Over the past few weeks, Google’s Threat Analysis Group (TAG) has reported a worrying trend. Experts have observed government-sponsored actors from different nations exploiting this WinRAR vulnerability as part of their operations. The vulnerability received an index of CVE-2023-38831. Even though a patch has since been released, many users remain vulnerable to potential attacks.
WinRAR RCE Vulnerability Exploited Through a PNG File
In August 2023, RARLabs, the developer of WinRAR, released an updated version that addressed several security-related issues. Among these was the CVE-2023-38831 vulnerability, a logical flaw within WinRAR. This flaw allowed for the unintended expansion of temporary files when processing specially crafted archives. Combined with an idiosyncrasy in the Windows ShellExecute implementation, it posed a significant risk. The vulnerability permitted attackers to run arbitrary code by tricking users into opening a seemingly benign file, such as a standard PNG image, that was contained within a ZIP archive.
According to a detailed report from analysts, this vulnerability had already been exploited in the wild as a zero-day by cybercriminal actors as early as April 2023. Their campaigns targeted financial traders and distributed various commodity malware families. Shortly after this revelation, proof-of-concept and exploit generators were publicly shared on GitHub, leading to an increase in testing activities by financially motivated and advanced persistent threat (APT) actors experimenting with CVE-2023-38831.
How does CVE-2023-38831 work?
This vulnerability hinged on the intricacies of how WinRAR processed archive structures. When a user double-clicked on a seemingly harmless file within WinRAR, it would inadvertently execute a file with the same name but containing a space in its extension. This behavior was caused by a quirk in WinRAR’s file extraction logic, which could lead to the extraction of unintended files into a temporary directory.
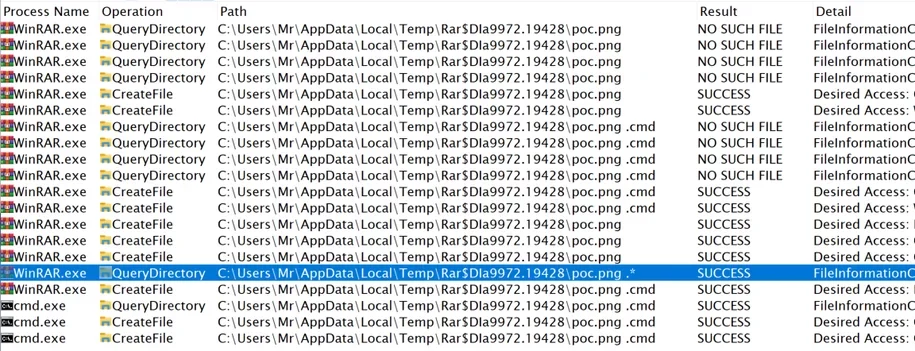
Furthermore, the flaw in the ShellExecute component triggered a search for valid extensions and executed the first file found with an extension matching specific criteria. This behavior allowed attackers to launch malicious code, even if it was not the original file the user intended to open.
Notable Campaigns That Used WinRAR Exploits
The exploitation of CVE-2023-38831 was not limited to one group or country. Various threat actors seized the opportunity to launch campaigns using this vulnerability:
- FROZENBARENTS Impersonates Ukrainian Drone School.
FROZENBARENTS, attributed to Russian Armed Forces’ GRU Unit 74455, targeted the energy sector. They used a lure disguised as an invitation from a Ukrainian drone warfare training school, delivering a malicious ZIP file that exploitedCVE-2023-38831. The payload contained the Rhadamanthys infostealer.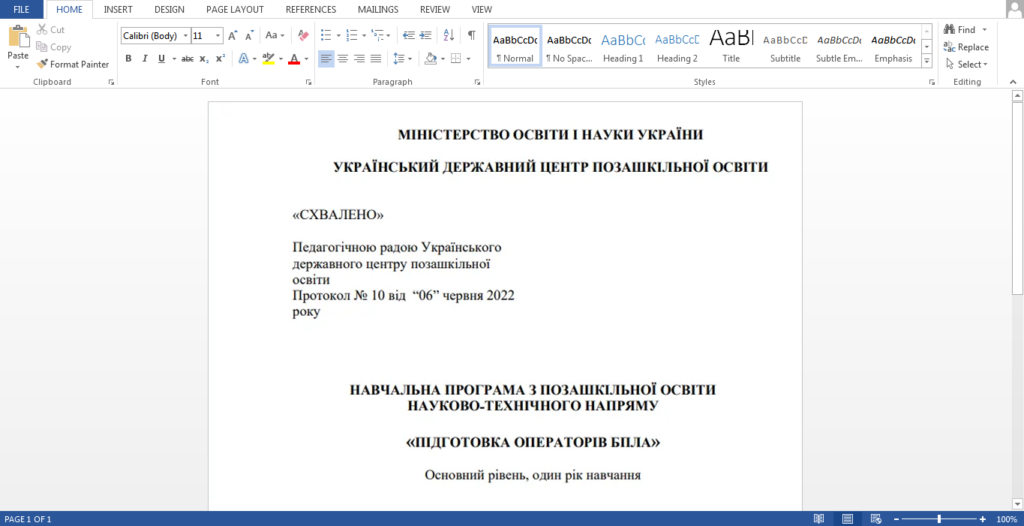
“Training of drone operators” decoy document from FROZENBARENTS campaign - FROZENLAKE Targets Ukrainian Energy Infrastructure.
FROZENLAKE, also attributed to Russian GRU, usedCVE-2023-38831to deliver malware aimed at Ukraine’s energy infrastructure. This campaign redirected users to a site that performed browser checks and initiated the download of an exploit-containing file disguised as an event invitation from a Ukrainian public policy think tank.
FROZENLAKE decoy document impersonating a Ukrainian public policy think tank - ISLANDDREAMS Targets Papua New Guinea.
ISLANDDREAMS, linked to China, exploited the same vulnerability. Their phishing campaign targeted users in Papua New Guinea, delivering an exploit through a malicious ZIP archive and a password-protected decoy PDF document.
Decoy PDF used in ISLANDDREAMS campaign
How do you protect yourself and your organization?
The widespread exploitation of the WinRAR vulnerability underscores the effectiveness of known vulnerability exploits, even when patches are available. This situation highlights the importance of prompt patching and the need for improved user-friendly mechanisms for keeping software secure and up to date.
Here are some key measures to enhance your security:
- It is important to regularly update your operating system, software, and applications, as updates often include security patches to fix known vulnerabilities.
- Establish clear and robust security policies for your organization. Ensure all employees are aware of these policies and adhere to them.
- Conduct regular cybersecurity training and awareness programs for your employees to educate them about threats like phishing and social engineering.
- Be wary of unsolicited emails, messages, and calls. Bypass clicking on suspicious links and refrain from downloading attachments from unknown sources. Ensure requests for personal or financial information are legitimate.
- Use anti-malware software and reputable antivirus to protect your devices from malware and other threats.
- Encrypt your sensitive data, both at rest and during transmission. Encryption helps protect your information from unauthorized access.
It’s important to remember that cybersecurity training should be a constant process rather than a one-time event. As threats become more sophisticated, it’s crucial to continually evaluate and adjust your security measures to stay ahead of potential risks. Collaboration between individuals, organizations, and the broader cybersecurity community is essential to maintaining a safer digital environment.




