Bootkit is a rather unusual and unspoken, though widely used kind of malware. These advanced malware types operate beneath the surface, embedding themselves in a computer’s boot sector, allowing them to activate before the operating system (OS) even starts. But why do they need such a deep integration? And where are they used? Let’s find out.
What is a Bootkit?
A bootkit is a sophisticated type of malware that starts and operates even before the operating system starts – during the boot process. Unlike many other malware types that target software vulnerabilities or user actions, bootkits embed themselves in the system’s boot process, making them exceptionally challenging to detect and remove.
One of the defining characteristics of a bootkit is its ability to load before the operating system (OS) itself. This gives the attacker a significant advantage, as they can intercept and manipulate the boot process, allowing them to gain control over the system even before the user logs in. Being integrated that close to the bare metal also opens the possibility of exploiting kernel-level vulnerabilities and hardware flaws.
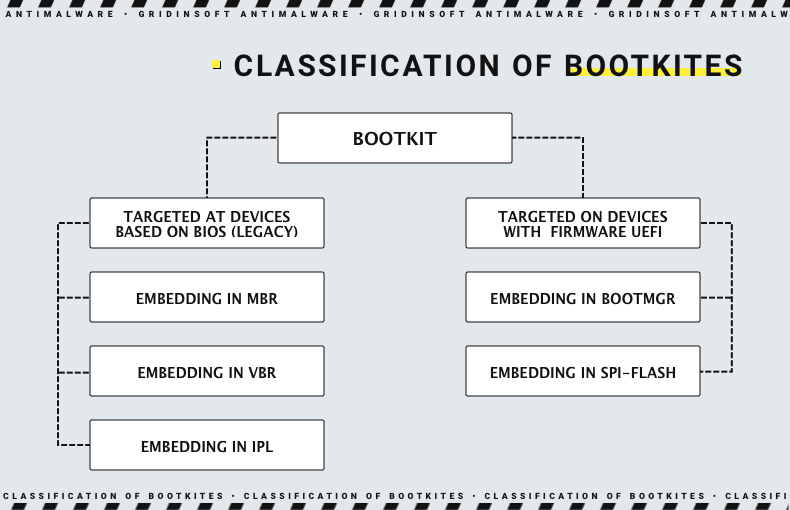
Bootkits vs. Rootkits
While often confused, bootkits and rootkits operate at different levels of a system. Rootkits infect the OS after it loads, granting the max privileges possible to its master. At the same time bootkits are embedded in the system bootloader or even motherboard firmware. This, eventually, changes both the capabilities and the purpose of the bootkit. The two things in common between these two are both being advanced and high-severity threats.
Functionalities of Bootkits
Bootkits are versatile in their malicious functionalities. To understand and combat these malicious entities effectively, we must dissect the intricacies of their functionalities.
- Persistence. One of the primary functionalities of bootkits is their persistence. One of the primary functionalities of bootkits is their persistence. They can implant themselves in the GUID Partition Table (GPT), a more modern system architecture. This positioning allows bootkits to remain active and undetected through system reboots and even full operating system reinstalls, contributing to their prolonged presence and challenging removal from the infected system.
- Data Theft. Some bootkits are engineered to steal sensitive data from the compromised system. During the boot process, they may intercept and exfiltrate data such as login credentials, financial information, personal files, and any other valuable data they can access.
- Backdoor Access. Bootkits can create backdoors within the system, which provide unauthorized remote access to the compromised computer. Adversaries will be able to execute commands, upload additional malware, or manipulate the system as they see fit. It essentially grants them a persistent presence on the compromised device.
- Bypassing security measures. One of the key traits of bootkits is their ability to circumvent security measures. They load themselves into the system’s memory before any security software or antivirus programs have a chance to activate. As a result, they can operate undetected and unimpeded by security tools, allowing them to carry out their malicious activities without being stopped.
Can I detect and remove the bootkit?
Detecting a bootkit before it is injected into the firmware or the first partitions of the hard disk is the most effective way to prevent it from causing damage. However, detecting a bootkit infection is not an easy task, and even if it is detected, removing it can be even more challenging.
If the bootkit has been injected into the EFI partition, only a complete operating system reinstallation can remove the malicious bootkit code from the disk. However, this may not be enough if the malware managed to infect the firmware, which will result in a new system being compromised, too. In such cases, it is advisable to determine which bootkit has infected the system and use special LiveCD antivirus utilities to clean the system of any malicious code.
How to Prevent Bootkits
Preventing bootkit malware requires taking several measures to reduce the risk of infection. Here are some steps that can be taken:
- Secure Boot and UEFI
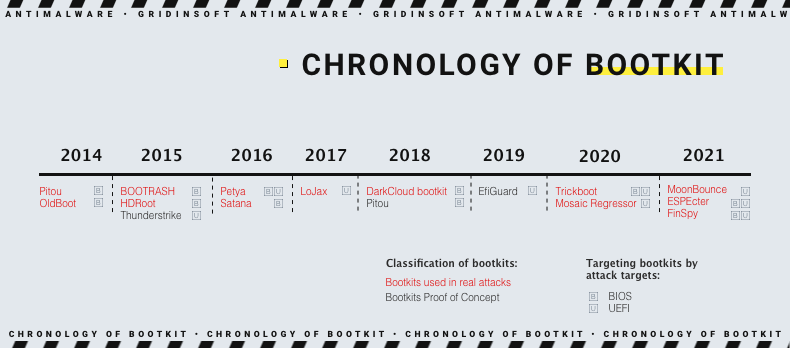
Secure Boot is a feature that is available in UEFI-enabled computers. Its purpose is to ensure that only trusted software is loaded during the boot process. UEFI itself is a more secure and modern technology that allows for a more firm control over the situation. This helps to prevent bootkit malware from infecting the computer. Still, recent developments have shown that the BlackLotus UEFI bootkit can bypass Secure Boot. - Update Your System
Keeping your operating system and security software up-to-date can prevent bootkit malware from infecting your computer. Pay attention to firmware updates as well: although rare, UEFI/BIOS vulnerabilities exist, too, and may be exploited in different scenarios. - Use antivirus software
While antivirus software can’t detect all bootkit malware, it can prevent such an infection in its early stage. Advanced control systems may also be useful for detecting the threats that integrate on such a low level. - Be cautious when downloading software
It is crucial to download software from trusted sources only, especially when we talk about hardware control utilities and drivers. Those two integrate deep enough into the system to allow their exploitation for bootkit injection. - Use a hardware-based solution
Hardware-based solutions, such as a Trusted Platform Module (TPM), can help prevent bootkit malware by ensuring that only trusted software is loaded during the boot process.





