If you’re seeing Trojan:Win32/Wacatac.H!ml detected by your antivirus, don’t panic. Your computer might be running slow. The CPU fan won’t stop spinning. You see strange processes eating up system resources. Your files might be locked or encrypted.
This guide will help you remove this threat completely. Follow these step-by-step instructions to eliminate Trojan:Win32/Wacatac.H!ml from your system. We’ll start with methods you can try right now.
| Detection Name | Trojan:Win32/Wacatac.H!ml |
| Threat Type | Trojan Dropper/Loader Malware |
| Primary Function | Downloads and installs additional malware payloads |
| Detection Method | Machine Learning (ML) based heuristic analysis |
| Affected Systems | Windows 10, Windows 11, Windows Server editions |
| Common File Locations | %TEMP%, %APPDATA%, %LOCALAPPDATA%, Downloads folder |
| Typical File Names | Random alphanumeric strings (e.g., hb4h80jb.exe, 4086b4f4db.exe) |
| File Size Range | 50KB – 2MB (varies by payload and packer) |
| Common Sources | Cracked software, keygens, pirated games, email attachments, torrent sites |
| Distribution Methods | Software bundling, malvertising, phishing emails, P2P networks |
| Persistence Methods | Registry Run keys, Scheduled Tasks, Windows Services |
| Network Behavior | Contacts C&C servers, downloads secondary payloads, data exfiltration |
| Typical Payloads | Ransomware, InfoStealers, Banking Trojans, Cryptocurrency Miners |
| System Impact | High CPU usage, slow performance, network spikes, file encryption |
| False Positive Rate | Moderate – ML detection can flag legitimate unsigned executables |
| Risk Level | High – Can deploy ransomware, spyware, and other dangerous malware |
Trojan:Win32/Wacatac.H!ml is Microsoft Defender’s detection name for a family of malware that acts as a dropper. This means it downloads and installs other malicious programs on your computer. The “H!ml” part indicates it was flagged by Microsoft’s machine learning system, which sometimes leads to false positive detections.
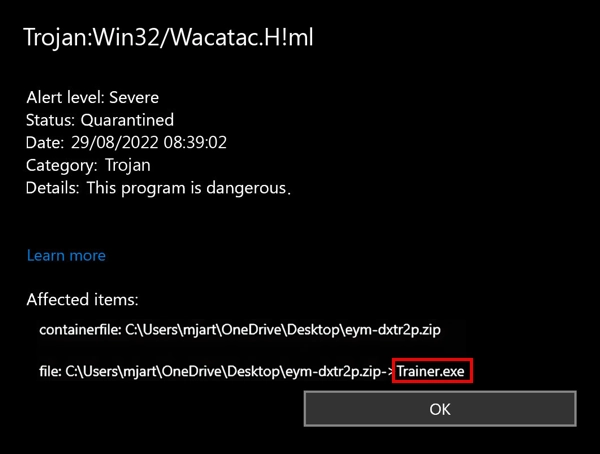
This malware often comes bundled with cracked games and pirated software. Once installed, it performs system fingerprinting to determine what additional malware to deploy. It can install ransomware, information stealing malware, or other threats.
Manual Removal Steps
You can remove Trojan:Win32/Wacatac.H!ml manually by following these steps. Manual removal takes time but gives you complete control over the process.
Step 1: Boot into Safe Mode
Safe Mode prevents malware from running at startup. This makes removal much easier.
- Press Windows key + R to open Run dialog
- Type “msconfig” and press Enter
- Click the “Boot” tab
- Check “Safe boot” option
- Click OK and restart your computer
Step 2: Show Hidden Files and Folders
Malware often hides in system folders. You need to make these visible first.
- Open File Explorer (Windows key + E)
- Click “View” tab
- Check “Hidden items” checkbox
- Click “Options” and select “Change folder and search options”
- Under “Advanced settings,” select “Show hidden files, folders, and drives”
- Uncheck “Hide protected operating system files”
- Click OK
Step 3: Terminate Malicious Processes
Stop any suspicious processes before deleting files. Look for processes with random names or high CPU usage.
- Press Ctrl + Shift + Esc to open Task Manager
- Click “More details” if needed
- Look for suspicious processes with random names like “hb4h80jb.exe” or “4086b4f4db.exe”
- Right-click suspicious processes and select “End task”
- If Windows prevents termination, note the file location for later deletion
Step 4: Delete Malicious Files
Remove malware files from common hiding locations. Check these directories carefully:
- Navigate to C:\Users\[YourUsername]\AppData\Local\Temp
- Delete any recently created suspicious files (.exe, .tmp, .bat files)
- Check C:\Windows\Temp for malicious files
- Look in C:\Users\[YourUsername]\Downloads for the original infected file
- Check these specific files that Wacatac commonly creates:
- FRMCACHE.DAT
- Files with random names ending in .exe
- Temporary batch files (.tmp.bat)
- Empty your Recycle Bin after deletion
Step 5: Clean Registry Entries
Remove malware registry entries that enable persistence. Be careful when editing the registry.
- Press Windows key + R, type “regedit” and press Enter
- Navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Look for entries with suspicious names or random characters
- Delete any entries pointing to files you removed in Step 4
- Check HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Remove similar suspicious entries
- Also check these registry locations:
- HKEY_CURRENT_USER\Control Panel\MMCPL
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Perflib
Step 6: Check Scheduled Tasks
Malware often creates scheduled tasks to maintain persistence on your system.
- Press Windows key + R, type “taskschd.msc” and press Enter
- Expand “Task Scheduler Library” in the left panel
- Look for tasks with random names or suspicious publishers
- Right-click suspicious tasks and select “Delete”
- Pay attention to tasks scheduled to run frequently or at startup
Step 7: Restart and Verify
Restart your computer normally and check if the malware is gone.
- Press Windows key + R, type “msconfig” and press Enter
- Click “Boot” tab and uncheck “Safe boot”
- Click OK and restart normally
- Run Windows Defender full scan to verify removal
- Monitor system performance for any remaining issues
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of Trojan:Win32/Wacatac.H!ml. Professional anti-malware software can find hidden components and registry changes that you might miss.
This approach is especially important for advanced trojan infections that use sophisticated hiding techniques. GridinSoft scans deep into system files and registry entries to ensure complete removal.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Browser Cleanup
If Trojan:Win32/Wacatac.H!ml affected your browsers, you need to clean them thoroughly. This malware can install browser hijackers or modify browser settings.
Remove Malicious Browser Extensions
Check all your browsers for suspicious extensions that might have been installed.
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect browser-based modifications, reset your browser completely:
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
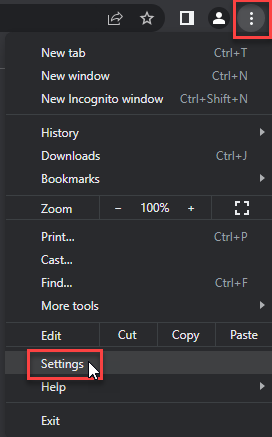
- Choose Reset and Clean up and Restore settings to their original defaults.
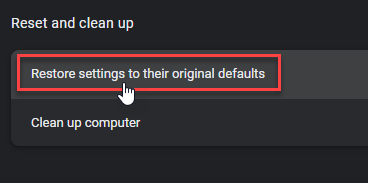
- Tap Reset settings.
Mozilla Firefox
- In the upper right corner tap the three-line icon and Choose Help.
- Choose More Troubleshooting Information.
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
How to Prevent Future Infections
Trojan:Win32/Wacatac.H!ml typically spreads through specific channels. Understanding these helps you avoid future infections.
Avoid Risky Software Sources
Most Wacatac infections come from downloading sketchy software. Cracked games and pirated software are common sources. These files often contain malware bundled with the desired program.
Download software only from official websites or trusted sources. Be especially careful with:
- Keygens and crack files
- Free versions of expensive software
- Game hacks and cheats
- Suspicious email attachments
Keep Your System Updated
Windows updates include security patches that prevent malware infections. Enable automatic updates to stay protected against the latest threats.
Use Real-Time Protection
While some users disable Windows Defender, this leaves you vulnerable. If you must disable it temporarily, re-enable it immediately after completing your task.
Be Cautious with Email
Similar to professional hacker email scams, Wacatac can arrive through malicious email attachments. Never open attachments from unknown senders.
Understanding False Positives
The “ml” in Trojan:Win32/Wacatac.H!ml stands for machine learning. This means Microsoft’s AI system flagged the file as suspicious. Sometimes this results in false positives, especially with:
- Homemade applications without digital signatures
- Development tools and compilers
- Some legitimate software with unusual behavior
- Modified or portable versions of programs
If you’re certain a file is legitimate, you can submit it to Microsoft for analysis. However, be absolutely sure before assuming it’s a false positive. When in doubt, treat the detection as real malware.
Frequently Asked Questions
What is Trojan:Win32/Wacatac.H!ml and why is it dangerous?
Trojan:Win32/Wacatac.H!ml is a dropper malware that downloads and installs other malicious programs on your computer. It’s dangerous because it can deploy ransomware, steal your personal information, or turn your computer into part of a botnet. The malware operates silently in the background while compromising your system security.
How did Trojan:Win32/Wacatac.H!ml get on my computer?
Most commonly, this malware arrives through cracked software, pirated games, or keygens. It can also spread through malicious email attachments, fake software updates, or infected USB drives. Some users get infected when downloading from torrent sites or clicking on suspicious links.
Can I remove Trojan:Win32/Wacatac.H!ml manually?
Yes, you can remove it manually by following the steps in this guide. Manual removal involves stopping malicious processes, deleting infected files, cleaning registry entries, and removing scheduled tasks. However, automatic removal with professional anti-malware software is faster and more reliable.
Is it safe to delete the files Windows Defender detected?
Generally yes, but be careful. If Windows Defender detected Trojan:Win32/Wacatac.H!ml, the files are likely malicious and should be removed. However, this detection sometimes produces false positives with legitimate software. If you’re unsure, scan the files with multiple antivirus programs before deletion.
How can I prevent Trojan:Win32/Wacatac.H!ml in the future?
Avoid downloading cracked software and pirated games. Keep Windows updated with the latest security patches. Don’t open email attachments from unknown senders. Use reputable antivirus software with real-time protection. Be cautious when downloading files from the internet, especially from unofficial sources.
What if manual removal doesn’t work?
If manual removal fails, the malware might have deep system integration or rootkit capabilities. In this case, use professional anti-malware software like GridinSoft Anti-Malware for thorough scanning and removal. You might also need to boot from a rescue disk or seek professional technical support.
Could this be a false positive detection?
Possibly. The “ml” suffix indicates machine learning detection, which can sometimes flag legitimate files as malicious. False positives are more common with homemade applications, development tools, or modified software. If you’re certain the file is legitimate, you can submit it to Microsoft for analysis.
Will this malware steal my personal information?
Trojan:Win32/Wacatac.H!ml can deploy information stealing malware that captures passwords, banking details, and personal files. It might also install keyloggers to record your typing. The specific payload depends on what the dropper downloads, which varies by infection.
Samples of Trojan:Win32/Wacatac.H!ml
- Trojan.Win64.Wacatac.oa!s1: ecf29589944737601c71dc00779f3df5283953b510a37f806929e7d051cb1c2c
- Ransom.Win32.Wacatac.cld: 4e1c027b4c3105063d40ef57e9979a40cb9c72fe6cd54f17d9f3c8ecaece71ae
- Ransom.Win32.Wacatac.cld: 4086d8f9de6fa55b2f10ac83b7f6c0ac0eea3a13c5896274e516582f2d1c6dbe
- Trojan.Win64.Wacatac.oa!s1: 26f5b4590ff9ca791118130b05363b3ad7a438c60cbc032fc812098943640976
- Trojan.Win64.Wacatac.cl: 0e889049525ea2641a817141ddac9dea6525f38381100e753bd24a00523dfbd3
- Trojan.Win32.Wacatac.cl: 9c07ca0022548a9ce4f73684c43353334353d6c6008faa58c7f16b2cc51a9015
- Trojan.Win32.Wacatac.oa!s1: 693b3e2567144e86d590d11892ea297ba90c56a271071347e36fefe56b6838b3
- Trojan.Win64.Wacatac.oa!s1: 04161d5c0396a619409d32814f1c7d8e2e443095112757971f7b23a9c1437de3
- Trojan.Win64.Wacatac.cl: ea5b1d63bbdfe27ceb541674238f0779fc422e273b0972e2bfc7a7de74d8f762
- Trojan.Win32.Wacatac.sa: e48496439a1735812e02a7fd6a6e6a7d9a7a7e0547f31a7f1284770cc50c1a6d
Quick Removal Summary
Fast Removal Steps:
- Boot into Safe Mode to prevent malware from running
- Use Task Manager to stop suspicious processes
- Delete malicious files from Temp folders and Downloads
- Clean registry entries in Run keys
- Remove suspicious scheduled tasks
- Restart and scan with Windows Defender
- For automatic removal, use GridinSoft Anti-Malware
Trojan:Win32/Wacatac.H!ml is a serious threat that requires immediate attention. While manual removal is possible, automatic tools like GridinSoft Anti-Malware ensure complete elimination of all malware components. Remember to avoid cracked software and maintain good security practices to prevent future infections.





