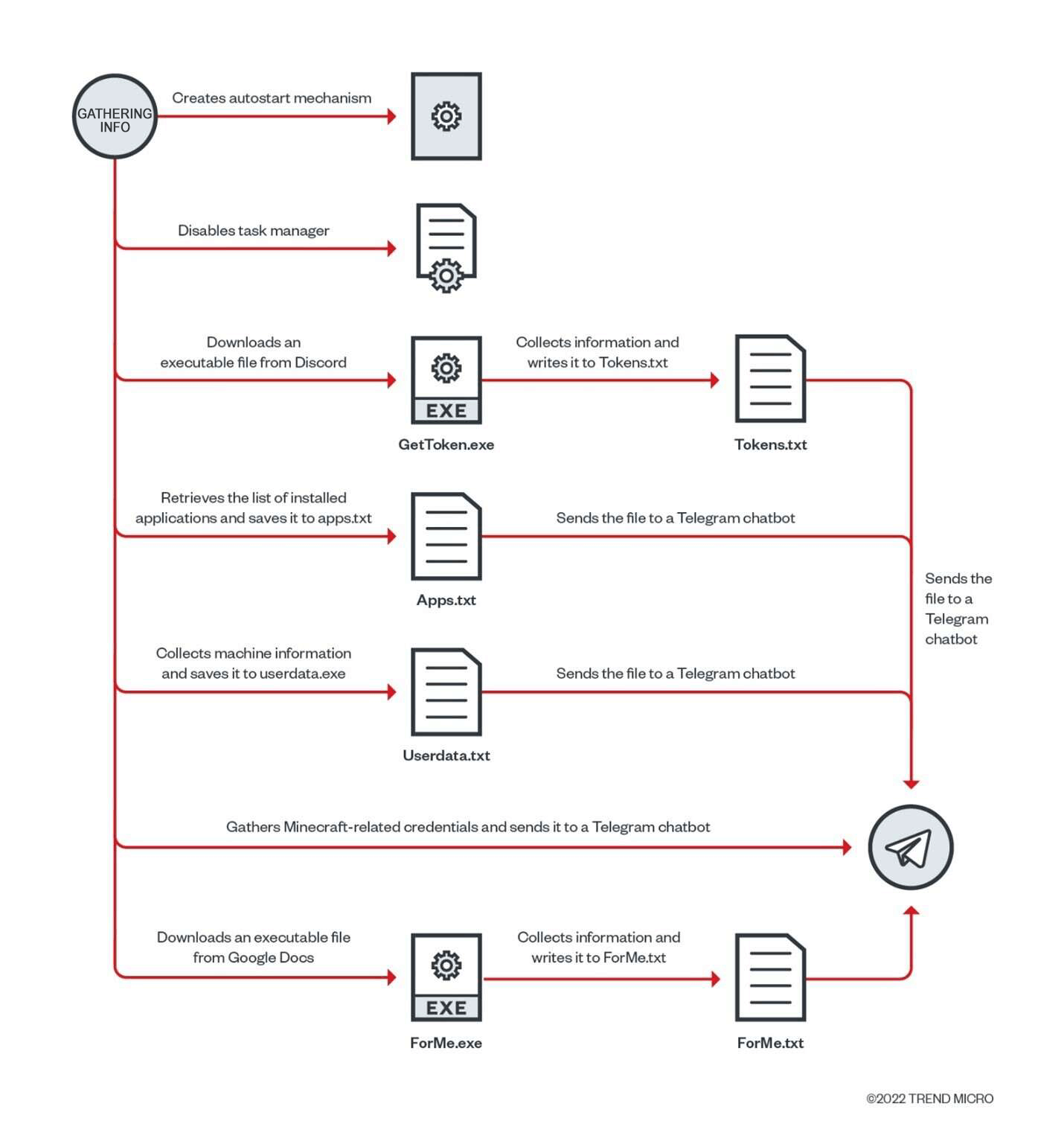
So, it all begins with a *.lnk file (Windows shortcut) with a PowerShell script to download an executable that, in turn, creates and launches a YourCyanide.cmd file containing a script from Pastebin. The subsequent malware unwinding involves multiple obfuscation layers read on the run. The intruder switches off the Task Manager, hinders the user’s attempts to fix anything with a recurring black screensaver, deactivates antivirus systems, and even swaps mouse buttons.
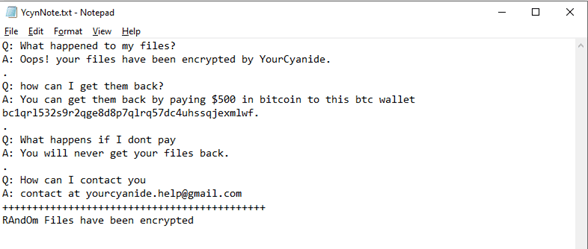
Although the ransomware component of YourCyanide is yet being developed, leaving the ransom note is already a part of the malware actions chain. The targeted files don’t yet get encrypted, but they are renamed to RAnDoM.file extension.raNDOM.cyn. The scanner for new files to be encrypted is seemingly not yet there.
An interesting fact: the developers of this ransomware obviously monitor security experts’ activities, as addresses of certain malware-research sandbox machine names were specified to be avoided. If the machine name matches any of the listed ones, the deployment of ransomware discontinues.




