Notorious group known as Water Curupira has unleashed a new wave of threats through their sophisticated malware, Pikabot. This menacing campaign, primarily spread through email spam, highlights an alarming escalation in cyber attacks. It targets unsuspecting victims with deceptive emails, leading to unauthorized access and potential data breaches.
Water Curupira’s Email Spam Campaigns
Water Curupira, one of the known operators behind Pikabot, have been instrumental in various campaigns. It primarily aims at deploying backdoors such as Cobalt Strike, that end up with Black Basta ransomware. Initially involved in DarkGate and IcedID spam campaigns, the group has since shifted its focus exclusively to Pikabot.
Pikabot’s Mechanism
Pikabot operates through two main components, a distinguishing feature that enhances its malicious capabilities. The loader and core module enable unauthorized remote access and execution of arbitrary commands through a connection with a command-and-control (C&C) server.
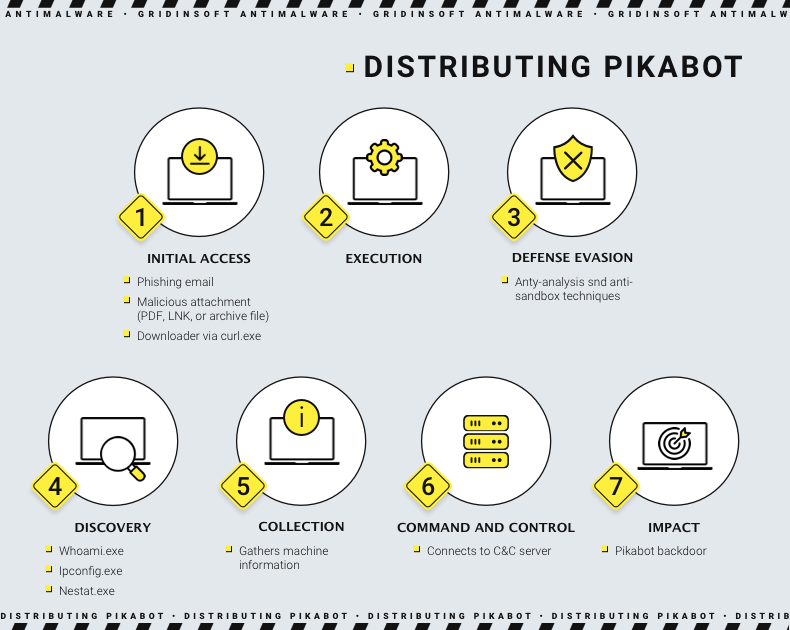
Pikabot’s primary method of system infiltration involves spam emails containing archives or PDF attachments. These emails are skillfully designed to imitate legitimate communication threads. They utilize thread-hijacking techniques to increase the likelihood of recipients interacting with malicious links or attachments. The attachments, designed either as password-protected archives with an IMG file or as PDFs, are crafted to deploy the Pikabot payload.
System Impact
Once inside the target system, Pikabot demonstrates a complex and multi-layered infection process. It employs obfuscated JavaScript and a series of conditional execution commands, coupled with repeated attempts to download the payload from external sources. The core module of Pikabot is tasked with collecting detailed information about the system, encrypting this data, and transmitting it to a C&C server for potential use in further malicious activities.
Another layer of Pikabot mischievous actions is the ability to serve as a loader/dropper. Malware uses several classic techniques, such as DLL hookup and shellcode injection. Also, it is capable of straightforward executable file launching, which is suitable for certain attack cases. Among other threats, Pikabot is particularly known for spreading Cobalt Strike backdoor.
Recommendations
To protect yourself against threats like Pikabot, which is spread by Water Curupira through email spam, here are some key recommendations:
- Always hover over links to see where they lead before clicking.
- Be cautious of unfamiliar email addresses, mismatches in email and sender names, and spoofed company emails.
- For emails claiming to be from legitimate companies, verify both the sender’s identity and the email content before interacting with any links or downloading attachments.
- Keep your operating system and all software updated with the latest security patches.
- Consistently backup important data to an external and secure location, ensuring that you can restore information in case of a cyber attack.
- Educate yourself and your company. Keep up to date with the latest cyber news to stay ahead of the curve.





