On January 9, 2024, Avast and Cisco Talos announced the release of a free decryptor for one of the Babuk ransomware variants – Tortilla. Analysts ensure that all the victims of the said threat actor can use the decryptor to get their files back. That is the second ransomware strain to get the decryptor in 2024 – what a start of the year!
Tortilla Ransomware Decryptor Is Available
On January 9, a free decryptor for the Babuk ransomware variant used by Tortilla gang was released. It is the result of a collaboration between Cisco Talos, Avast and Dutch Police. Police operations related to the detainment of key Tortilla group members helped with recovering the original decryptor, which was further used to get the decryption key. Further, Cisco shared this key with Avast Threat Labs, whose Babuk decryptor is now capable of decrypting Tortilla ransomware, too.
After receiving the key, Avast analysts discovered that the pattern they use is in fact the same as in the case of the original Babuk string. This simplified the integration of a new variant into the existing decryptor. Due to the use of a single private key for all victims, there is the possibility of all the victims to get their files back. The updated decryptor is now available on the developer site.
What is Tortilla Ransomware?
Tortilla is a sample of Babuk ransomware that emerged a month after the original malware shutdown in September 2021. Possibly, it is one of the earliest offsprings, as it emerged in October of the same year. Contrary to other Babuk-like ransomware samples, Tortilla almost repeats the original, which made the analysts believe that it is just a continuation of the old group. However, the names for the payload that granted the group the name, pointed at a different actor managing the campaign.
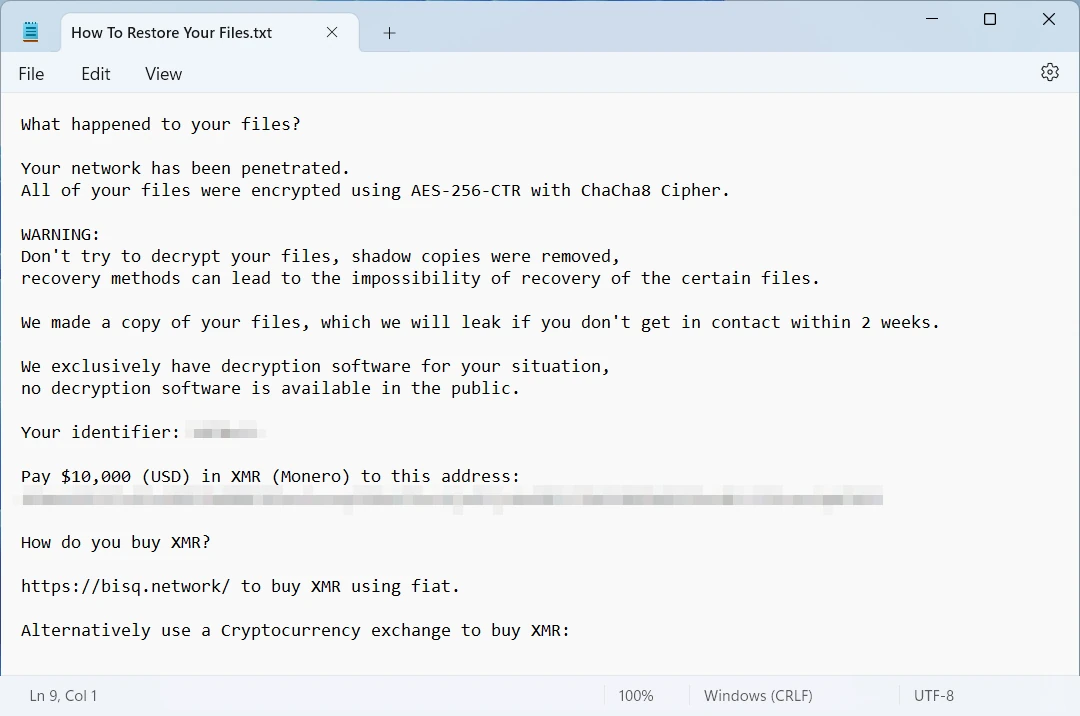
Babuk itself was a prolific ransomware strain, used by the eponymous threat actor in attacks on corporations. Emerged in November 2020 as Vasa Locker, it hacked over a dozen of companies. Everything was ruined by a single post on the Darknet forum in September 2021, when one of the key members leaked the admin panel key and the source code. This made the gang cease further operations. The end? No, the continuous resurface of Babuk code in a number of other ransomware samples, like ESXIArgs and Rorschach.
Can Other Ransomware Samples Get the Decryptor?
As some of the recent events show, it is possible to happen to any ransomware group, both active and defunct. Even prolific groups such as LockBit and BlackBasta are not invulnerable – some of their past samples used vulnerable encryption algorithms and analysts managed to create a decryptor. For defunct groups, especially ones that have their members apprehended, the chance of getting the decryptor is even higher. This once again explains why you hear the advice to avoid paying the ransom: the free decryptor is more possible to appear than you’d think.
Still, the best decision in that case is to avoid ransomware attacks at all. Robust cybersecurity within the perimeter, employee training, vulnerability patching – these steps are much easier and cheaper than solving the consequences of a ransomware attack.





